MS-101 Online Practice Questions and Answers
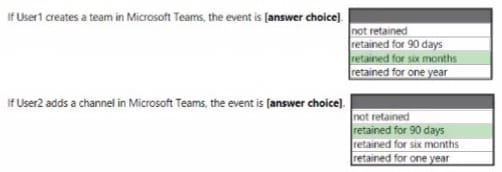
HOTSPOT
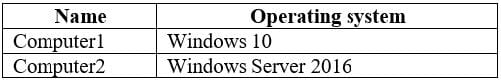
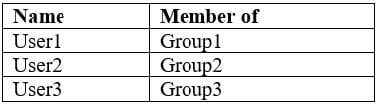
You have a Microsoft Azure Activity Directory (Azure AD) tenant contains the users shown in the following table.
Group3 is a member of Group1.
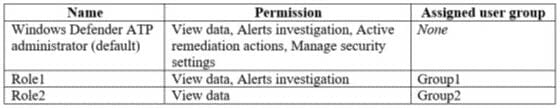
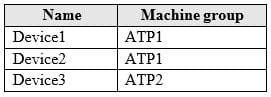
Your company uses Windows Defender Advanced Threat Protection (ATP). Windows Defender ATP contains the roles shown in the following table.
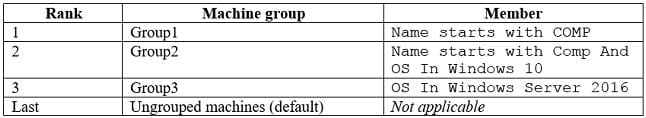
Windows Defender ATP contains the device groups shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
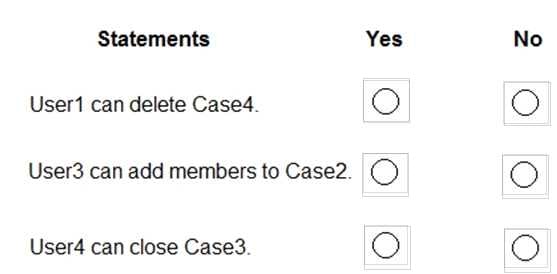
HOTSPOT
Your company uses Windows Defender Advanced Threat Protection (ATP). Windows Defender ATP contains the device groups shown in the following table.

You onboard computers to Windows Defender ATP as shown in the following table.

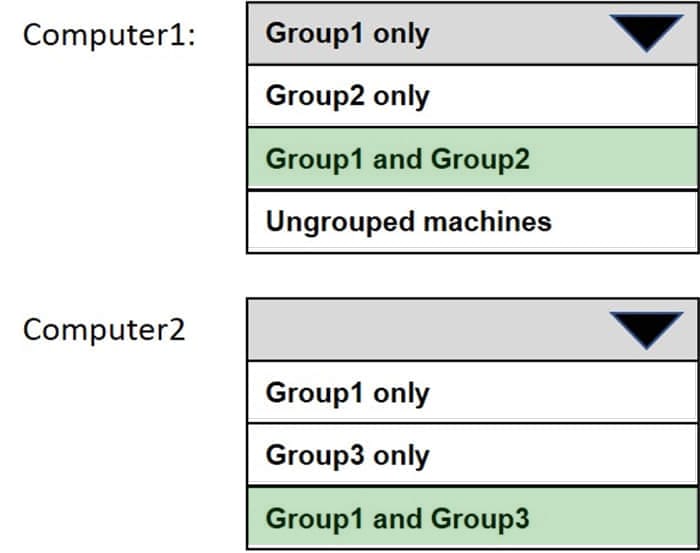
Of which groups are Computer1 and Computer2 members? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
HOTSPOT
You have a Microsoft 365 subscription.
You are configuring permissions for Security and Compliance.
You need to ensure that the users can perform the tasks shown in the following table.

