EC-COUNCIL 212-82 dumps - 100% Pass Guarantee!
Vendor: EC-COUNCIL
Certifications: EC-COUNCIL Certifications
Exam Name: EC-Council Certified Cybersecurity Technician (C|CT)
Exam Code: 212-82
Total Questions: 102 Q&As ( View Details)
Last Updated: Mar 19, 2025
Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates
VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
EC-COUNCIL 212-82 Last Month Results
 99.6% Pass Rate
99.6% Pass Rate 365 Days Free Update
365 Days Free Update Verified By Professional IT Experts
Verified By Professional IT Experts 24/7 Live Support
24/7 Live Support Instant Download PDF&VCE
Instant Download PDF&VCE 3 Days Preparation Before Test
3 Days Preparation Before Test 18 Years Experience
18 Years Experience 6000+ IT Exam Dumps
6000+ IT Exam Dumps 100% Safe Shopping Experience
100% Safe Shopping Experience
212-82 Q&A's Detail
| Exam Code: | 212-82 |
| Total Questions: | 102 |
| Single & Multiple Choice | 102 |
CertBus Has the Latest 212-82 Exam Dumps in Both PDF and VCE Format
- EC-COUNCIL_certbus_212-82_by_Fabiano_Rigon_92.pdf
- 225.74 KB
- EC-COUNCIL_certbus_212-82_by_Qazax_93.pdf
- 225.82 KB
- EC-COUNCIL_certbus_212-82_by_Gajendra_Singh_82.pdf
- 226.34 KB
- EC-COUNCIL_certbus_212-82_by_Marcio_Silva_91.pdf
- 242.18 KB
- EC-COUNCIL_certbus_212-82_by_Napoleon_98.pdf
- 225.92 KB
- EC-COUNCIL_certbus_212-82_by_Dan_Malone_87.pdf
- 229.42 KB
212-82 Online Practice Questions and Answers
The IHandR team in an organization was handling a recent malware attack on one of the hosts connected to the organization's network. Edwin, a member of the IHandR team, was involved in reinstating lost data from the backup media. Before performing this step, Edwin ensured that the backup does not have any traces of malware. Identify the IHandR step performed by Edwin in the above scenario.
A. Eradication
B. Incident containment
C. Notification
D. Recovery
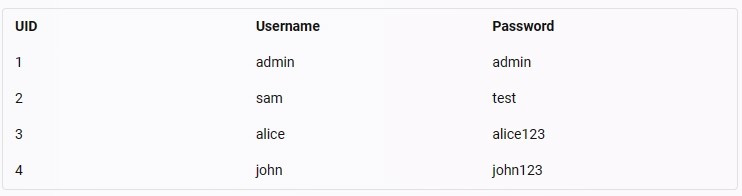
A web application www.movieabc.com was found to be prone to SQL injection attack. You are given a task to exploit the web application and fetch the user credentials. Select the UID which is mapped to user john in the database table.
Note: Username: sam Pass: test
A. 5
B. 3
C. 2
D. 4
Matias, a network security administrator at an organization, was tasked with the implementation of secure wireless network encryption for their network. For this purpose, Matias employed a security solution that uses 256-bit Galois/Counter Mode Protocol (GCMP-256) to maintain the authenticity and confidentiality of data.
Identify the type of wireless encryption used by the security solution employed by Matias in the above scenario.
A. WPA2 encryption
B. WPA3 encryption
C. WEP encryption
D. WPA encryption
Karter, a security professional, deployed a honeypot on the organization's network for luring attackers who attempt to breach the network. For this purpose, he configured a type of honeypot that simulates a real OS as well as the applications and services of a target network. Furthermore, the honeypot deployed by Karter only responds to pre-configured commands.
Identify the type of Honeypot deployed by Karter in the above scenario.
A. Low-interaction honeypot
B. Pure honeypot
C. Medium-interaction honeypot
D. High-interaction honeypot
George, a security professional at an MNC, implemented an Internet access policy that allowed employees working from a remote location to access any site, download any application, and access any computer or network without any restrictions. Identify the type of Internet access policy implemented by George in this scenario.
A. Permissive policy
B. Paranoid policy
C. Prudent policy
D. Promiscuous policy
Add Comments
Success Stories
- Turkey
- BAHMAN
- Mar 21, 2025
- Rating: 4.6 / 5.0
![]()
About 3 questions are different, but the remaining is ok for pass. I passed successfully.
- British Columbia
- Warren
- Mar 21, 2025
- Rating: 5.0 / 5.0
This dumps was introduced by my room mate several month ago. He took the exam at that time. I don't think it will help me a lot. But when I found many new questions that I never found from other study materials, i begun to pay more attention on this dumps. Finally I cleared the exam with almost full score. Thanks for this dumps. Really appreciate.
- Greece
- Lara
- Mar 20, 2025
- Rating: 5.0 / 5.0
![]()
Dump is valid. Thanks for all.
- Turkey
- Baines
- Mar 18, 2025
- Rating: 4.6 / 5.0
![]()
dumps is valid.
- United Kingdom
- Bath
- Mar 18, 2025
- Rating: 4.5 / 5.0
![]()
Valid, around 3 questions are different, d & g different as well,rest are fine
- United Kingdom
- Vicky
- Mar 16, 2025
- Rating: 4.8 / 5.0
![]()
A very helpful study material, I have passed the exam with the help of this dumps. So i will introduce this dumps to other friend.
- United Kingdom
- King
- Mar 15, 2025
- Rating: 4.4 / 5.0
![]()
hi guys, thanks for your help. I passed the exam with good score yesterday. Thanks a million.
- United States
- Jack
- Mar 14, 2025
- Rating: 4.3 / 5.0
![]()
This dumps is still valid. Just took my CCNA today and passed it. Every question i got on the test was in the dumps.
- India
- Ziad Z from Jordan
- Mar 14, 2025
- Rating: 4.1 / 5.0
![]()
I just passed my exam by using this dumps, thanks to thier efforts which help to get the certificates in easy way.
- Turkey
- Bakery
- Mar 14, 2025
- Rating: 4.8 / 5.0
![]()
there are 4 questions different. these are about t.shoot questions. but the rest is ok for pass. Good dumps.
EC-COUNCIL 212-82 exam official information: Boost your Cybersecurity career with Cyber Security Technician training. Enroll to CCT certification and upgrade to a Certified Cybersecurity Technician.


 Printable PDF
Printable PDF