NSE4-5.4 Online Practice Questions and Answers
Which of the following statements best describes how the collector agent learns that a user has logged off from the network?
A. The workstation fails to reply to the polls frequently done by the collector agent.
B. The DC agent captures the log off event from the event logs, which it forwards to the collector agent.
C. The work station notifies the DC agent that the user has logged off.
D. The collector agent gets the logoff events when polling the respective domain controller.
If you enable the option "Generate Logs when Session Starts", what effect does this have on the number of traffic log messages generated for each session?
A. No traffic log message is generated.
B. One traffic log message is generated.
C. Two traffic log messages are generated.
D. A log message is only generated if there is a security event.
Which of the following IKE modes is the one used during the IPsec phase 2 negotiation?
A. Aggressive mode
B. Quick mode
C. Main mode
D. Fast mode
Which portion of the configuration does an administrator specify the type of IPsec configuration (either policy-based or route-based)?
A. Under the IPsec VPN global settings.
B. Under the phase 2 settings.
C. Under the phase 1 settings.
D. Under the firewall policy settings.
Examine this log entry. What does the log indicate? (Choose three.)
date=2013-12-04 time=09:30:18 logid=0100032001 type=event subtype=system level=information vd="root" user="admin" ui=http(192.168.1.112) action=login status=success reason=none profile="super_admin" msg="Administrator admin logged in successfully from http(192.168.1.112)"
A. In the GUI, the log entry was located under "Log and Report > Event Log > User".
B. In the GUI, the log entry was located under "Log and Report > Event Log > System".
C. In the GUI, the log entry was located under "Log and Report > Traffic Log > Local Traffic".
D. The connection was encrypted.
E. The connection was unencrypted.
F. The IP of the FortiGate interface that "admin" connected to was 192.168.1.112.
G. The IP of the computer that "admin" connected from was 192.168.1.112.
Which of the following statements are correct regarding virtual domains (VDOMs)? (Select all that apply.)
A. VDOMs divide a single FortiGate unit into two or more virtual units that function as multiple, independent units.
B. A management VDOM handles SNMP, logging, alert email, and FDN-based updates.
C. VDOMs share firmware versions, as well as antivirus and IPS databases.
D. Only administrative users with a 'super_admin' profile will be able to enter multiple VDOMs to make configuration changes.
A new version of FortiOS firmware has just been released. When you upload new firmware, which is true?
A. If you upload the firmware image via the boot loader's menu from a TFTP server, it will not preserve the configuration. But if you upload new firmware via the GUI or CLI, as long as you are following a supported upgrade path, FortiOS will attempt to convert the existing configuration to be valid with any new or changed syntax.
B. No settings are preserved. You must completely reconfigure.
C. No settings are preserved. After the upgrade, you must upload a configuration backup file. FortiOS will ignore any commands that are not valid in the new OS. In those cases, you must reconfigure settings that are not compatible with the new firmware.
D. You must use FortiConverter to convert a backup configuration file into the syntax required by the new FortiOS, then upload it to FortiGate.
Which are valid replies from a RADIUS server to an ACCESS-REQUEST packet from a FortiGate? (Choose two.)
A. ACCESS-CHALLENGE
B. ACCESS-RESTRICT
C. ACCESS-PENDING
D. ACCESS-REJECT
A FortiGate unit has multiple VDOMs in NAT/route mode with multiple VLAN interfaces in each VDOM. Which of the following statements is correct regarding the IP addresses assigned to each VLAN interface?
A. Different VLANs can share the same IP address as long as they have different VLAN IDs.
B. Different VLANs can share the same IP address as long as they are in different physical interface.
C. Different VLANs can share the same IP address as long as they are in different VDOMs.
D. Different VLANs can never share the same IP addresses.
An administrator wants to create an IPsec VPN tunnel between two FortiGate devices. Which three configuration steps must be performed on both units to support this scenario? (Choose three.)
A. Create firewall policies to allow and control traffic between the source and destination IP addresses.
B. Configure the appropriate user groups to allow users access to the tunnel.
C. Set the operating mode to IPsec VPN mode.
D. Define the phase 2 parameters.
E. Define the Phase 1 parameters.
Which of the following are valid FortiGate device interface methods for handling DNS requests? (Select all that apply.)
