NSE5_FCT-7.0 Online Practice Questions and Answers
Refer to the exhibit.
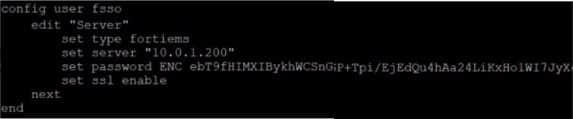
Based on the CLI output from FortiGate. which statement is true?
A. FortiGate is configured to pull user groups from FortiClient EMS
B. FortiGate is configured with local user group
C. FortiGate is configured to pull user groups from FortiAuthenticator
D. FortiGate is configured to pull user groups from AD Server.
Refer to the exhibit.
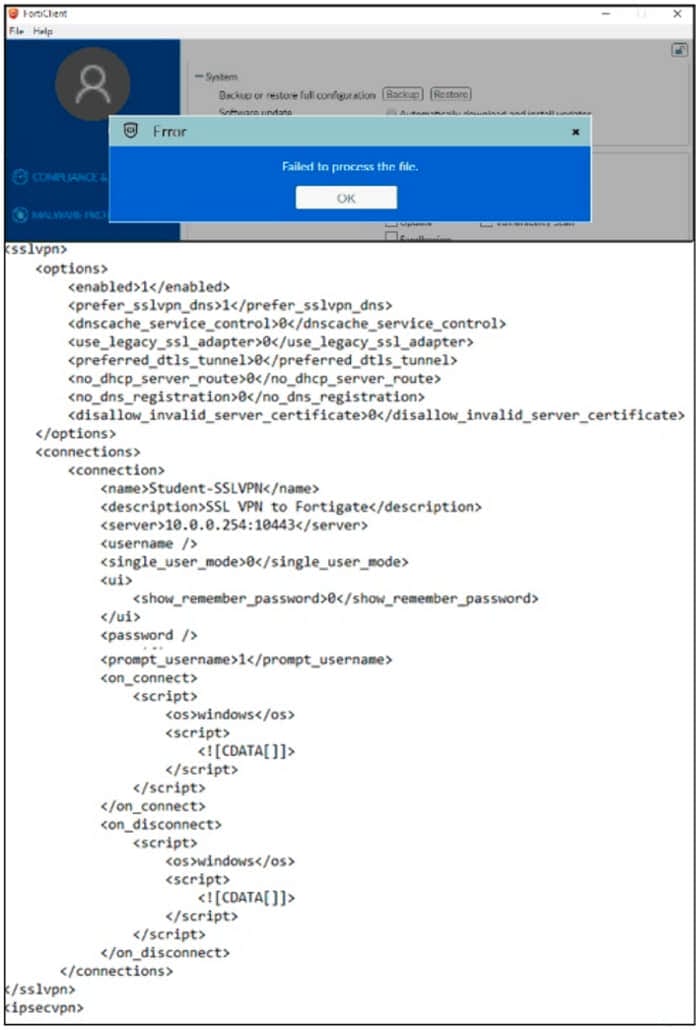
An administrator has restored the modified XML configuration file to FortiClient and sees the error shown in the exhibit.
Based on the XML settings shown in the exhibit, what must the administrator do to resolve the issue with the XML configuration file?
A. The administrator must resolve the XML syntax error.
B. The administrator must use a password to decrypt the file
C. The administrator must change the file size
D. The administrator must save the file as FortiClient-config conf.
Which component or device shares ZTNA tag information through Security Fabric integration?
A. FortiGate
B. FortiGate Access Proxy
C. FortiClient
D. FortiClient EMS
Refer to the exhibit.
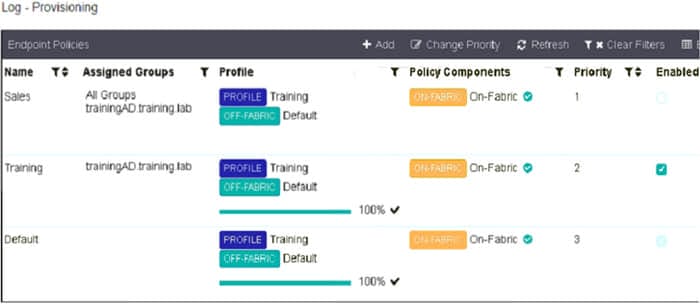
Which shows multiple endpoint policies on FortiClient EMS.
