NSE4_FGT-7.2 Online Practice Questions and Answers
Which three statements are true regarding session-based authentication? (Choose three.)
A. HTTP sessions are treated as a single user.
B. IP sessions from the same source IP address are treated as a single user.
C. It can differentiate among multiple clients behind the same source IP address.
D. It requires more resources.
E. It is not recommended if multiple users are behind the source NAT
An administrator observes that the port1 interface cannot be configured with an IP address. What can be the reasons for that? (Choose three.)
A. The interface has been configured for one-arm sniffer.
B. The interface is a member of a virtual wire pair.
C. The operation mode is transparent.
D. The interface is a member of a zone.
E. Captive portal is enabled in the interface.
An administrator needs to increase network bandwidth and provide redundancy.
What interface type must the administrator select to bind multiple FortiGate interfaces?
A. VLAN interface
B. Software Switch interface
C. Aggregate interface
D. Redundant interface
Refer to the exhibit.
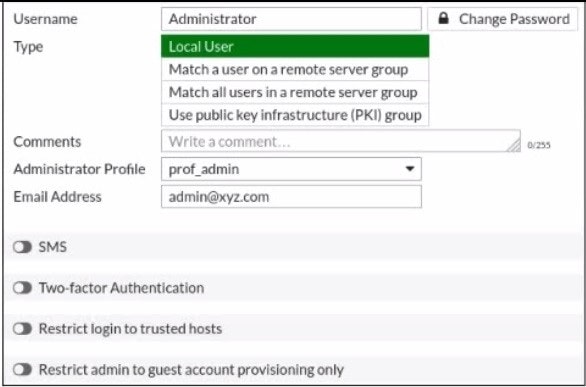
The global settings on a FortiGate device must be changed to align with company security policies. What does the Administrator account need to access the FortiGate global settings?
A. Change password
B. Enable restrict access to trusted hosts
C. Change Administrator profile
D. Enable two-factor authentication
An administrator wants to simplify remote access without asking users to provide user credentials. Which access control method provides this solution?
A. ZTNA IP/MAC filtering mode
B. ZTNA access proxy
C. SSL VPN
D. L2TP
If Internet Service is already selected as Destination in a firewall policy, which other configuration object can be selected for the Destination field of a firewall policy?
A. IP address
B. No other object can be added
C. FQDN address
D. User or User Group
An administrator has configured a strict RPF check on FortiGate. Which statement is true about the strict RPF check?
A. The strict RPF check is run on the first sent and reply packet of any new session.
B. Strict RPF checks the best route back to the source using the incoming interface.
C. Strict RPF checks only for the existence of at least one active route back to the source using the incoming interface.
D. Strict RPF allows packets back to sources with all active routes.
Which two statements are correct about NGFW Policy-based mode? (Choose two.)
A. NGFW policy-based mode does not require the use of central source NAT policy
B. NGFW policy-based mode can only be applied globally and not on individual VDOMs
C. NGFW policy-based mode supports creating applications and web filtering categories directly in a firewall policy
D. NGFW policy-based mode policies support only flow inspection
Refer to the exhibit showing a debug flow output.
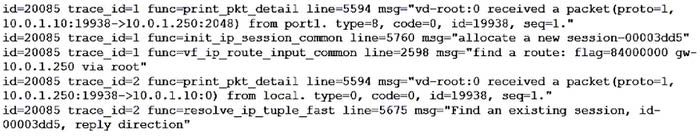
What two conclusions can you make from the debug flow output? (Choose two.)
A. The debug flow is for ICMP traffic.
B. The default route is required to receive a reply.
C. Anew traffic session was created.
D. A firewall policy allowed the connection.
An administrator wants to configure Dead Peer Detection (DPD) on IPSEC VPN for detecting dead tunnels. The requirement is that FortiGate sends DPD probes only when no traffic is observed in the tunnel.
Which DPD mode on FortiGate will meet the above requirement?
A. Disabled
B. On Demand
C. Enabled
D. On Idle
Which of the following are valid actions for FortiGuard category based filter in a web filter profile ui proxy-based inspection mode? (Choose two.)
A. Warning
B. Exempt
C. Allow
D. Learn
To complete the final step of a Security Fabric configuration, an administrator must authorize all the devices on which device?
A. FortiManager
B. Root FortiGate
C. FortiAnalyzer
D. Downstream FortiGate
Examine the exhibit, which contains a virtual IP and firewall policy configuration.
