JN0-333 Online Practice Questions and Answers
Click the Exhibit button.
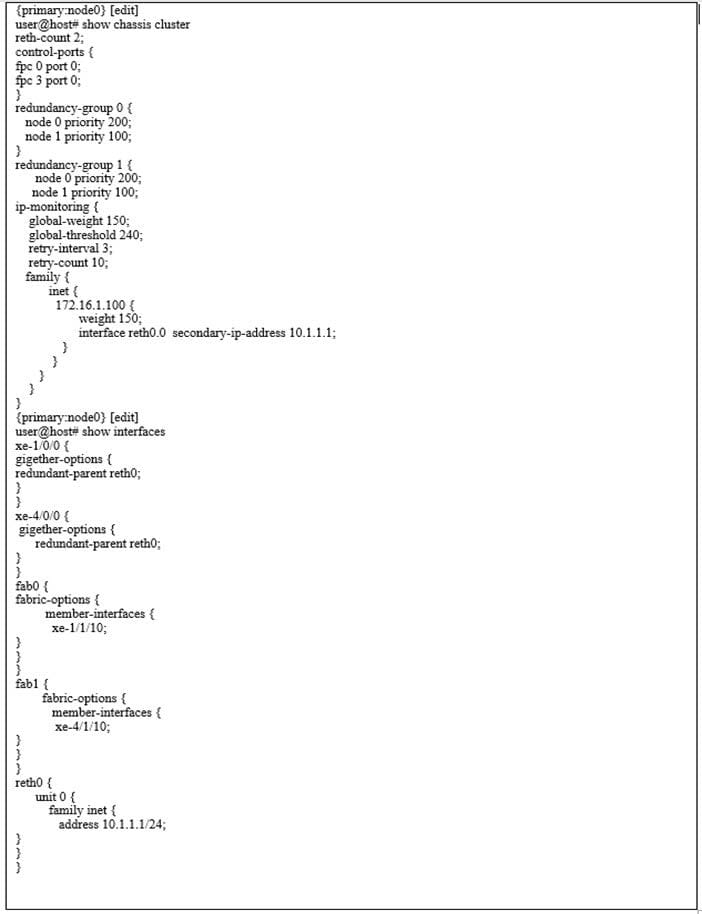
Which statement would explain why the IP-monitoring feature is functioning incorrectly?
A. The global weight value is too large for the configured global threshold.
B. The secondary IP address should be on a different subnet than the reth IP address.
C. The secondary IP address is the same as the reth IP address.
D. The monitored IP address is not on the same subnet as the reth IP address.
Which statement describes the function of screen options?
A. Screen options encrypt transit traffic in a tunnel.
B. Screen options protect against various attacks on traffic entering a security device.
C. Screen options translate a private address to a public address.
D. Screen options restrict or permit users individually or in a group.
Which interface is used exclusively to forward Ethernet-switching traffic between two chassis cluster nodes?
A. swfab0
B. fxp0
C. fab0
D. me0
You are asked to support source NAT for an application that requires that its original source port not be changed.
Which configuration would satisfy the requirement?
A. Configure a source NAT rule that references an IP address pool with interface proxy ARP enabled.
B. Configure the egress interface to source NAT fixed-port status.
C. Configure a source NAT rule that references an IP address pool with the port no-translation parameter enabled.
D. Configure a source NAT rule that sets the egress interface to the overload status.
You are changing the default vCPU allocation on a vSRX. How are the additional vCPUs allocated in this scenario?
A. The vCPU are allocated equally across the Junos control plane and packet forwarding engine.
B. One dedicated vCPU is allocated for the Junos control plane and the remaining vCPUs for the packet forwarding engine.
C. One dedicated vCPU is allocated for the packet forwarding engine, one for the Junos control plane, and the remaining vCPUs are equally balanced.
D. One dedicated vCPU is allocated for the packet forwarding engine and the remaining vCPUs for the Junos plane.
Which action will restrict SSH access to an SRX Series device from a specific IP address which is connected to a security zone named trust?
A. Implement a firewall filter on the security zone trust.
B. Implement a security policy from security zone junos-host to security zone trust.
C. Implement host-inbound-traffic system-services to allow SSH.
D. Implement a security policy from security zone trust to security zone junos-host.
Click the Exhibit button.
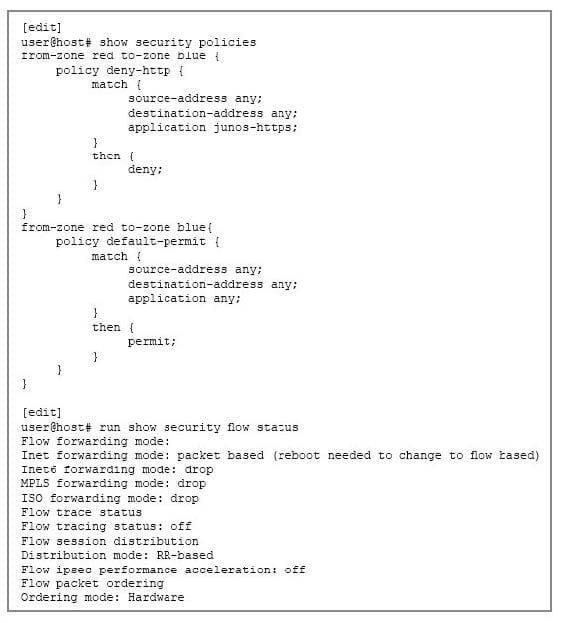
You notice that your SRX Series device is not blocking HTTP traffic as expected. Referring to the exhibit, what should you do to solve the problem?
A. Commit the configuration.
B. Reboot the SRX Series device.
C. Configure the SRX Series device to operate in packet-based mode.
D. Move the deny-http policy to the bottom of the policy list.
Which type of VPN provides a secure method of transporting encrypted IP traffic?
A. IPsec
B. Layer 3 VPN
C. VPLS
D. Layer 2 VPN
