PT0-002 Online Practice Questions and Answers
A penetration tester is assessing a wireless network. Although monitoring the correct channel and SSID, the tester is unable to capture a handshake between the clients and the AP. Which of the following attacks is the MOST effective to allow the penetration tester to capture a handshake?
A. Key reinstallation
B. Deauthentication
C. Evil twin
D. Replay
A penetration tester completed a vulnerability scan against a web server and identified a single but severe vulnerability.
Which of the following is the BEST way to ensure this is a true positive?
A. Run another scanner to compare.
B. Perform a manual test on the server.
C. Check the results on the scanner.
D. Look for the vulnerability online.
A penetration tester would like to obtain FTP credentials by deploying a workstation as an on-path attack between the target and the server that has the FTP protocol. Which of the following methods would be the BEST to accomplish this objective?
A. Wait for the next login and perform a downgrade attack on the server.
B. Capture traffic using Wireshark.
C. Perform a brute-force attack over the server.
D. Use an FTP exploit against the server.
Which of the following provides an exploitation suite with payload modules that cover the broadest range of target system types?
A. Nessus
B. Metasploit
C. Burp Suite
D. Ethercap
Which of the following types of assessments MOST likely focuses on vulnerabilities with the objective to access specific data?
A. An unknown-environment assessment
B. A known-environment assessment
C. A red-team assessment
D. A compliance-based assessment
A penetration tester fuzzes an internal server looking for hidden services and applications and obtains the following output:
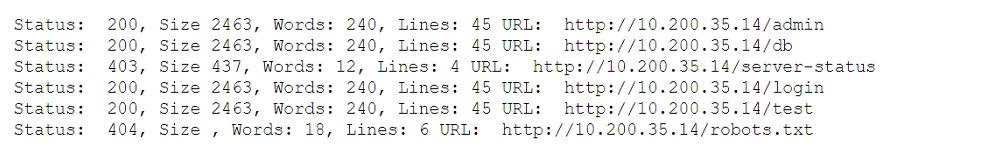
Which of the following is the most likely explanation for the output?
A. The tester does not have credentials to access the server-status page.
B. The admin directory cannot be fuzzed because it is forbidden.
C. The admin, test, and db directories redirect to the log-in page.
D. The robots.txt file has six entries in it.
A penetration tester writes the following script:
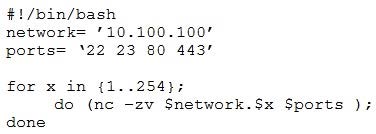
Which of the following is the tester performing?
A. Searching for service vulnerabilities
B. Trying to recover a lost bind shell
C. Building a reverse shell listening on specified ports
D. Scanning a network for specific open ports
After running the enum4linux.pl command, a penetration tester received the following output: Which of the following commands should the penetration tester run NEXT?
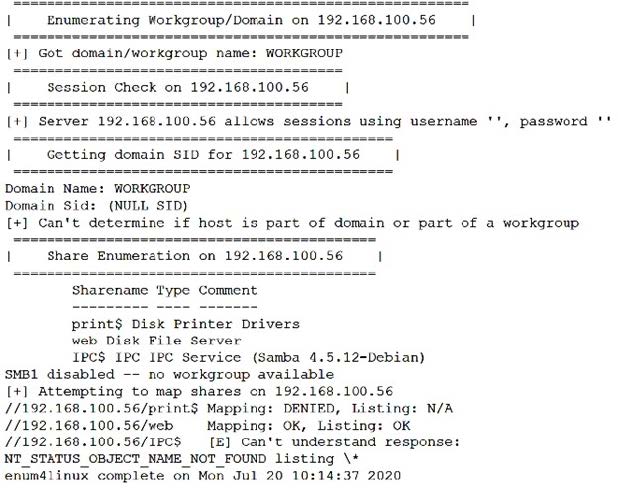
A. smbspool //192.160.100.56/print$
B. net rpc share -S 192.168.100.56 -U ''
C. smbget //192.168.100.56/web -U ''
D. smbclient //192.168.100.56/web -U '' -N
During a penetration tester found a web component with no authentication requirements. The web component also allows file uploads and is hosted on one of the target public web the following actions should the penetration tester perform next?
A. Continue the assessment and mark the finding as critical.
B. Attempting to remediate the issue temporally.
C. Notify the primary contact immediately.
D. Shutting down the web server until the assessment is finished
In Python socket programming, SOCK_DGRAM type is:
A. reliable.
B. matrixed.
C. connectionless.
D. slower.
A penetration tester has gained access to part of an internal network and wants to exploit on a different network segment. Using Scapy, the tester runs the following command:
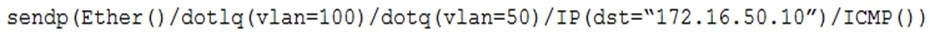
Which of the following represents what the penetration tester is attempting to accomplish?
A. DNS cache poisoning
B. MAC spoofing
C. ARP poisoning
D. Double-tagging attack
A penetration tester gains access to a system and establishes persistence, and then runs the following commands:
cat /dev/null > temp
touch -r .bash_history temp
mv temp .bash_history
Which of the following actions is the tester MOST likely performing?
A. Redirecting Bash history to /dev/null
B. Making a copy of the user's Bash history for further enumeration
C. Covering tracks by clearing the Bash history
D. Making decoy files on the system to confuse incident responders
Penetration tester has discovered an unknown Linux 64-bit executable binary. Which of the following tools would be BEST to use to analyze this issue?
A. Peach
B. WinDbg
C. GDB
D. OllyDbg
A red-team tester has been contracted to emulate the threat posed by a malicious insider on a company's network, with the constrained objective of gaining access to sensitive personnel files. During the assessment, the red-team tester identifies an artifact indicating possible prior compromise within the target environment.
Which of the following actions should the tester take?
A. Perform forensic analysis to isolate the means of compromise and determine attribution.
B. Incorporate the newly identified method of compromise into the red team's approach.
C. Create a detailed document of findings before continuing with the assessment.
D. Halt the assessment and follow the reporting procedures as outlined in the contract.
A penetration tester is performing a vulnerability scan on a large ATM network. One of the organization's requirements is that the scan does not affect legitimate clients' usage of the ATMs. Which of the following should the tester do to best meet the company's vulnerability scan requirements?
A. Use Nmap's -T2 switch to run a slower scan and with less resources.
B. Run the scans using multiple machines.
C. Run the scans only during lunch hours.
D. Use Nmap's -host-timeout switch to skip unresponsive targets.
