PCNSC Online Practice Questions and Answers
Which PAN-OS policy must you configure to force a user to provide additional credential before he is allowed to access an internal application that contains highly sensitive business data?
A. Authentication policy
B. Decryption policy
C. Security policy
D. Application Override policy
In High Availability, which information is transferred via the HA data link?
A. heartbeats
B. HA state information
C. session information
D. User-ID information
An administrator using an enterprise PKI needs to establish a unique chain of trust to ensure mutual authentication between panorama and the managed firewall and Log Collectors. How would the administrator establish the chain of trust?
A. Configure strong password
B. Set up multiple-factor authentication.
C. Use custom certificates.
D. Enable LDAP or RADIUS integration.
Refer to the exhibit.
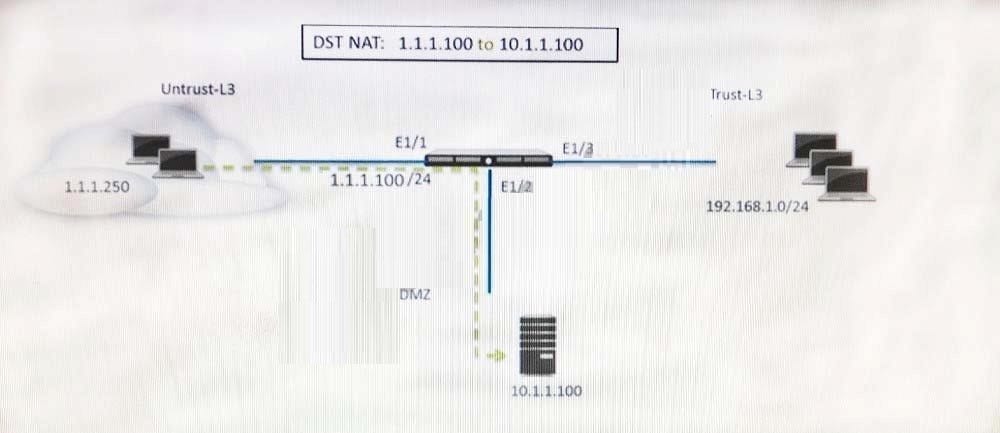
A web server in the DMZ is being mapped to a public address through DNAT. Which Security policy rule will allow traffic to flow to the web server?
A. Untrust (any) to Untrust (10. 1.1. 100), web browsing -Allow
B. Untrust (any) to Untrust (1. 1. 1. 100), web browsing -Allow
C. Untrust (any) to DMZ (1. 1. 1. 100), web browsing -Allow
D. Untrust (any) to DMZ (10. 1. 1. 100), web browsing -Allow
Which feature prevents the submission of login information into website froms?
A. credential phishing prevention
B. file blocking
C. User-ID
D. data filtering
Which event will happen administrator uses an Application Override Policy?
A. The application name assigned to the traffic by the security rule is written to the traffic log.
B. The Palo Alto Networks NGFW Steps App-ID processing at Layer 4.
C. Threat-ID processing time is decreased.
D. App-ID processing time is increased.
Which action would enables the firewalls to send their preexisting logs to Panorama?
A. A CLI command will forward the pre-existing logs to Panorama.
B. Use the import option to pull logs panorama.
C. Use the ACC to consolidate pre-existing logs.
D. The- log database will need to be exported from the firewall and manually imported into Panorama.
An administrator wants multiple web servers in the DMZ to receive connections from the internet. Traffic destined for 206.15.22.9 port 80/TCP needs to be forwarded to the server at 10 1.22 Based on the information shown in the age, which NAT rule will forward web-browsing traffic correctly?
