NSE4_FGT-6.0 Online Practice Questions and Answers
Which of the following route attributes must be equal for static routes to be eligible for equal cost multipath (ECMP) routing? (Choose two.)
A. Priority
B. Metric
C. Distance
D. Cost
Which statements about DNS filter profiles are true? (Choose two.)
A. They can inspect HTTP traffic.
B. They can redirect blocked requests to a specific portal.
C. They can block DNS requests to known botnet command and control servers.
D. They must be applied in firewall policies with SSL inspection enabled.
Which of the following conditions are required for establishing an IPSec VPN between two FortiGate devices? (Choose two.)
A. If XAuth is enabled as a server in one peer, it must be enabled as a client in the other peer.
B. If the VPN is configured as route-based, there must be at least one firewall policy with the action set to IPSec.
C. If the VPN is configured as DialUp User in one peer, it must be configured as either Static IP Address or Dynamic DNS in the other peer.
D. If the VPN is configured as a policy-based in one peer, it must also be configured as policy-based in the other peer.
An administration wants to throttle the total volume of SMTP sessions to their email server. Which of the following DoS sensors can be used to achieve this?
A. tcp_port_scan
B. ip_dst_session
C. udp_flood
D. ip_src_session
Which of the following statements are best practices for troubleshooting FSSO? (Choose two.)
A. Include the group of guest users in a policy.
B. Extend timeout timers.
C. Guarantee at least 34 Kbps bandwidth between FortiGate and domain controllers.
D. Ensure all firewalls allow the FSSO required ports.
If the Issuer and Subject values are the same in a digital certificate, which type of entity was the certificate issued to?
A. A CRL
B. A person
C. A subordinate CA
D. A root CA
Which of the following statements about the FSSO collector agent timers is true?
A. The workstation verify interval is used to periodically check if a workstation is still a domain member.
B. The IP address change verify interval monitors the server IP address where the collector agent is installed, and the updates the collector agent configuration if it changes.
C. The user group cache expiry is used to age out the monitored groups.
D. The dead entry timeout interval is used to age out entries with an unverified status.
