JN0-334 Online Practice Questions and Answers
Which two statements are true about virtualized SRX Series devices? (Choose two.)
A. vSRX cannot be deployed in transparent mode.
B. cSRX can be deployed in routed mode.
C. cSRX cannot be deployed in routed mode.
D. vSRX can be deployed in transparent mode.
You want to deploy vSRX in Amazon Web Services (AWS) virtual private clouds (VPCs). Which two statements are true in this scenario? (Choose two.)
A. The vSRX devices serving as local enforcement points for VPCs can be managed by a centralized Junos Space Network Director instance.
B. MPLS LSPs can be used to connect vSRXs in different VPCs.
C. IPsec tunnels can be used to connect vSRX in different VPCs.
D. The vSRX devices serving as local enforcement points for VPCs can be managed by a centralized Junos Space Security Director instance.
Which two solutions provide a sandboxing feature for finding zero-day malware threats? (Choose two.)
A. Sky ATP
B. UTM
C. JATP
D. IPS
You want to use Sky ATP to protect your network; however, company policy does not allow you to send any files to the cloud.
Which Sky ATP feature should you use in this situation?
A. Only use on-premises local Sky ATP server anti-malware file scanning.
B. Only use cloud-based Sky ATP file hash lookups.
C. Only use on-box SRX anti-malware file scanning.
D. Only use cloud-based Sky ATP file blacklists.
Click the Exhibit button.
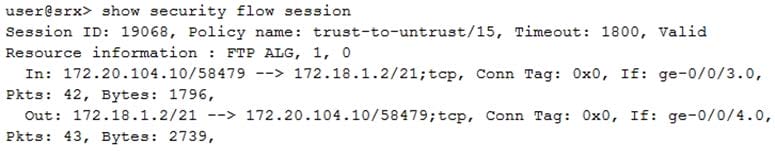
Which two statements are true about the session shown in the exhibit? (Choose two.)
A. Two security policies are required for bidirectional traffic flow.
B. The ALG was enabled by manual configuration.
C. The ALG was enabled by default.
D. One security policy is required for bidirectional traffic flow.
You are troubleshooting advanced policy-based routing (APBR). Which two actions should you perform in this scenario? (Choose two.)
A. Verify that the APBR profiles are applied to the egress zone.
B. Verity inet.0 for correct route leaking.
C. Review the APBR statistics for matching rules and route modifications.
D. Inspect the application system cache for the application entry.
You want to support reth LAG interfaces on a chassis cluster.
What must be enabled on the interconnecting switch to accomplish this task?
A. RSTP
B. 802.3ad
C. LLDP
D. swfab
Which three statements are correct about fabric interfaces on the SRX5800? (Choose three.)
A. Fabric interfaces must be user-assigned interfaces.
B. Fabric interfaces must have a user-assigned IP address.
C. Fabric interfaces must be same interface type.
D. Fabric interfaces must be on the same Layer 2 segment.
E. Fabric interfaces must be system-assigned interfaces.