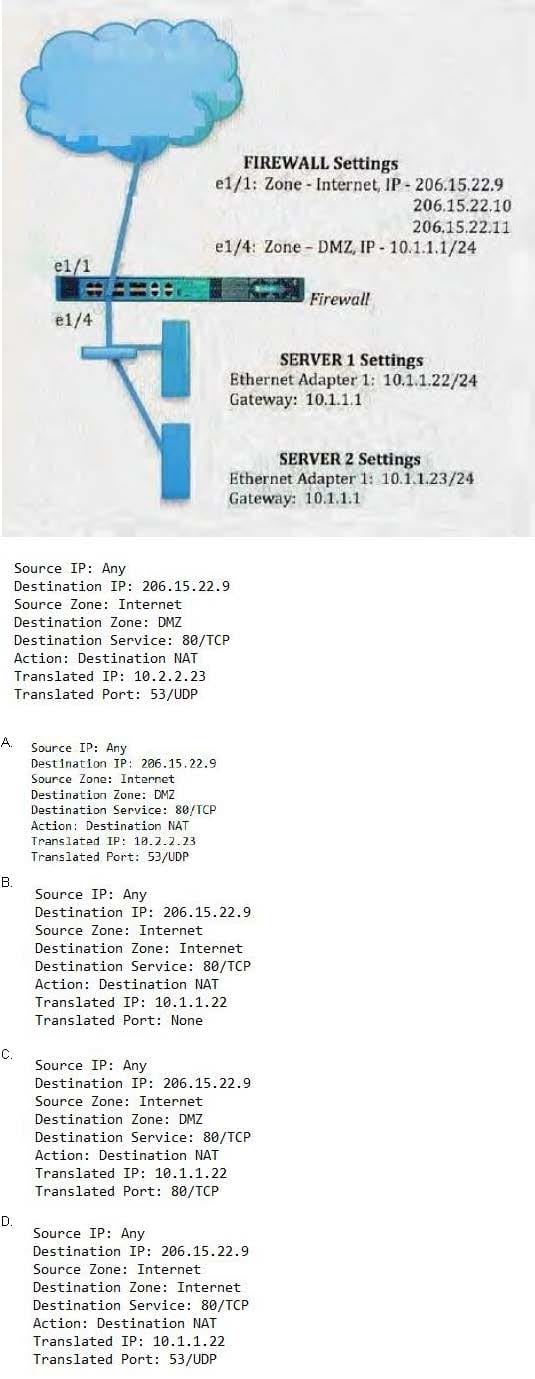
A. B. C. D.
A Security policy rule is configured with a Vulnerability Protection Profile and an action of Deny".
Which action will this configuration cause on the matched traffic?
A. The configuration is invalid it will cause the firewall to Skip this Security policy rule A warning will be displayed during a command.
B. The configuration is valid It will cause the firewall to deny the matched sessions. Any configured Security Profiles have no effect if the Security policy rule action is set to "Deny".
C. The configuration will allow the matched session unless a vulnerability signature is detected. The "Deny" action will supersede the per. defined, severity defined actions defined in the associated Vulnerability Protection Profile.
D. The configuration is invalid. The Profile Settings section will be- grayed out when the action is set to "Deny".
What are two benefits of nested device groups in panorama? (Choose two )
A. overwrites local firewall configuration
B. requires configuration both function and location for every device
C. all device groups inherit setting from the Shared group
D. reuse of the existing Security policy rules and objects
Winch three steps will reduce the CPU utilization on the management plane? (Choose three. )
A. Disable predefined reports.
B. Reduce the traffic being decrypted by the firewall.
C. Disable SNMP on the management interface.
D. Application override of SSL application.
Which three options are supposed in HA Lite? (Choose three.)
A. Configuration synchronization
B. Virtual link
C. active/passive deployment
D. session synchronization
E. synchronization of IPsec security associations
During the packet flow process, which two processes are performed in application identification? (Choose two.)
A. Application changed from content inspection
B. session application identified
C. pattern based application identification
D. application override policy match
Which DoS protection mechanism detects and prevents session exhaustion attacks?
A. TCP Port Scan Protection
B. Flood Protection
C. Resource Protection
D. Pocket Based Attack Protection
A network security engineer is asked to provide a report on bandwidth usage. Which tab in the ACC provides the information needed to create the report?
A. Blocked Activity
B. Bandwidth Activity
C. Threat Activity
D. Network Activity
