SC-100 Online Practice Questions and Answers
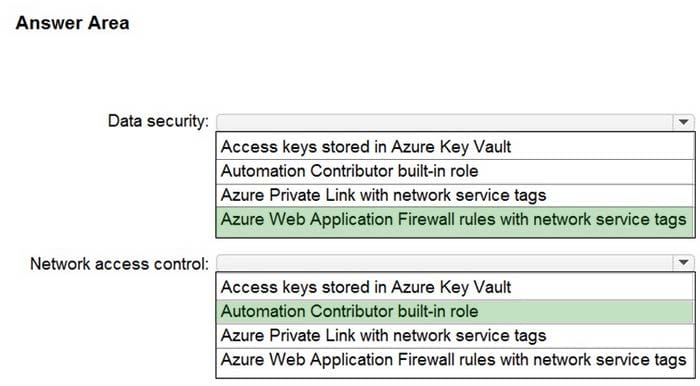
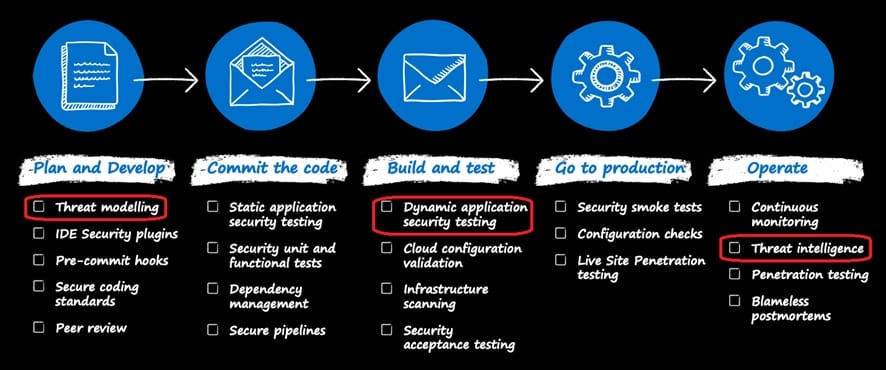
HOTSPOT
You are designing security for a runbook in an Azure Automation account. The runbook will copy data to Azure Data Lake Storage Gen2.
You need to recommend a solution to secure the components of the copy process.
What should you include in the recommendation for each component? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
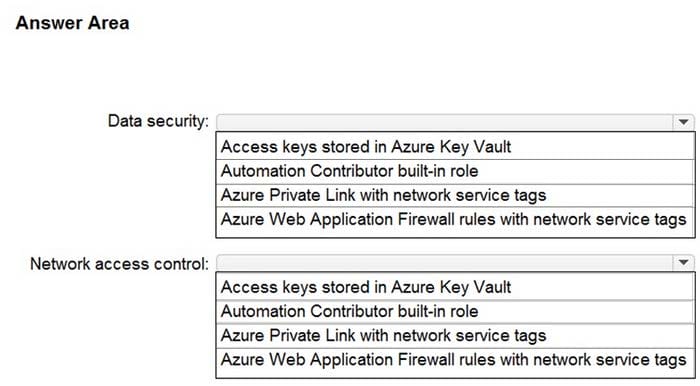
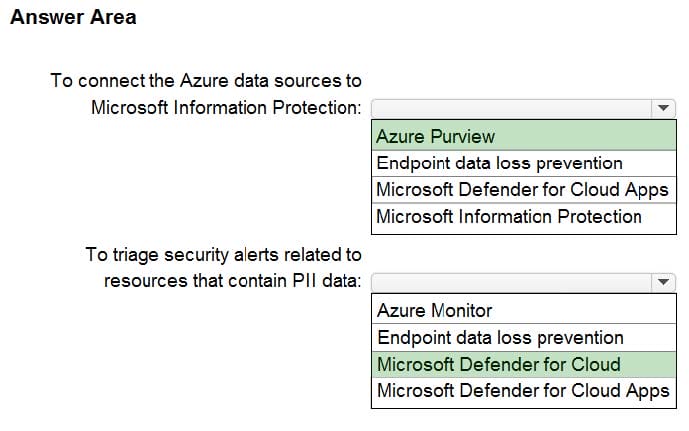
HOTSPOT
Your company is migrating data to Azure. The data contains Personally Identifiable Information (PII).
The company plans to use Microsoft Information Protection for the PII data store in Azure.
