SY0-601 Online Practice Questions and Answers
Which of the following is the MOST secure but LEAST expensive data destruction method for data that is stored on hard drives?
A. Pulverizing
B. Shredding
C. Incinerating
D. Degaussing
An enterpnse has hired an outside security firm to facilitate penetration testing on its network and applications. The firm has agreed to pay for each vulnerability that ts discovered. Which of the following BEST represents the type of testing that is being used?
A. White-box
B. Red-leam
C. Bug bounty
D. Gray-box
E. Black-box
Which of the following controls would be the MOST cost-effective and time-efficient to deter intrusions at the perimeter of a restricted, remote military training area?(Select TWO).
A. Barricades
B. Thermal sensors
C. Drones
D. Signage
E. Motion sensors
F. Guards
G. Bollards
A security analyst is working on a project to implement a solution that monitors network communications and provides alerts when abnormal behavior is detected
Which of the following is the security analyst MOST likely implementing?
A. Vulnerability scans
B. User behavior analysis
C. Security orchestration, automation, and response
D. Threat hunting
An organization has expanded its operations by opening a remote office. The new office is fully furnished with office resources to support up to 50 employees working on any given day. Which of the following VPN solutions would BEST support the new office?
A. Always On
B. Remote access
C. Site-to-site
D. Full tunnel
Accompany deployed a WiFi access point in a public area and wants to harden the configuration to make it more secure. After performing an assessment, an analyst identifies that the access point is configured to use WPA3, AES, WPS, and RADIUS. Which of the following should the analyst disable to enhance the access point security?
A. WPA3
B. AES
C. RADIUS
D. WPS
A retail company that is launching @ new website to showcase the company's product line and other information for online shoppers registered the following URLs:
1.
www companysite com
2.
shop companysite com
3.
about-us companysite com
4.
contact-us. companysite com
5.
secure-logon companysite com
Which of the following should the company use to secure its website rf the company is concerned with convenience and cost?
A. A self-signed certificate
B. A root certificate
C. A code-signing certificate
D. A wildcard certificate
E. An extended validation certificate
During an intemal penetration test, a security analyst identified a network device that had accepted cleartext authentication and was configured with a default credential. Which of the following recommendations should the security analyst make to secure this device?
A. Configure SNMPv1.
B. Configure SNMPv2c
C. Configure SNMPv3.
D. Configure the default community string.
A security analyst sees the following log output while reviewing web logs:
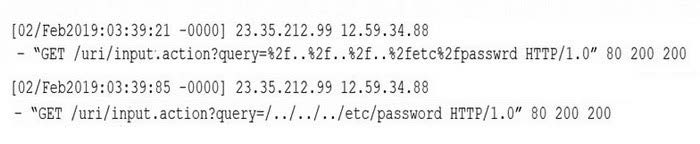
Which of the following mitigation strategies would be BEST to prevent this attack from being successful?
A. Secure cookies
B. Input validation
C. Code signing
D. Stored procedures
An organization has hired a security analyst to perform a penetration test. The analyst captures 1Gb worth of inbound network traffic to the server and transfer the pcap back to the machine for analysis. Which of the following tools should the analyst use to further review the pcap?
A. Nmap
B. cURL
C. Netcat
D. Wireshark
After entering a username and password, and administrator must draw a gesture on a touch screen. Which of the following demonstrates what the administrator is providing?
A. Multifactor authentication
B. Something you can do
C. Biometric
D. Two-factor authentication
Which of the following techniques eliminates the use of rainbow tables for password cracking?
A. Hashing
B. Tokenization
C. Asymmetric encryption
D. Salting
A company is enhancing the security of the wireless network and needs to ensure only employees with a valid certificate can authenticate to the network. Which of the following should the company implement?
A. PEAP
B. PSK
C. WPA3
D. WPS
An administrator assists the legal and compliance team with ensuring information about customer transactions is archived for the proper time period. Which of the following data policies is the administrator carrying out?
A. Compromise
B. Retention
C. Analysis
D. Transfer
E. Inventory
A vulnerability scan returned the following results:
2 Critical 5 High 15 Medium 98 Low
Which of the following would the information security team most likely use to decide if all discovered vulnerabilities must be addressed and the order in which they should be addressed?
A. Risk appetite
B. Risk register
C. Risk matrix
D. Risk acceptance
