Cisco 350-201 dumps - 100% Pass Guarantee!
Vendor: Cisco
Certifications: CyberOps Professional
Exam Name: Performing CyberOps Using Cisco Security Technologies (CBRCOR)
Exam Code: 350-201
Total Questions: 139 Q&As ( View Details)
Last Updated: Mar 17, 2025
Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates
VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Cisco 350-201 Last Month Results
 98.8% Pass Rate
98.8% Pass Rate 365 Days Free Update
365 Days Free Update Verified By Professional IT Experts
Verified By Professional IT Experts 24/7 Live Support
24/7 Live Support Instant Download PDF&VCE
Instant Download PDF&VCE 3 Days Preparation Before Test
3 Days Preparation Before Test 18 Years Experience
18 Years Experience 6000+ IT Exam Dumps
6000+ IT Exam Dumps 100% Safe Shopping Experience
100% Safe Shopping Experience
350-201 Q&A's Detail
| Exam Code: | 350-201 |
| Total Questions: | 139 |
| Single & Multiple Choice | 126 |
| Drag Drop | 13 |
CertBus Has the Latest 350-201 Exam Dumps in Both PDF and VCE Format
- Cisco_certbus_350-201_by_BButton_123.pdf
- 256.54 KB
- Cisco_certbus_350-201_by_Djala_129.pdf
- 385.68 KB
- Cisco_certbus_350-201_by_Freel4ncer_114.pdf
- 267.97 KB
- Cisco_certbus_350-201_by_Meg_118.pdf
- 262.24 KB
- Cisco_certbus_350-201_by_BOOM_CCNP_115.pdf
- 293.37 KB
- Cisco_certbus_350-201_by_kitcat65_122.pdf
- 300.04 KB
350-201 Online Practice Questions and Answers
An engineer is going through vulnerability triage with company management because of a recent malware outbreak from which 21 affected assets need to be patched or remediated. Management decides not to prioritize fixing the assets and accepts the vulnerabilities.
What is the next step the engineer should take?
A. Investigate the vulnerability to prevent further spread
B. Acknowledge the vulnerabilities and document the risk
C. Apply vendor patches or available hot fixes
D. Isolate the assets affected in a separate network
An engineer receives an incident ticket with hundreds of intrusion alerts that require investigation. An analysis of the incident log shows that the alerts are from trusted IP addresses and internal devices. The final incident report stated that these alerts were false positives and that no intrusions were detected.
What action should be taken to harden the network?
A. Move the IPS to after the firewall facing the internal network
B. Move the IPS to before the firewall facing the outside network
C. Configure the proxy service on the IPS
D. Configure reverse port forwarding on the IPS
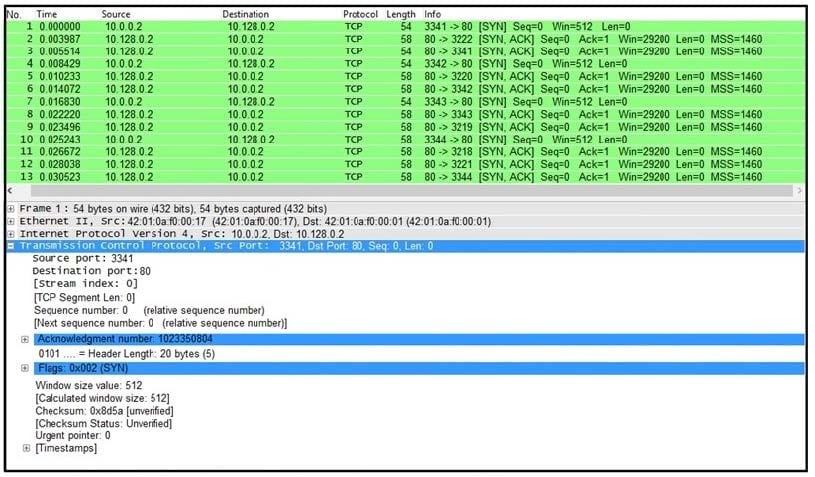
Refer to the exhibit. What is the threat in this Wireshark traffic capture?
