RC0-501 Online Practice Questions and Answers
A business has recently deployed laptops to all sales employees. The laptops will be used primarily from home offices and while traveling, and a high amount of wireless mobile use is expected. To protect the laptops while connected to untrusted wireless networks, which of the following would be the BEST method for reducing the risk of having the laptops compromised?
A. MAC filtering
B. Virtualization
C. OS hardening
D. Application white-listing
An attacker uses a network sniffer to capture the packets of a transaction that adds $20 to a gift card. The attacker then user a function of the sniffer to push those packets back onto the network again, adding another $20 to the gift card. This can be done many times. Which of the following describes this type of attack?
A. Integer overflow attack
B. Smurf attack
C. Replay attack
D. Buffer overflow attack
E. Cross-site scripting attack
During a recent audit, it was discovered that many services and desktops were missing security patches. Which of the following BEST describes the assessment that was performed to discover this issue?
A. Network mapping
B. Vulnerability scan
C. Port Scan
D. Protocol analysis
A security administrator suspects that data on a server has been exhilarated as a result of unauthorized remote access. Which of the following would assist the administrator in con-firming the suspicions? (Select TWO)
A. Networking access control
B. DLP alerts
C. Log analysis
D. File integrity monitoring
E. Host firewall rules
When designing a web based client server application with single application server and database cluster backend, input validation should be performed:
A. On the client
B. Using database stored procedures
C. On the application server
D. Using HTTPS
A security analyst is performing a quantitative risk analysis. The risk analysis should show the potential monetary loss each time a threat or event occurs. Given this requirement, which of the following concepts would assist the analyst in determining this value? (Select two.)
A. ALE
B. AV
C. ARO
D. EF
E. ROI
A workstation puts out a network request to locate another system. Joe, a hacker on the network, responds before the real system does, and he tricks the workstation into communicating with him. Which of the following BEST describes what occurred?
A. The hacker used a race condition.
B. The hacker used a pass-the-hash attack.
C. The hacker-explogted importer key management.
D. The hacker explogted weak switch configuration.
A group of non-profit agencies wants to implement a cloud service to share resources with each other and minimize costs. Which of the following cloud deployment models BEST describes this type of effort?
A. Public
B. Hybrid
C. Community
D. Private
A security analyst is investigating a suspected security breach and discovers the following in the logs of the potentially compromised server:
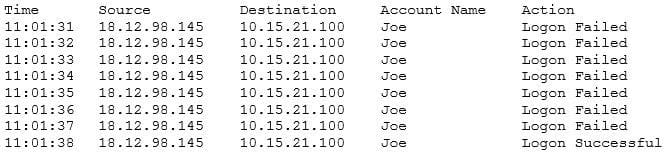
Which of the following would be the BEST method for preventing this type of suspected attack in the future?
A. Implement password expirations
B. Implement restrictions on shared credentials
C. Implement account lockout settings
D. Implement time-of-day restrictions on this server
Which of the following use the SSH protocol?
A. Stelnet
B. SCP
C. SNMP
D. FTPS
E. SSL
F. SFTP
In a corporation where compute utilization spikes several times a year, the Chief Information Officer (CIO) has requested a cost-effective architecture to handle the variable capacity demand. Which of the following characteristics BEST describes what the CIO has requested?
A. Elasticity
B. Scalability
C. High availability
D. Redundancy
When systems, hardware, or software are not supported by the original vendor, it is a vulnerability known as:
A. system sprawl
B. end-of-life systems
C. resource exhaustion
D. a default configuration
An information security specialist is reviewing the following output from a Linux server.

Based on the above information, which of the following types of malware was installed on the server?
A. Logic bomb
B. Trojan
C. Backdoor
D. Ransomware
E. Rootkit
The availability of a system has been labeled as the highest priority. Which of the following should be focused on the MOST to ensure the objective?
A. Authentication
B. HVAC
C. Full-disk encryption
D. File integrity checking