Examine the exhibit, which contains a session diagnostic output.
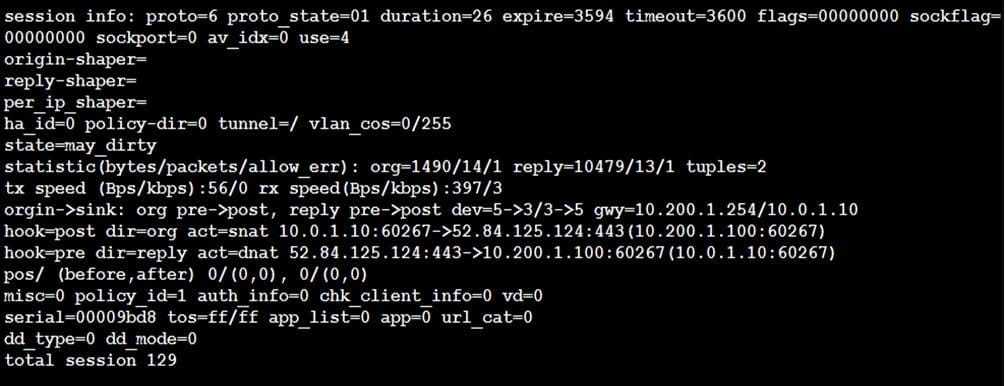
Which of the following statements about the session diagnostic output is true?
A. The session is in ESTABLISHED state.
B. The session is in LISTEN state.
C. The session is in TIME_WAIT state.
D. The session is in CLOSE_WAIT state.
Refer to the following exhibit.
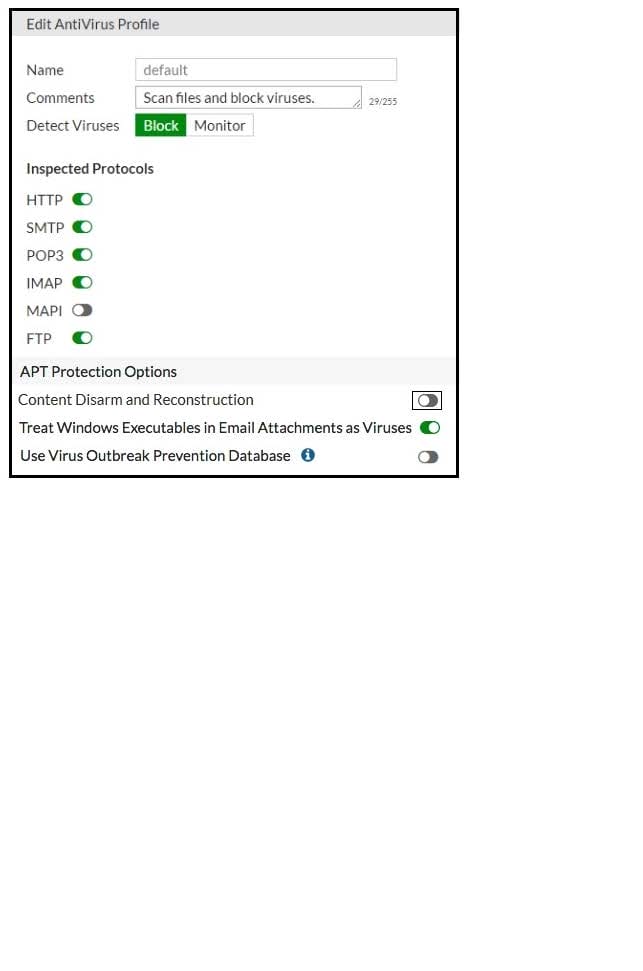
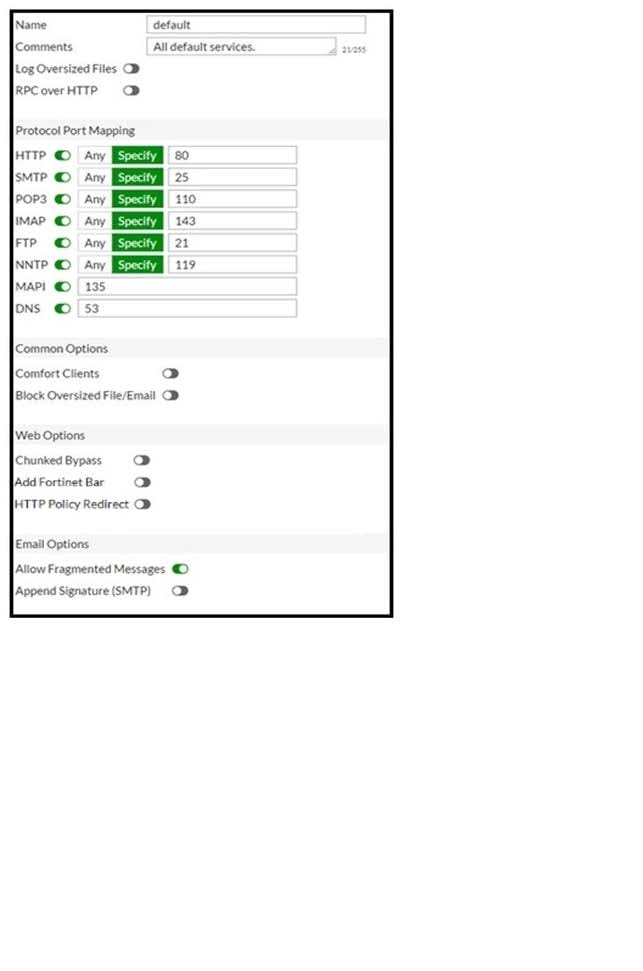
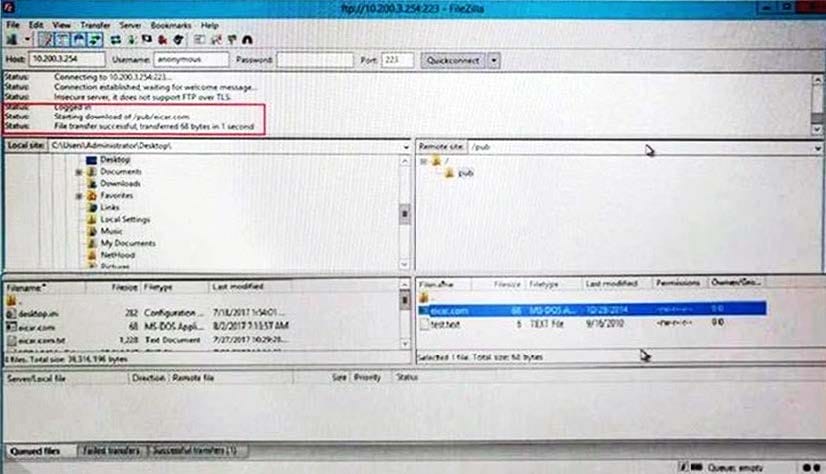
Why is FortiGate not blocking the test file over FTP download?
A. Deep-inspection must be enabled for FortiGate to fully scan FTP traffic.
B. FortiGate needs to be operating in flow-based inspection mode in order to scan FTP traffic.
C. The FortiSandbox signature database is required to successfully scan FTP traffic.
D. The proxy options profile needs to scan FTP traffic on a non-standard port.
An administrator wants to create a policy-based IPsec VPN tunnel betweeb two FortiGate devices. Which configuration steps must be performed on both devices to support this scenario? (Choose three.)
A. Define the phase 1 parameters, without enabling IPsec interface mode
B. Define the phase 2 parameters.
C. Set the phase 2 encapsulation method to transport mode
D. Define at least one firewall policy, with the action set to IPsec.
E. Define a route to the remote network over the IPsec tunnel.
On a FortiGate with a hard disk, how can you upload logs to FortiAnalyzer or FortiManager? (Choose two.)
A. hourly
B. real time
C. on-demand
D. store-and-upload
When using WPAD DNS method, which FQDN format do browsers use to query the DNS server?
A. srv_proxy.
B. srv_tcp.wpad.
C. wpad.
D. proxy.
The FSSO Collector Agent set to advanced access mode for the Windows Active Directory uses which of the following?
A. LDAP convention B. NTLM convention
C. Windows convention ?NetBios\Username
D. RSSO convention
Which is a requirement for creating an inter-VDOM link between two VDOMs?
A. The inspection mode of at least one VDOM must be proxy-based.
B. At least one of the VDOMs must operate in NAT mode.
C. The inspection mode of both VDOMs must match.
D. Both VDOMs must operate in NAT mode.
Which of the following static routes are not maintained in the routing table?
A. Named Address routes
B. Dynamic routes
C. ISDB routes
D. Policy routes
