350-201 Online Practice Questions and Answers
The physical security department received a report that an unauthorized person followed an authorized individual to enter a secured premise. The incident was documented and given to a security specialist to analyze. Which step should be taken at this stage?
A. Determine the assets to which the attacker has access
B. Identify assets the attacker handled or acquired
C. Change access controls to high risk assets in the enterprise
D. Identify movement of the attacker in the enterprise
According to GDPR, what should be done with data to ensure its confidentiality, integrity, and availability?
A. Perform a vulnerability assessment
B. Conduct a data protection impact assessment
C. Conduct penetration testing
D. Perform awareness testing
A SOC team is informed that a UK-based user will be traveling between three countries over the next 60 days. Having the names of the 3 destination countries and the user's working hours, what must the analyst do next to detect an abnormal behavior?
A. Create a rule triggered by 3 failed VPN connection attempts in an 8-hour period
B. Create a rule triggered by 1 successful VPN connection from any nondestination country
C. Create a rule triggered by multiple successful VPN connections from the destination countries
D. Analyze the logs from all countries related to this user during the traveling period
A security architect is working in a processing center and must implement a DLP solution to detect and prevent any type of copy and paste attempts of sensitive data within unapproved applications and removable devices. Which technical architecture must be used?
A. DLP for data in motion
B. DLP for removable data
C. DLP for data in use
D. DLP for data at rest
An engineer wants to review the packet overviews of SNORT alerts. When printing the SNORT alerts, all the packet headers are included, and the file is too large to utilize. Which action is needed to correct this problem?
A. Modify the alert rule to "output alert_syslog: output log"
B. Modify the output module rule to "output alert_quick: output filename"
C. Modify the alert rule to "output alert_syslog: output header"
D. Modify the output module rule to "output alert_fast: output filename"
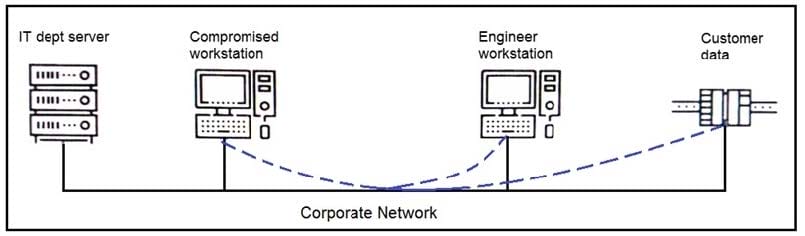
Refer to the exhibit. An engineer received a report that an attacker has compromised a workstation and gained access to sensitive customer data from the network using insecure protocols. Which action prevents this type of attack in the future?
A. Use VLANs to segregate zones and the firewall to allow only required services and secured protocols
B. Deploy a SOAR solution and correlate log alerts from customer zones
C. Deploy IDS within sensitive areas and continuously update signatures
D. Use syslog to gather data from multiple sources and detect intrusion logs for timely responses
A customer is using a central device to manage network devices over SNMPv2. A remote attacker caused a denial of service condition and can trigger this vulnerability by issuing a GET request for the ciscoFlashMIB OID on an affected device.
Which should be disabled to resolve the issue?
A. SNMPv2
B. TCP small services
C. port UDP 161 and 162
D. UDP small services
What is a benefit of key risk indicators?
A. clear perspective into the risk position of an organization
B. improved visibility on quantifiable information
C. improved mitigation techniques for unknown threats
D. clear procedures and processes for organizational risk
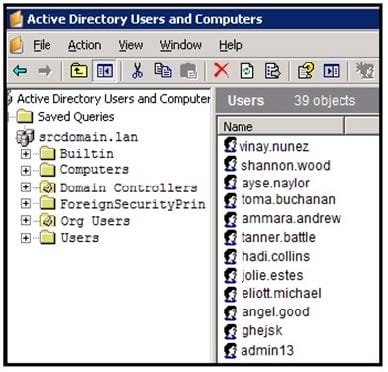
Refer to the exhibit. An engineer is investigating a case with suspicious usernames within the active directory. After the engineer investigates and cross-correlates events from other sources, it appears that the 2 users are privileged, and their creation date matches suspicious network traffic that was initiated from the internal network 2 days prior.
Which type of compromise is occurring?
A. compromised insider
B. compromised root access
C. compromised database tables
D. compromised network
What is needed to assess risk mitigation effectiveness in an organization?
A. analysis of key performance indicators
B. compliance with security standards
C. cost-effectiveness of control measures
D. updated list of vulnerable systems
An engineer received an incident ticket of a malware outbreak and used antivirus and malware removal tools to eradicate the threat. The engineer notices that abnormal processes are still occurring in the system and determines that manual intervention is needed to clean the infected host and restore functionality. What is the next step the engineer should take to complete this playbook step?
A. Scan the network to identify unknown assets and the asset owners.
B. Analyze the components of the infected hosts and associated business services.
C. Scan the host with updated signatures and remove temporary containment.
D. Analyze the impact of the malware and contain the artifacts.
A SOC analyst detected a ransomware outbreak in the organization coming from a malicious email attachment. Affected parties are notified, and the incident response team is assigned to the case. According to the NIST incident response handbook, what is the next step in handling the incident?
A. Create a follow-up report based on the incident documentation.
B. Perform a vulnerability assessment to find existing vulnerabilities.
C. Eradicate malicious software from the infected machines.
D. Collect evidence and maintain a chain-of-custody during further analysis.
Which action should be taken when the HTTP response code 301 is received from a web application?
A. Update the cached header metadata.
B. Confirm the resource's location.
C. Increase the allowed user limit.
D. Modify the session timeout setting.
An engineer received multiple reports from users trying to access a company website and instead of landing on the website, they are redirected to a malicious website that asks them to fill in sensitive personal data. Which type of attack is occurring?
A. Address Resolution Protocol poisoning
B. session hijacking attack
C. teardrop attack
D. Domain Name System poisoning
A SOC team receives multiple alerts by a rule that detects requests to malicious URLs and informs the incident response team to block the malicious URLs requested on the firewall. Which action will improve the effectiveness of the process?
A. Block local to remote HTTP/HTTPS requests on the firewall for users who triggered the rule.
B. Inform the user by enabling an automated email response when the rule is triggered.
C. Inform the incident response team by enabling an automated email response when the rule is triggered.
D. Create an automation script for blocking URLs on the firewall when the rule is triggered.