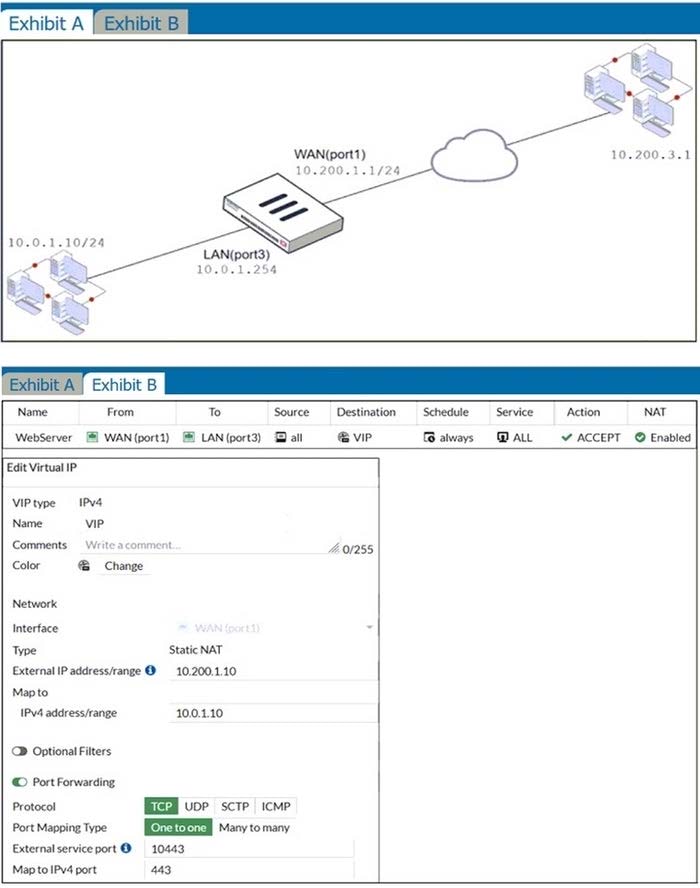
The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port2) interface has the IP address 10.0.1.254/24.
The first firewall policy has NAT enabled on the outgoing interface address.
The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT the Internet traffic coming from a workstation with the IP address 10.0.1.10/24?
A. 10.200.1.10
B. Any available IP address in the WAN (port1) subnet 10.200.1.0/24 66 of 108
C. 10.200.1.1
D. 10.0.1.254
Which three authentication timeout types are availability for selection on FortiGate? (Choose three.)
A. hard-timeout
B. auth-on-demand
C. soft-timeout
D. new-session
E. Idle-timeout
Refer to the exhibit.
The exhibit shows a diagram of a FortiGate device connected to the network and the firewall policy and IP pool configuration on the FortiGate device.
Two PCs, PC1 and PC2, are connected behind FortiGate and can access the internet successfully. However, when the administrator adds a third PC to the network (PC3), the PC cannot connect to the internet.
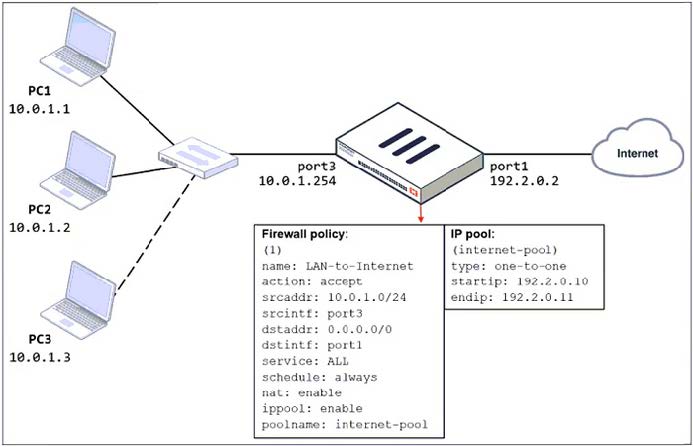
Based on the information shown in the exhibit, which three configuration changes should the administrator make to fix the connectivity issue for PC3? (Choose three.)
A. In the IP pool configuration, set type to overload. Most Voted
B. Configure 192.2.0.12/24 as the secondary IP address on port1.
C. In the firewall policy configuration, disable ippool. Most Voted
D. In the IP pool configuration, set endip to 192.2.0.12. Most Voted
E. Configure another firewall policy that matches only the address of PC3 as source, and then place the policy on top of the list.