The solution must use the principle of least privilege.
To which role should you assign each user? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
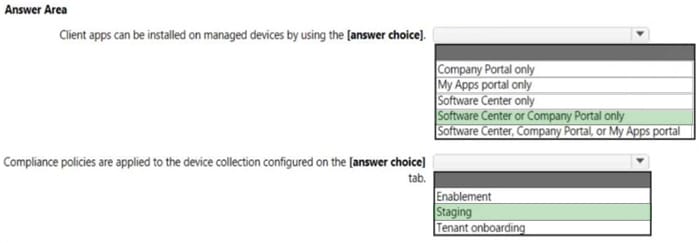
HOTSPOT
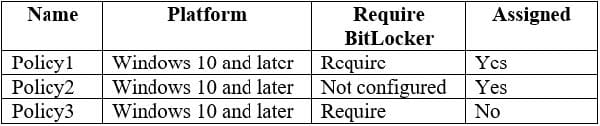
You have three devices enrolled in Microsoft Intune as shown in the following table.
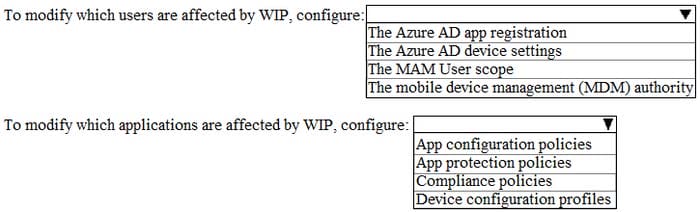
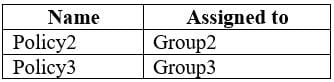
The device compliance policies in Intune are configured as shown in the following table.
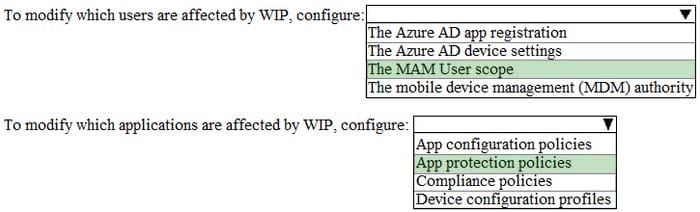
The device compliance policies have the assignments shown in the following table.
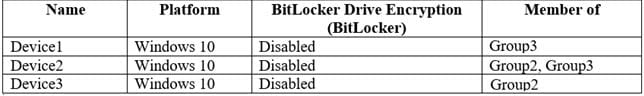
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
HOTSPOT
Your company uses Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP).
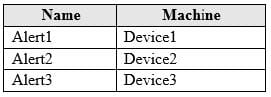
The devices onboarded to Microsoft Defender ATP are shown in the following table.
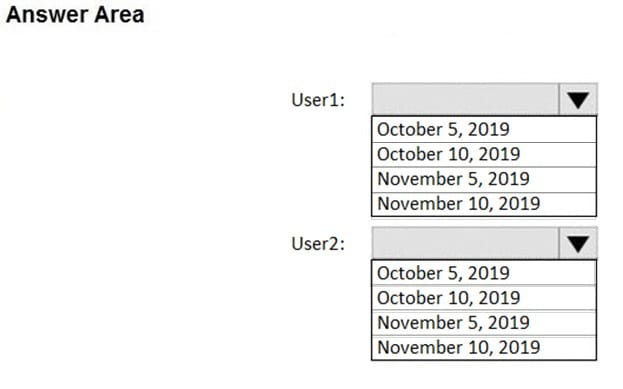
The alerts visible in the Microsoft Defender ATP alerts queue are shown in the following table.
You create a suppression rule that has the following settings:
1.
Triggering IOC: Any IOC
2.
Action: Hide alert
3.
Suppression scope: Alerts on ATP1 machine group
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
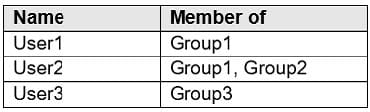
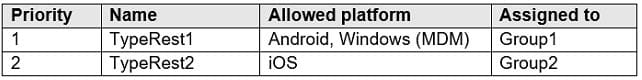
HOTSPOT
You have a Microsoft 365 subscription that contains the users in the following table.
In Microsoft Endpoint Manager, you create two device type restrictions that have the settings shown in the following table.
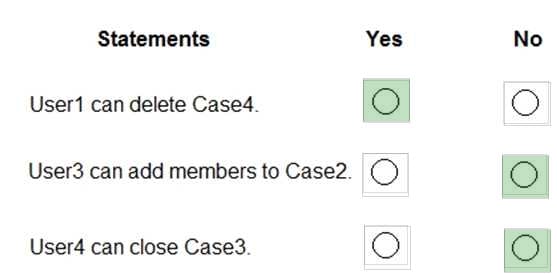
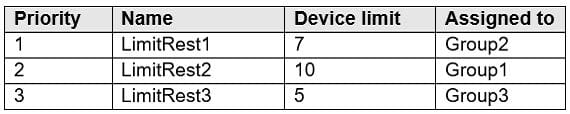
In Microsoft Endpoint Manager, you create three device limit restrictions that have the settings shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
HOTSPOT
You have a Microsoft 365 E5 tenant.
You need to ensure that administrators are notified when a user receives an email message that contains malware. The solution must use the principle of least privilege.
Which type of policy should you create and which Microsoft 365 compliance center role is required to create the pokey? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
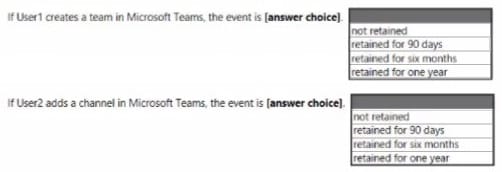
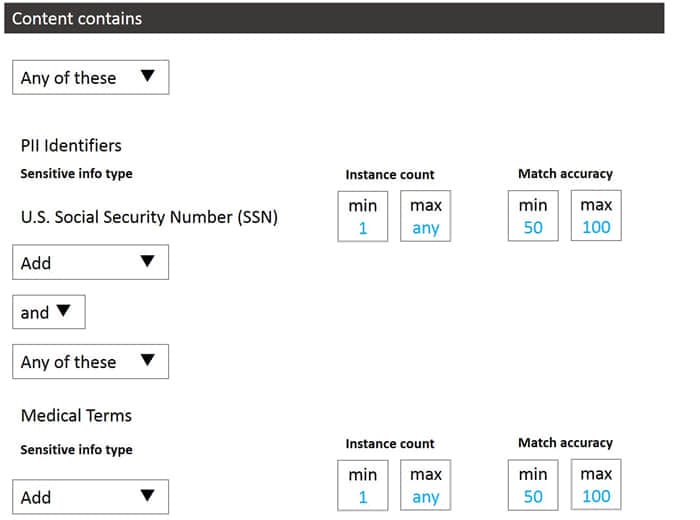
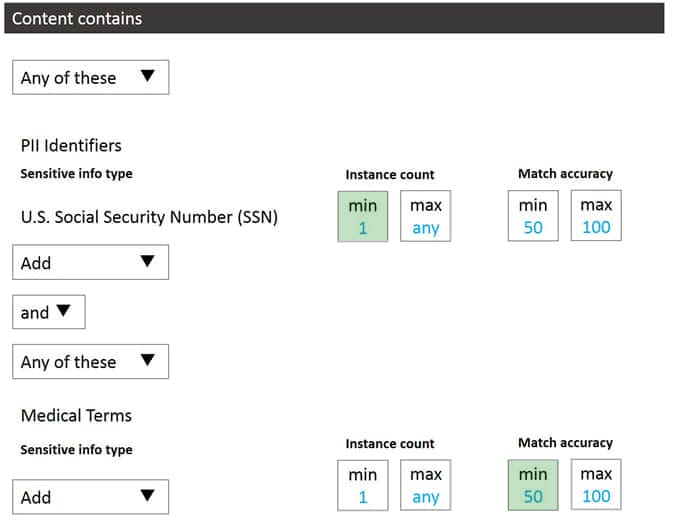
HOTSPOT
You need to configure a conditional access policy to meet the compliance requirements.
You add Exchange Online as a cloud app.
Which two additional settings should you configure in Policy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