A. A high rate of SYN packets being sent from multiple sources toward a single destination IP
B. A flood of ACK packets coming from a single source IP to multiple destination IPs
C. A high rate of SYN packets being sent from a single source IP toward multiple destination IPs
D. A flood of SYN packets coming from a single source IP to a single destination IP
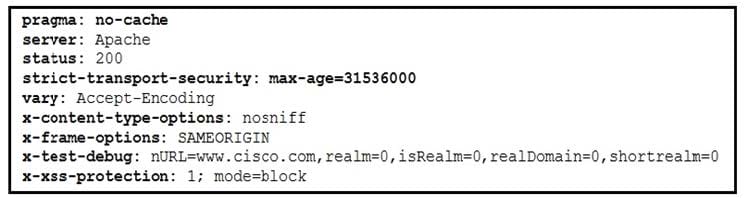
Refer to the exhibit. Where are the browser page rendering permissions displayed?
A. x-frame-options
B. x-xss-protection
C. x-content-type-options
D. x-test-debug
An engineer notices that every Sunday night, there is a two-hour period with a large load of network activity. Upon further investigation, the engineer finds that the activity is from locations around the globe outside the organization's service area. What are the next steps the engineer must take?
A. Assign the issue to the incident handling provider because no suspicious activity has been observed during business hours.
B. Review the SIEM and FirePower logs, block all traffic, and document the results of calling the call center.
C. Define the access points using StealthWatch or SIEM logs, understand services being offered during the hours in question, and cross-correlate other source events.
D. Treat it as a false positive, and accept the SIEM issue as valid to avoid alerts from triggering on weekends.
Add Comments
Success Stories
- United States
- Lloyd
- Mar 22, 2025
- Rating: 4.5 / 5.0
![]()
This 350-201 exam dump is useful and helpful, I also introduced it to my good friend. Now, we passed the exam together. Thanks for this dumps.
- Pakistan
- Keeley
- Mar 21, 2025
- Rating: 4.8 / 5.0
![]()
Valid material !! I will continue using this material and introduced it to other friend. Good thing should be shared with friend.
- Ghana
- Rock
- Mar 21, 2025
- Rating: 4.7 / 5.0
![]()
took the exams yesterday.dumps are valid. almost all of the multiple-choice came out. I advice know ur material very well and then U can read dumps. good success
- Quebec
- Marshall
- Mar 20, 2025
- Rating: 5.0 / 5.0
100% valid. Passed my exam yesterday. I got a new question about Network access control. I can’t remember the question exactly. I’m sure I answered that question correctly because I pass my exam with the full score. It seems that is the only new question I got in the real exam. Anyway, I passed my exam. really a great dumps! I strongly recommend this to all candidates who need to take the exam but do not have much time to prepare for that. You really need to have a try.
- India
- Abbie
- Mar 19, 2025
- Rating: 4.5 / 5.0
![]()
I passed my exam this morning. I prepared with this dumps two weeks ago. This dumps is very valid. All the questions were in my exam. I still got 2 new questions but luckily they are easy for me. Thanks for your help. I will recommend you to everyone I know.
- Pakistan
- Lloyd
- Mar 17, 2025
- Rating: 4.3 / 5.0
![]()
this dumps is valid. All questions that I met in the exam are from this dumps !!!
- United States
- Tony
- Mar 17, 2025
- Rating: 4.8 / 5.0
![]()
yes, i passed the exam in the morning, thanks for this study material. Recommend.
- United States
- Little
- Mar 16, 2025
- Rating: 5.0 / 5.0
![]()
The BEST resource to use for the exam. I passed on the first try! And read this from cover to cover! Extremely readable and clearly defines the intended of the exam. I also recommend using all the on line extras and getting the additional questions on mobile phone for quick review during downtime.
- Canada
- Pin
- Mar 14, 2025
- Rating: 4.2 / 5.0
![]()
Thats it for this exam! Gave my test today and passed. Thank to the site. All the best!
- Assmus Estate
- Alma
- Mar 13, 2025
- Rating: 5.0 / 5.0
Really recommend this dumps. The questions are update and answers are accurate. Prepare for my exam with this material only and passed my exam yesterday. I met 2 new questions in my actual exam. Never mind. They are not so easy and I think I answered that correctly.
Cisco 350-201 exam official information: This exam tests your knowledge and skills related to core cybersecurity operations, including fundamentals, techniques, processes, and automation.


 Printable PDF
Printable PDF