NSE6_FWB-6.4 Online Practice Questions and Answers
What capability can FortiWeb add to your Web App that your Web App may or may not already have?
A. Automatic backup and recovery
B. High Availability
C. HTTP/HTML Form Authentication
D. SSL Inspection
An e-commerce web app is used by small businesses. Clients often access it from offices behind a router, where clients are on an IPv4 private network LAN. You need to protect the web application from denial of service attacks that use request floods.
What FortiWeb feature should you configure?
A. Enable "Shared IP" and configure the separate rate limits for requests from NATted source IPs.
B. Configure FortiWeb to use "X-Forwarded-For:" headers to find each client's private network IP, and to block attacks using that.
C. Enable SYN cookies.
D. Configure a server policy that matches requests from shared Internet connections.
Refer to the exhibit.
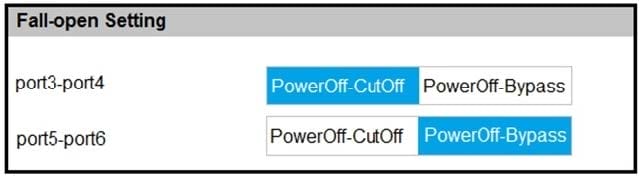
Based on the configuration, what would happen if this FortiWeb were to lose power? (Choose two.)
A. Traffic that passes between port5 and port6 will be inspected.
B. Traffic will be interrupted between port3 and port4.
C. All traffic will be interrupted.
D. Traffic will pass between port5 and port6 uninspected.
Which two statements about the anti-defacement feature on FortiWeb are true? (Choose two.)
A. Anti-defacement can redirect users to a backup web server, if it detects a change.
B. Anti-defacement downloads a copy of your website to RAM, in order to restore a clean image, if it detects defacement.
C. FortiWeb will only check to see if there are changes on the web server; it will not download the whole file each time.
D. Anti-defacement does not make a backup copy of your databases.
What role does FortiWeb play in ensuring PCI DSS compliance?
A. It provides the ability to securely process cash transactions.
B. It provides the required SQL server protection.
C. It provides the WAF required by PCI.
D. It provides credit card processing capabilities.
You are using HTTP content routing on FortiWeb. You want requests for web application A to be forwarded to a cluster of web servers, which all host the same web application. You want requests for web application B to be forwarded to a different, single web server.
Which statement about this solution is true?
A. The server policy applies the same protection profile to all of its protected web applications.
B. You must put the single web server in to a server pool, in order to use it with HTTP content routing.
C. You must chain policies so that requests for web application A go to the virtual server for policy A, and requests for web application B go to the virtual server for policy B.
D. Static or policy-based routes are not required.
When integrating FortiWeb and FortiAnalyzer, why is the selection for FortiWeb Version critical? (Choose two)
A. Defines Log file format
B. Defines communication protocol
C. Defines Database Schema
D. Defines Log storage location
You are using HTTP content routing on FortiWeb. Requests for web app A should be forwarded to a cluster of web servers which all host the same web app. Requests for web app B should be forwarded to a different, single web server.
Which is true about the solution?
A. Static or policy-based routes are not required.
B. To achieve HTTP content routing, you must chain policies: the first policy accepts all traffic, and forwards requests for web app A to the virtual server for policy A. It also forwards requests for web app B to the virtual server for policy B. Policy A and Policy B apply their app-specific protection profiles, and then distribute that app's traffic among all members of the server farm.
C. You must put the single web server into a server pool in order to use it with HTTP content routing.
D. The server policy applies the same protection profile to all its protected web apps.
What role does FortiWeb play in ensuring PCI DSS compliance?
A. PCI specifically requires a WAF
B. Provides credit card processing capabilities
C. Provide ability to securely process cash transactions
D. Provides load balancing between multiple web servers
Which is true about HTTPS on FortiWeb? (Choose three.)
A. For SNI, you select the certificate that FortiWeb will present in the server pool, not in the server policy.
B. After enabling HSTS, redirects to HTTPS are no longer necessary.
C. In true transparent mode, the TLS session terminator is a protected web server.
D. Enabling RC4 protects against the BEAST attack, but is not recommended if you configure FortiWeb to only offer TLS 1.2.
E. In transparent inspection mode, you select which certificate that FortiWeb will present in the server pool, not in the server policy.
Which operation mode does not require additional configuration in order to allow FTP traffic to your web server?
A. Offline Protection
B. Transparent Inspection
C. True Transparent Proxy
D. Reverse-Proxy
A client is trying to start a session from a page that should normally be accessible only after they have logged in.
When a start page rule detects the invalid session access, what can FortiWeb do? (Choose three.)
A. Reply with a "403 Forbidden" HTTP error
B. Allow the page access, but log the violation
C. Automatically redirect the client to the login page
D. Display an access policy message, then allow the client to continue, redirecting them to their requested page
E. Prompt the client to authenticate
How does your FortiWeb configuration differ if the FortiWeb is upstream of the SNAT device instead of downstream of the SNAT device?
A. You must enable the "Use" X-Forwarded-For: option.
B. FortiWeb must be set for Transparent Mode
C. No special configuration required
D. You must enable "Add" X-Forwarded-For: instead of the "Use" X-Forwarded-For: option.
FortiWeb offers the same load balancing algorithms as FortiGate.
Which two Layer 7 switch methods does FortiWeb also offer? (Choose two.)
A. Round robin
B. HTTP session-based round robin
C. HTTP user-based round robin
D. HTTP content routes
Which algorithm is used to build mathematical models for bot detection?
A. HCM
B. SVN
C. SVM
D. HMM