You need to recommend a solution to discover PII data at risk in the Azure resources.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
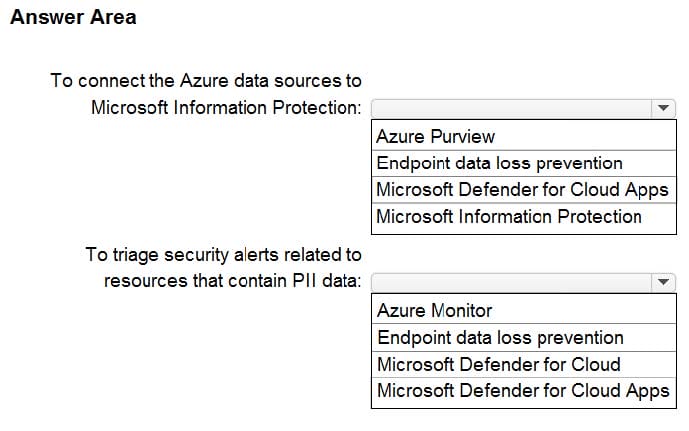
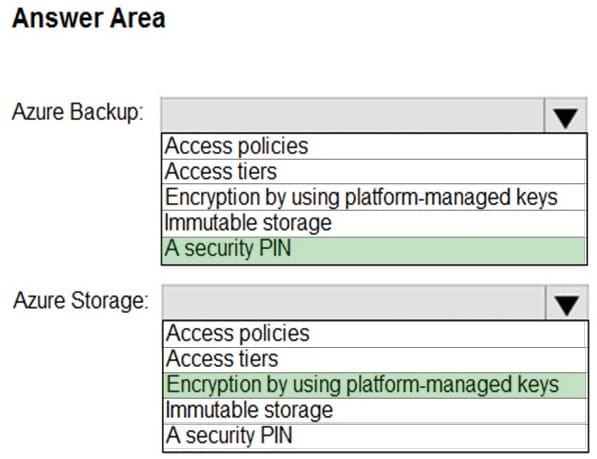
HOTSPOT
Your company wants to optimize using Azure to protect its resources from ransomware.
You need to recommend which capabilities of Azure Backup and Azure Storage provide the strongest protection against ransomware attacks. The solution must follow Microsoft Security Best Practices.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
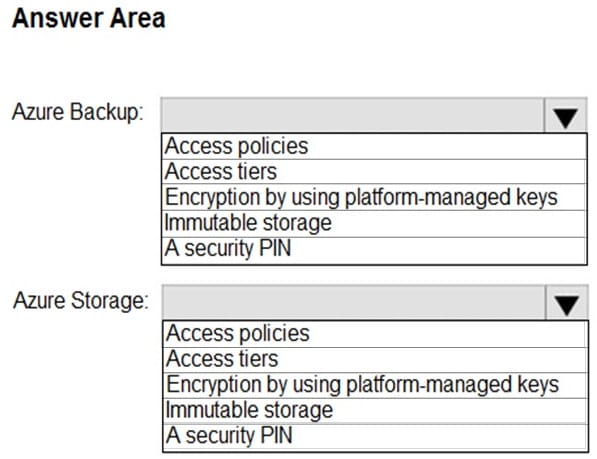
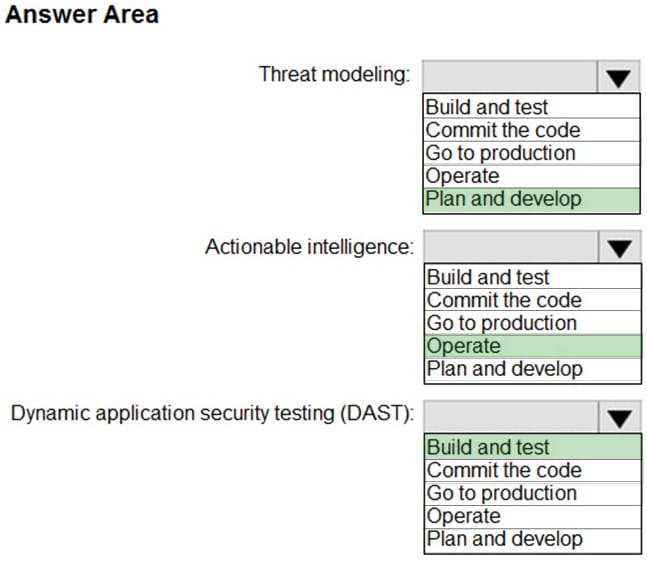
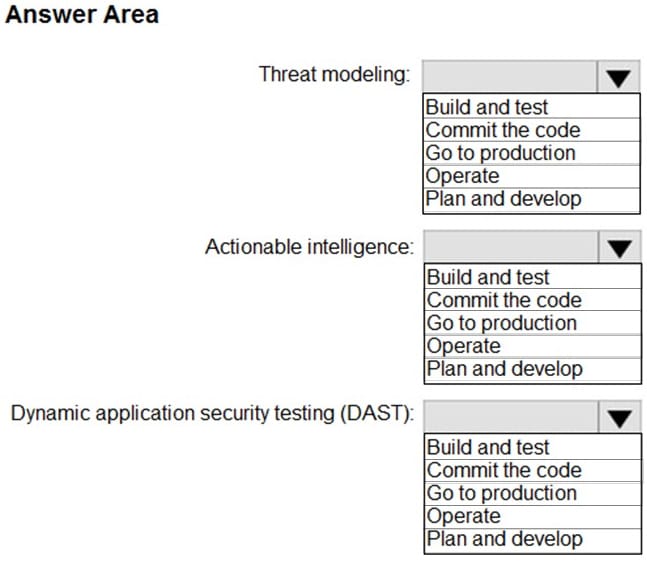
HOTSPOT
You need to recommend a security methodology for a DevOps development process based on the Microsoft Cloud Adoption Framework for Azure.