A. Forward-only
B. Non-recursive
C. Recursive
D. Iterative
E. Conditional-forward
View the exhibit.
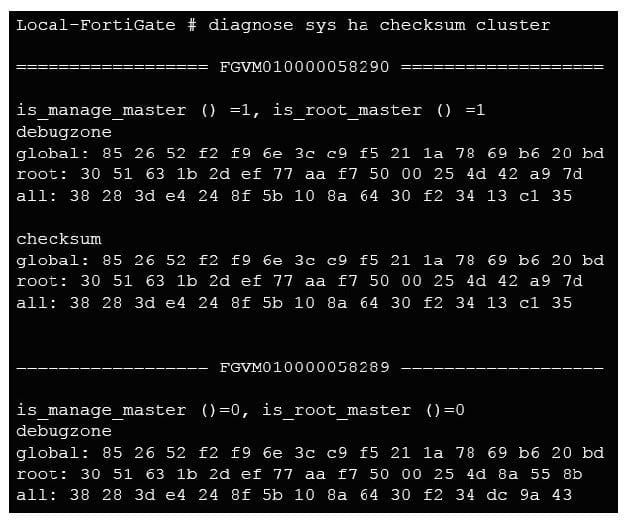
Which statements are correct, based on this output? (Choose two.)
A. The FortiGate have three VDOMs.
B. The all VDOM is not synchronized between the primary and secondary FortiGate.
C. The global configuration is synchronized between the primary and secondary FortiGate.
D. The root VDOM is not synchronized between the primary and secondary FortiGate.
Review the IPsec phase 2 configuration shown in the exhibit; then answer the question below.
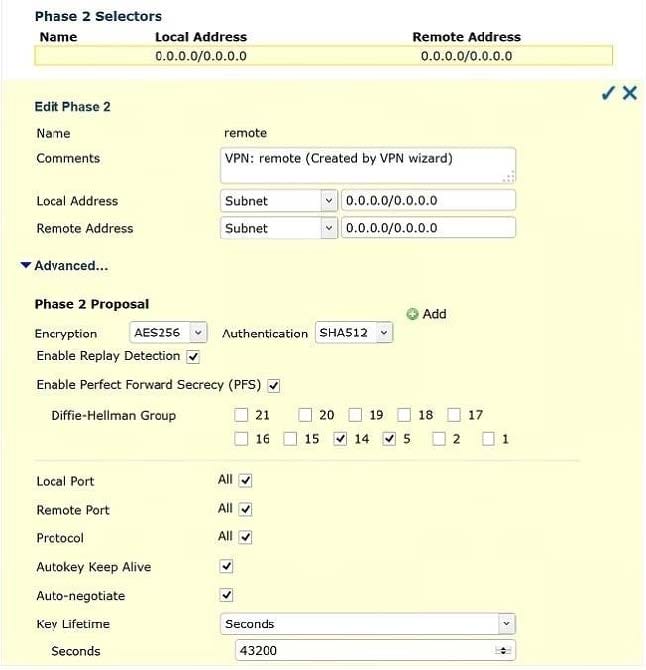
Which statements are correct regarding this configuration? (Choose two.).
A. The Phase 2 will re-key even if there is no traffic.
B. There will be a DH exchange for each re-key.
C. The sequence number of ESP packets received from the peer will not be checked.
D. Quick mode selectors will default to those used in the firewall policy.
An administrator has configured a route-based IPsec VPN between two FortiGates. Which statement about this IPsec VPN configuration is true?
A. A phase 2 configuration is not required.
B. This VPN cannot be used as part of a hub and spoke topology.
C. The IPsec firewall policies must be placed at the top of the list.
D. A virtual IPsec interface is automatically created after the phase 1 configuration is completed.
View the Exhibit.

The administrator needs to confirm that FortiGate 2 is properly routing that traffic to the 10.0.1.0/24 subnet. The administrator needs to confirm it by sending ICMP pings to FortiGate 2 from the CLI of FortiGate 1. What ping option needs to be enabled before running the ping?
A. Execute ping-options source port1
B. Execute ping-options source 10.200.1.1.
C. Execute ping-options source 10.200.1.2
D. Execute ping-options source 10.0.1.254