Which policy is applied to the endpoint in the AD group trainingAD?
A. The Sales policy
B. The Training policy
C. Both the Sales and Training policies because their priority is higher than the Default policy
D. The Default policy because it has the highest priority
An administrator needs to connect FortiClient EMS as a fabric connector to FortiGate. What is the prerequisite to get FortiClient EMS to connect to FortiGate successfully?
A. Revoke and update the FortiClient EMS root CA.
B. Revoke and update the FortiClient client certificate on EMS.
C. Import and verify the FortiClient client certificate on FortiGate.
D. Import and verify the FortiClient EMS root CA certificate on FortiGate
Refer to the exhibit, which shows the Zero Trust Tagging Rule Set configuration.
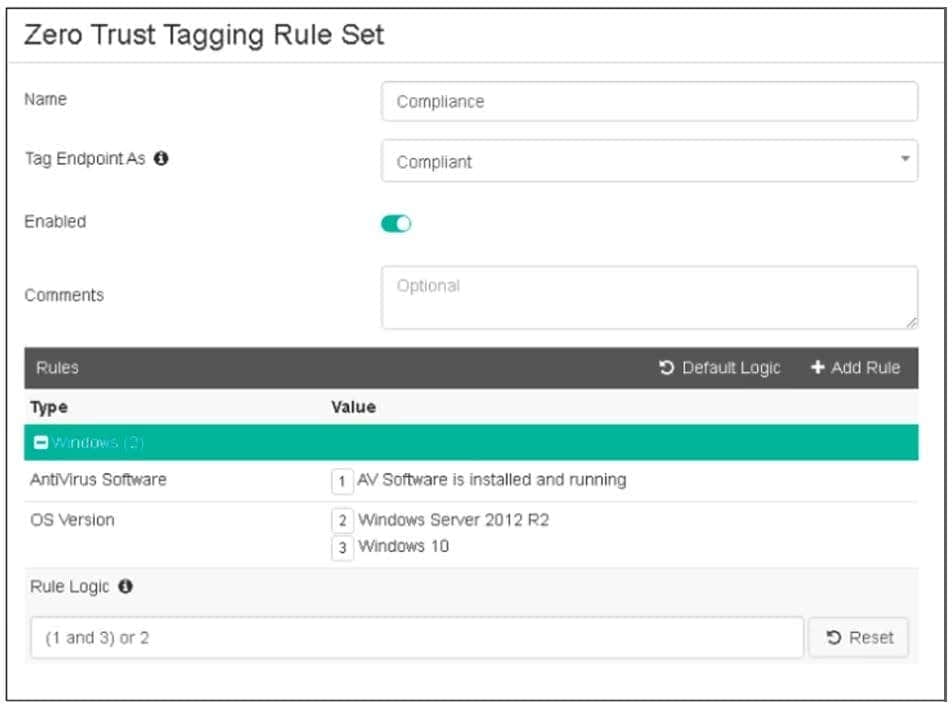
Which two statements about the rule set are true? (Choose two.)
A. The endpoint must satisfy that only Windows 10 is running.
B. The endpoint must satisfy that only AV software is installed and running.
C. The endpoint must satisfy that antivirus is installed and running and Windows 10 is running.
D. The endpoint must satisfy that only Windows Server 2012 R2 is running.
Why does FortiGate need the root CA certificate of FortiClient EMS?
A. To sign FortiClient CSR requests
B. To revoke FortiClient client certificates
C. To trust certificates issued by FortiClient EMS
D. To update FortiClient client certificates
An administrator is required to maintain a software inventory on the endpoints. without showing the feature on the FortiClient dashboard What must the administrator do to achieve this requirement?
A. The administrator must use default endpoint profile
B. The administrator must not select the vulnerability scan feature in the deployment package.
C. The administrator must select the vulnerability scan feature in the deployment package, but disable the feature on the endpoint profile
D. The administrator must click the hide icon on the vulnerability scan tab
