NSE4_FGT-6.2 Online Practice Questions and Answers
An administrator needs to strengthen the security for SSL VPN access. Which of the following statements are best practices to do so? (Choose three.)
A. Configure split tunneling for content inspection.
B. Configure host restrictions by IP or MAC address.
C. Configure two-factor authentication using security certificates.
D. Configure SSL offloading to a content processor (FortiASIC).
E. Configure a client integrity check (host-check).
What FortiGate components are tested during the hardware test? (Choose three.)
A. Administrative access
B. HA heartbeat
C. CPU
D. Hard disk
E. Network interfaces
Which of the following statements about converse mode are true? (Choose two.)
A. FortiGate stops sending files to FortiSandbox for inspection.
B. FortiGate stops doing RPF checks over incoming packets.
C. Administrators cannot change the configuration.
D. Administrators can access the FortiGate only through the console port.
NGFW mode allows policy-based configuration for most inspection rules. Which security profile's configuration does not change when you enable policy-based inspection?
A. Web filtering
B. Antivirus
C. Web proxy
D. Application control
Which of the following statements about policy-based IPsec tunnels are true? (Choose two.)
A. They can be configured in both NAT/Route and transparent operation modes.
B. They support L2TP-over-IPsec.
C. They require two firewall policies: one for each directions of traffic flow.
D. They support GRE-over-IPsec.
An administrator has configured a route-based IPsec VPN between two FortiGate devices. Which statement about this IPsec VPN configuration is true?
A. A phase 2 configuration is not required.
B. This VPN cannot be used as part of a hub-and-spoke topology.
C. A virtual IPsec interface is automatically created after the phase 1 configuration is completed.
D. The IPsec firewall policies must be placed at the top of the list.
What settings must you configure to ensure FortiGate generates logs for web filter activity on a firewall policy called Full Access? (Choose two.)
A. Enable Event Logging.
B. Enable a web filter security profile on the Full Access firewall policy.
C. Enable Log Allowed Traffic on the Full Access firewall policy.
D. Enable disk logging.
Which of the following statements about the FSSO collector agent timers is true?
A. The workstation verify interval is used to periodically check if a workstation is still a domain member.
B. The IP address change verify interval monitors the server IP address where the collector agent is installed, and the updates the collector agent configuration if it changes.
C. The user group cache expiry is used to age out the monitored groups.
D. The dead entry timeout interval is used to age out entries with an unverified status.
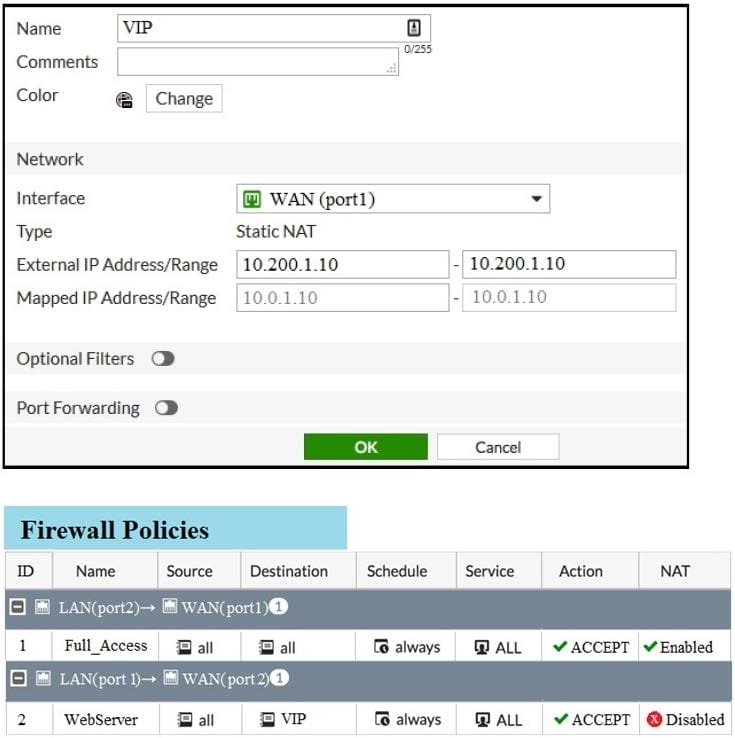
Examine the exhibit, which contains a virtual IP and firewall policy configuration.
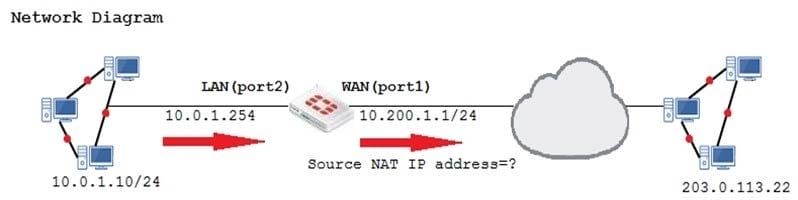
The WAN (port1) interface has the IP address 10.200.1.1/24. The LAN (port2) interface has the IP address
10.0.1.254/24.
The first firewall policy has NAT enabled on the outgoing interface address. The second firewall policy is
configured with a VIP as the destination address.
Which IP address will be used to source NAT the Internet traffic coming from a workstation with the IP
address 10.0.1.10/24?
A. 10.200.1.10
B. Any available IP address in the WAN (port1) subnet 10.200.1.0/24
C. 10.200.1.1
D. 10.0.1.254
Which of the following are purposes of NAT traversal in IPsec? (Choose two.)
A. To detect intermediary NAT devices in the tunnel path.
B. To dynamically change phase 1 negotiation mode aggressive mode.
C. To encapsulation ESP packets in UDP packets using port 4500.
D. To force a new DH exchange with each phase 2 rekey.
Which of the following statements about central NAT are true? (Choose two.)
A. IP tool references must be removed from existing firewall policies before enabling central NAT.
B. Central NAT can be enabled or disabled from the CLI only.
C. Source NAT, using central NAT does not require a central SNAT policy.
D. Destination NAT, using central NAT, requires a VIP object as the destination address in a firewall.
Which two statements about antivirus scanning mode are true? (Choose two.)
A. In proxy-based inspection mode, antivirus buffers the whole file for scanning, before sending it to the client.
B. In full scan flow-based inspection mode, FortiGate buffers the file, but also simultaneously transmits it to the client.
C. In proxy-based inspection mode, files bigger than the buffer size are scanned.
D. In quick scan mode, you can configure antivirus profiles to use any of the available antivirus signature databases.
The FSSO collector agent set to advanced access mode for the Windows Active Directory uses which convention?
A. LDAP
B. Windows
C. RSSO
D. NTLM
Which two statements about virtual domains (VDOMs) are true? (Choose two.)
A. Transparent mode and NAT mode VDOMs cannot be combined on the same FortiGate.
B. Each VDOM can be configured with different system hostnames.
C. Different VLAN subinterfaces of the same physical interface can be assigned to different VDOMs.
D. Each VDOM has its own routing table.
What three FortiGate components are tested during the hardware test? (Choose three.)
A. CPU
B. Administrative access
C. HA heartbeat
D. Hard disk
E. Network interfaces
