PSE-PLATFORM Online Practice Questions and Answers
Where are three tuning considerations when building a security policy to protect against modern day attacks? (Choose three)
A. Create an anti-spyware profile to block all spyware
B. Create a vulnerability protection profile to block all the vulnerabilities with severity low and higher
C. Create an SSL Decryption policy to decrypt 100% of the traffic
D. Create an antivirus profile to block all content that matches and antivirus signature
E. Create a WildFire profile to schedule file uploads during low network usage windows
Which two designs require virtual systems? (Choose two.)
A. A shared gateway interface that does not need a full administrative boundary
B. A virtual router as a replacement for an internet-facing router
C. A single physical firewall shared by different organizations, each with unique traffic control needs
D. A VMware NSX deployment that needs micros segmentation
Which license is required to receive weekly dynamic updates to the correlation objects on the firewall and Panorama?
A. WildFire on the firewall, and AutoFocus on Panorama
B. URL Filtering on the firewall, and MindMeld on Panorama
C. Threat Prevention on the firewall, and Support on Panorama
D. GlobalProtect on the firewall, and Threat Prevention on Panorama
How do Highly Suspicious artifacts in-AutoFocus help identify when an unknown, potential zero-day, targeted attack occur to allow one to adjust the security posture?
A. Highly Suspicious artifacts are associated with High-Risk payloads that are inflicting massive amounts of damage to end customers.
B. All High Risk artifacts are automatically classified as Highly Suspicious.
C. Highly Suspicious artifacts are High Risk artifacts that have been seen in very few samples.
D. Highly Suspicious artifacts have been seen infecting a broad, significant range of companies.
Which two components must to be configured within User-ID on a new firewall that has been implemented? (Choose two.)
A. Group Mapping
B. 802.1X Authentication
C. Proxy Authentication
D. User mapping
Which option is required to activate/retrieve a Device Management License on the M.100 Appliance after the Auth Codes have been activated on the Palo Alto Networks Support Site?
A. Generate a Tech Support File and call PANTAC
B. Select Device > Licenses and click activate feature using authorization code
C. Select PANORAMA > Licenses and click Activate feature using authorization code
D. Generate a State Dump File and upload it to the Palo Alto Network support portal
What are three considerations when deploying User-ID. (Choose three.)
A. Enable WMI probing in high security networks
B. User-ID can support a maximum hops.
C. Specify included and excluded networks when configuring User-ID
D. Use a dedicated service account for User-ID services with the minimal permissions necessary.
E. Only enable User-ID on trusted zones
A client chooses to not block uncategorized websites.
Which two additions should be made to help provide some protection? (Choose two.)
A. A security policy rule using only known URL categories with the action set to allow
B. A file blocking profile to security policy rules that allow uncategorized websites to help reduce the risk of drive by downloads
C. A URL filtering profile with the action set to continue for unknown URL categories to security policy rules that allow web access
D. A data filtering profile with a custom data pattern to security policy rules that deny uncategorized websites
Which configuration creates the most comprehensive "best-practice" Anti Spyware profile to prevent command and Control traffic?
A. Clone the Strict Anti-Spyware Profile, enable DNS Sinkholing and Passive DNS Monitoring, and deploy this customized clone
B. Clone the Default Anti-Spyware Profile and enable DNS Sinkholing and Passive DNS Monitoring, and deploy this customized clone
C. Edit and deploy the Default Anti-Spyware Profile (DNS Sinkholing and Passive DNS Monitoring is already enabled)
D. Edit and deploy the Strict Anti-Spyware Profile Profile (DNS Sinkholing and Passive DNS Monitoring is already enabled)
Given the following network diagram, an administrator is considering the use of Windows Log Forwarding and Global Catalog servers for User-ID implementation.
What are two potential bandwidth and processing bottlenecks to consider? (Choose two.)
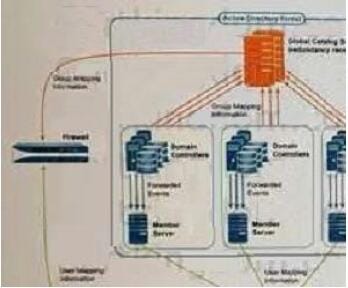
A. Member Servers
B. Firewall
C. Domain Controllers
D. Windows Server
What is a best practice when configuring a security policy to completely block a specific application?
A. One the Service/URL. Category tab, set the service to any
B. On the Actions tab, configure a file blocking security profile
C. On the Service/URL. Category tab, set the service to application-default
D. On the Service/URL. Category tab, manually specify a port/service
How often are regularly scheduled update for the Anti-virus Application, Threats, and Wildfire subscription databases made available by Palo Alto Networks in PAN-OS 8.0?
A. Anti-Virus (Daily) Application (Weekly), Threats (Daily), Wildfire (5 Minutes)
B. Anti-Virus (Weekly) Application (Daily), Threats (Daily), Wildfire (5 Minutes)
C. Anti-Virus (Daily) Application (Weekly), Threats (Weekly), Wildfire (5 Minutes)
D. Anti-Virus (Weekly) Application (Daily), Threats (Weekly), Wildfire (5 Minutes)
Which three methods used to map users to IP addresses are supported in Palo Alto Networks firewalls? (Choose three.)
A. Client Probing
B. TACACS
C. eDirectory monitoring
D. SNMP server
E. Lotus Domino
F. RADIUS
G. Active Directory monitoring
Which three policies or certificates must be configured for SSL Forward Proxy decryption? (Choose three.)
A. Forward trust certificate
B. Forward untrust certificate
C. A decrypt port mirror policy
D. Internal server certificate
E. A decryption policy
Which design objective could be satisfied by vsys functionality?
A. Separation of routing tables used by different departments in company
B. Provide same-device high availability functionality for different departments in a company
C. Administrative separation of firewall policies used by different departments in company
D. Allocate firewall hardware resources to different departments in a company