You have a Microsoft 365 subscription.
You need to investigate user activity in Microsoft 365, including from where users signed in, which applications were used, and increases in activity during the past month. The solution must minimize administrative effort.
Which admin center should you use?
A. Azure ATP
B. Security and Compliance
C. Cloud App Security
D. Flow
You have a Microsoft 365 subscription.
You plan to enable Microsoft Azure Information Protection.
You need to ensure that only the members of a group named PilotUsers can protect content.
What should you do?
A. From the AADRM PowerShell module, run the Set-AadrmOnboardingControlPolicy cmdlet.
B. From Azure Information Protection, create a policy.
C. From the AADRM PowerShell module, run the Set-AadrmRoleBasedAdministrator cmdlet.
D. From Azure Information Protection, configure the protection activation status.
You have an Azure Active Directory (Azure AD) tenant and a Microsoft 365 E5 subscription. The tenant contains the users shown in the following table.

You plan to implement Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP).
You verify that role-based access control (RBAC) is turned on in Microsoft Defender ATP.
You need to identify which user can view security incidents from the Microsoft Defender Security Center.
Which user should you identify?
A. User1
B. User2
C. User3
D. User4
You have two conditional access policies named Policy1 and Policy2.
Policy1 has the following settings:
Assignments:
-Users and groups: User1
-Cloud apps or actions: Office 365 Exchange Online
-Conditions: 0 conditions selected Access controls:
-Grant: Grant access
-Session: 0 controls selected Enable policy: On
Policy2 has the following settings: Assignments:
-Users and groups: User1
-Cloud apps or actions: Office 365 Exchange Online
-Conditions: 0 conditions selected Access controls:
-Grant: Block access
-Session: 0 controls selected Enable policy: On
You need to ensure that User1 can access Microsoft Exchange Online only from devices that are marked as compliant. What should you do?
A. Modify the Grant settings of Policy2.
B. Disable Policy2.
C. Modify the Conditions settings of Policy2.
D. Modify the Grant settings of Policy1.
You have a Microsoft 365 tenant that contains 500 Windows 10 devices and a Microsoft Endpoint Manager device compliance policy.
You need to ensure that only devices marked as compliant can access Microsoft Office 365 apps.
Which policy type should you configure?
A. conditional access
B. account protection
C. attack surface reduction (ASR)
D. Endpoint detection and response
You have a Microsoft 365 E5 subscription that contains the devices shown in the following table.
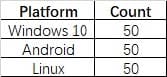
You need to configure an incident email notification rule that will be triggered when an alert occurs only on a Windows 10 device. The solution must minimize administrative effort. What should you do first?
A. From the Microsoft 365 admin center, create a mail-enabled security group.
B. From the Microsoft 365 Defender portal, create a device group.
C. From the Microsoft Endpoint Manager admin center, create a device category.
D. From the Azure Active Directory admin center, create a dynamic device group.
You need to configure the compliance settings to meet the technical requirements. What should you do in the Microsoft Endpoint Manager admin center?
A. From Compliance policies, modify the Notifications settings.
B. From Locations, create a new location for noncompliant devices.
C. From Retire Noncompliant Devices, select Clear All Devices Retire State.
D. Modify the Compliance policy settings.