During which stage of a continuous integration and continuous deployment (CI/CD) DevOps process should each security-related task be performed? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Your company has an on-premises network, an Azure subscription, and a Microsoft 365 E5 subscription. The company uses the following devices:
1.
Computers that run either Windows 10 or Windows 11
2.
Tablets and phones that run either Android or iOS
You need to recommend a solution to classify and encrypt sensitive Microsoft Office 365 data regardless of where the data is stored.
What should you include in the recommendation?
A. eDiscovery
B. Microsoft Information Protection
C. Compliance Manager
D. retention policies
You have 50 Azure subscriptions.
You need to monitor the resource in the subscriptions for compliance with the ISO 27001:2013 standards. The solution must minimize the effort required to modify the list of monitored policy definitions for the subscriptions.
What are two ways to achieve the goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. Assign an initiative to a management group.
B. Assign a policy to each subscription.
C. Assign a policy to a management group.
D. Assign an initiative to each subscription.
E. Assign a blueprint to each subscription.
F. Assign a blueprint to a management group.
You have Windows 11 devices and Microsoft 365 E5 licenses.
You need to recommend a solution to prevent users from accessing websites that contain adult content such as gambling sites.
What should you include in the recommendation?
A. Microsoft Endpoint Manager
B. Compliance Manager
C. Microsoft Defender for Cloud Apps
D. Microsoft Defender for Endpoint
Your company has a hybrid cloud infrastructure that contains an on-premises Active Directory Domain Services (AD DS) forest, a Microsoft 365 subscription, and an Azure subscription.
The company's on-premises network contains internal web apps that use Kerberos authentication. Currently, the web apps are accessible only from the network.
You have remote users who have personal devices that run Windows 11.
You need to recommend a solution to provide the remote users with the ability to access the web apps. The solution must meet the following requirements:
1.
Prevent the remote users from accessing any other resources on the network.
2.
Support Azure Active Directory (Azure AD) Conditional Access.
3.
Simplify the end-user experience. What should you include in the recommendation?
A. Azure AD Application Proxy
B. web content filtering in Microsoft Defender for Endpoint
C. Microsoft Tunnel
D. Azure Virtual WAN
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You need to enforce ISO 27001:2013 standards for the subscription. The solution must ensure that noncompliant resources are remediated automatically.
What should you use?
A. Azure Policy
B. Azure Blueprints
C. the regulatory compliance dashboard in Defender for Cloud
D. Azure role-based access control (Azure RBAC)
For a Microsoft cloud environment, you are designing a security architecture based on the Microsoft Cloud Security Benchmark.
What are three best practices for identity management based on the Azure Security Benchmark? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. Manage application identities securely and automatically.
B. Manage the lifecycle of identities and entitlements
C. Protect identity and authentication systems.
D. Enable threat detection for identity and access management.
E. Use a centralized identity and authentication system.
You have an Azure subscription.
Your company has a governance requirement that resources must be created in the West Europe or North Europe Azure regions.
What should you recommend using to enforce the governance requirement?
A. Azure management groups
B. custom Azure roles
C. Azure Policy assignments
D. regulatory compliance standards in Microsoft Defender for Cloud
Your company has on-premises Microsoft SQL Server databases.
The company plans to move the databases to Azure.
You need to recommend a secure architecture for the databases that will minimize operational requirements for patching and protect sensitive data by using dynamic data masking. The solution must minimize costs.
What should you include in the recommendation?
A. SQL Server on Azure Virtual Machines
B. Azure Synapse Analytics dedicated SQL pools
C. Azure SQL Database
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled.
The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019.
You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator
authorizes the application.
Which security control should you recommend?
A. Azure AD Conditional Access App Control policies
B. Azure Security Benchmark compliance controls in Defender for Cloud
C. app protection policies in Microsoft Endpoint Manager
D. application control policies in Microsoft Defender for Endpoint
You have an on-premises datacenter and an Azure Kubernetes Service (AKS) cluster named AKS1.
You need to restrict internet access to the public endpoint of AKS1. The solution must ensure that AKS1 can be accessed only from the public IP addresses associated with the on-premises datacenter.
What should you use?
A. a private endpoint
B. a network security group (NSG)
C. a service endpoint
D. an authorized IP range
You need to recommend a solution to scan the application code. The solution must meet the application development requirements. What should you include in the recommendation?
A. Azure Key Vault
B. GitHub Advanced Security
C. Application Insights in Azure Monitor
D. Azure DevTest Labs