PCCSA Online Practice Questions and Answers
DRAG DROP
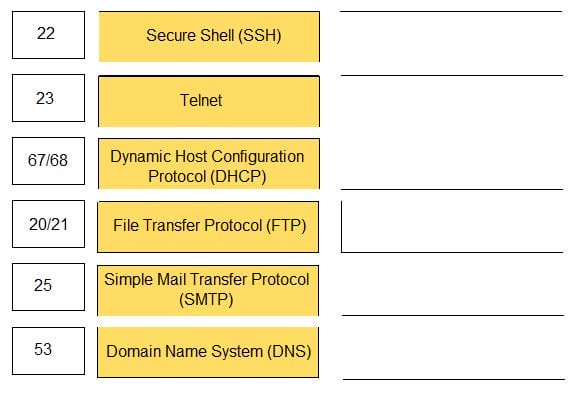
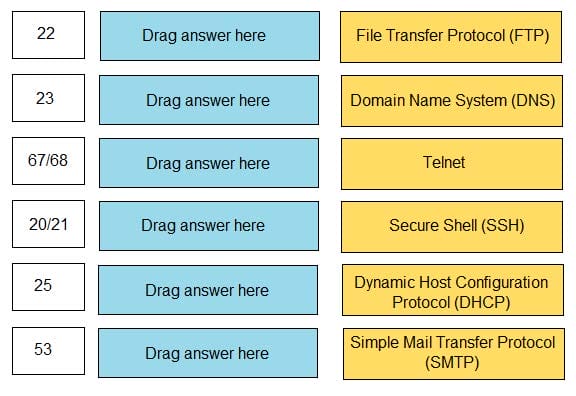
Match the common TCP/IP protocol with its corresponding port(s).
Select and Place:
DRAG DROP
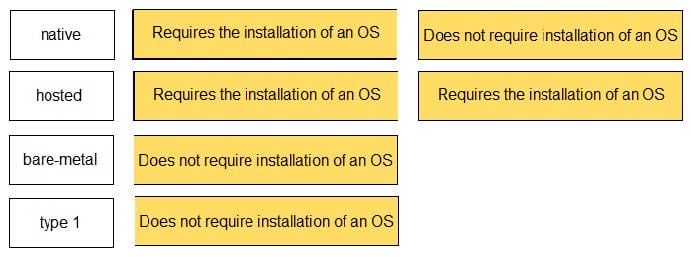
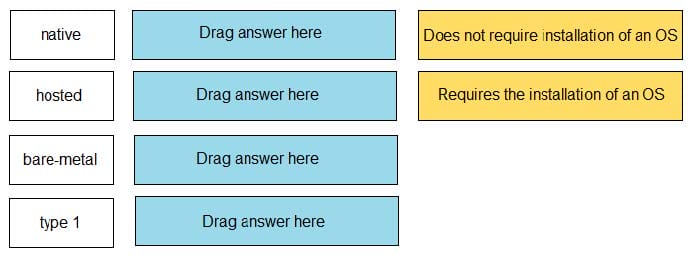
Match the task for server settings in group mapping with its order in the process.
Select and Place:
Which Palo Alto Networks product or feature includes machine learning to enhance security?
A. Panorama
B. MineMeld
C. Magnifier
D. User-ID
Which type of attack floods a target with ICMP requests?
A. route table poisoning
B. reconnaissance
C. IP spoofing
D. denial-of-service
Which type of attack floods a target with TCP SYN requests?
A. route table poisoning
B. reconaissance
C. denial-of-service
D. IP spoofing
Which two components are part of a next-generation firewall security policy? (Choose two.)
A. role-based access controls
B. user identification
C. content identification
D. file permissions
Which data security compliance standard is used to protect card holder data wherever it is processed, stored, or transmitted?
A. Property Card Industry
B. Payment Card Industry
C. Personal Card Industry
D. Payment Club Industry
You discover an infected email attachment that contains software code that attacks a known vulnerability in a popular social networking application. This type of software code belongs to which type of malware category?
A. social engineering
B. virus
C. pharming
D. exploit
What is an example of a distance-vector routing protocol?
A. OSPF
B. BGP
C. RIP D. IGRP
Which option lists the correct sequence of a TCP three-way handshake?
A. SYN, ACK, SYN
B. SYN, SYN+ACK, ACK
C. SYN, ACK, FIN
D. SYN, SYN+ACK, FIN
In the context of a mobile device management solution, what is a function of the "policy enforcement" feature?
A. controls which websites can be accessed when connected to Wi-Fi
B. controls which Wi-Fi networks can be accessed
C. controls which phone numbers can be dialed
D. controls which password/passcode settings are allowed
During which step of the cyber-attack lifecycle is a user's web browser redirected to a webpage that automatically downloads malware to the endpoint?
A. delivery
B. weaponization
C. reconnaissance
D. command-and-control
Which two remote access methods are secure because they encrypt traffic? (Choose two.)
A. IPsec-AH
B. SSH
C. VPN
D. Telnet
E. rlogin
In PKI, which item is issued by a CA?
A. digital certificate
B. SSH key
C. KDC ticket
D. shared key
On an endpoint, which method should you use to secure applications against exploits?
A. full-disk encryption
B. strong user passwords
C. software patches
D. endpoint-based firewall