JN0-634 Online Practice Questions and Answers
Click the Exhibit button.
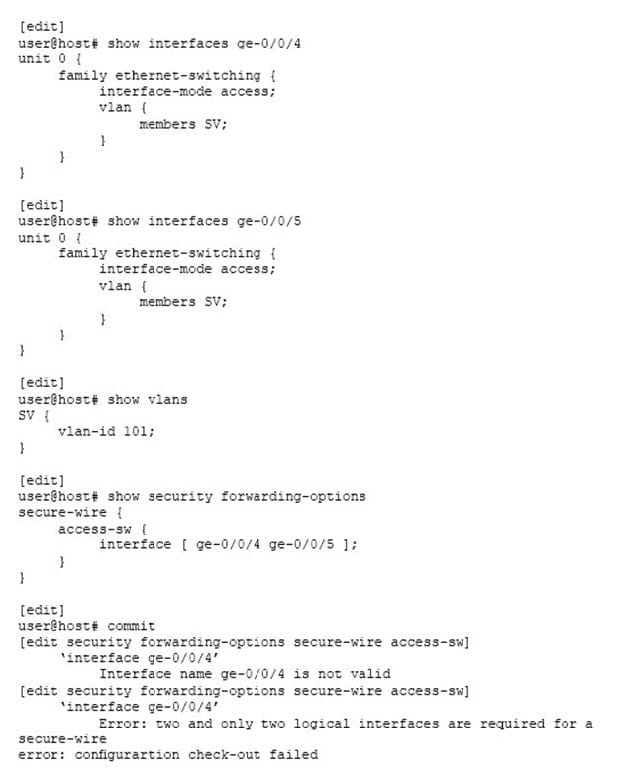
You are trying to implement secure wire on your SRX Series device. However, you are receiving the commit error shown in the exhibit.
What must you do to solve the problem?
A. Add the correct logical units to the interfaces in the secure wire.
B. Put the ge-0/0/4 and ge-0/0/5 interfaces in separate secure wires.
C. Change the Ethernet switching mode from access to trunk for the ge-0/0/4 and ge-0/0/5 interfaces.
D. Add the ge-0/0/4 and ge-0/0/5 interfaces to the SV VLAN.
Which three components are part of the AppSecure services suite? (Choose three.)
A. IDP
B. Sky ATP
C. AppQoS
D. AppFW
E. Web filtering
While reviewing the Log and Reporting portion of Security Director, you find that multiple objects reference the same address. You want to use a standardized name for all of the objects.
In this scenario, how would you create a standardized object name without searching the entire policy?
A. Remove the duplicate objects.
B. Merge the duplicate objects.
C. Rename the duplicate objects.
D. Replace the duplicate objects.
A customer has recently deployed a next-generation firewall, sandboxing software, cloud access security brokers (CASB), and endpoint protection.
In this scenario, which tool would provide the customer with additional attack prevention?
A. Junos Space Cross Provisioning Platform
B. Contrail
C. Security Director Policy Enforcer
D. Network Director Inventory Manager
Click the Exhibit button.
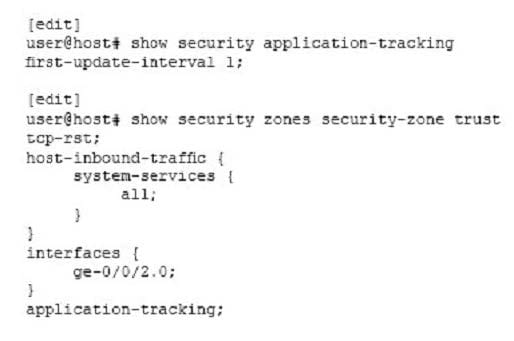
Referring to the exhibit, how many AppTrack logs will be generated for an HTTP session lasting 12 minutes?
A. 4
B. 2
C. 1
D. 3
The Software-Defined Secure Networks Policy Enforcer contains which two components? (Choose two.)
A. SRX Series device
B. Sky ATP
C. Policy Controller
D. Feed Connector
Click the Exhibit button.
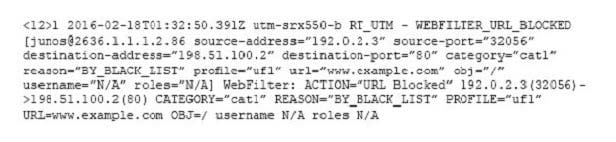
A customer submits a service ticket complaining that access to http://www.example.com/ has been blocked.
Referring to the log message shown in the exhibit, why was access blocked?
A. All illegal source port was utilized.
B. The URI matched a profile entry.
C. The user/role permissions were exceeded.
D. There was a website category infraction.
Click the Exhibit button.
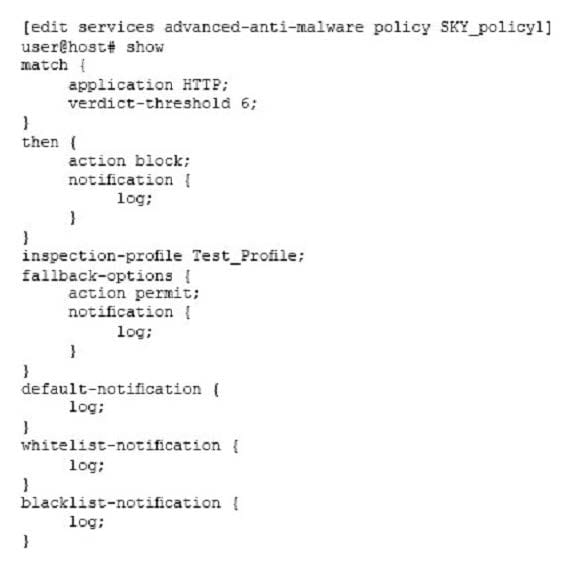
Referring to the exhibit, you have configured a Sky ATP policy to inspect user traffic. However, you have noticed that encrypted traffic is not being inspected.
In this scenario, what must you do to solve this issue?
A. Change the policy to inspect HTTPS traffic.
B. Configure the PKI feature.
C. Configure the SSL forward proxy feature.
D. Change the policy to inspect TLS traffic.
