IDENTITY-AND-ACCESS-MANAGEMENT-DESIGNER Online Practice Questions and Answers
Universal containers(UC) has decided to build a new, highly sensitive application on Force.com platform. The security team at UC has decided that they want users to provide a fingerprint in addition to username/ Password to authenticate to this application. How can an architect support fingerprints as a form of identification for salesforce Authentication?
A. Use salesforce Two-factor Authentication with callouts to a third-party fingerprint scanning application.
B. Use Delegated Authentication with callouts to a third-party fingerprint scanning application.
C. Use an appexchange product that does fingerprint scanning with native salesforce identity confirmation.
D. Use custom login flows with callouts to a third-party fingerprint scanning application.
Universal Containers (UC) has a strict requirement to authenticate users to Salesforce using their mainframe credentials. The mainframe user store cannot be accessed from a SAML provider. UC would also like to have users in Salesforce created on the fly if they provide accurate mainframe credentials.
How can the Architect meet these requirements?
A. Use a Salesforce Login Flow to call out to a web service and create the user on the fly.
B. Use the SOAP API to create the user when created on the mainframe; implement Delegated Authentication.
C. Implement Just-In-Time Provisioning on the mainframe to create the user on the fly.
D. Implement OAuth User-Agent Flow on the mainframe; use a Registration Handler to create the user on the fly.
Universal containers wants to build a custom mobile app connecting to salesforce using Oauth, and would like to restrict the types of resources mobile users can access. What Oauth feature of Salesforce should be used to achieve the goal?
A. Access Tokens
B. Mobile pins
C. Refresh Tokens
D. Scopes
Northern Trail Outfitters (NTO) uses Salesforce Experience Cloud sites (previously known as Customer Community) to provide a digital portal where customers can login using their Google account.
NTO would like to automatically create a case record for first time users logging into Salesforce Experience Cloud.
What should an Identity architect do to fulfill the requirement?
A. Configure an authentication provider for Social Login using Google and a custom registration handler.
B. Implement a Just-in-Time handler class that has logic to create cases upon first login.
C. Create an authentication provider for Social Login using Google and leverage standard registration handler.
D. Implement a login flow with a record create component for Case.
Universal Containers (UC) wants to integrate a third-party Reward Calculation system with Salesforce to calculate Rewards. Rewards will be calculated on a schedule basis and update back into Salesforce. The integration between Salesforce and the Reward Calculation System needs to be secure. Which are two recommended practices for using OAuth flow in this scenario. choose 2 answers
A. OAuth Refresh Token FLow
B. OAuth Username-Password Flow
C. OAuth SAML Bearer Assertion FLow
D. OAuth JWT Bearer Token FLow
An architect needs to advise the team that manages the identity provider how to differentiate salesforce from other service providers. What SAML SSO setting in salesforce provides this capability?
A. Entity id
B. Issuer
C. Identity provider login URL
D. SAML identity location
A financial enterprise is planning to set up a user authentication mechanism to login to the Salesforce system. Due to regulatory requirements, the CIO of the company wants user administration, including passwords and authentication requests, to be managed by an external system that is only accessible via a SOAP webservice.
Which authentication mechanism should an identity architect recommend to meet the requirements?
A. OAuth Web-Server Flow
B. Identity Connect
C. Delegated Authentication
D. Just-in-Time Provisioning
Universal Containers (UC) uses middleware to integrate multiple systems with Salesforce. UC has a strict, new requirement that usernames and passwords cannot be stored in any UC system. How can UC's middleware authenticate to Salesforce while adhering to this requirement?
A. Create a Connected App that supports the JWT Bearer Token OAuth Flow.
B. Create a Connected App that supports the Refresh Token OAuth Flow
C. Create a Connected App that supports the Web Server OAuth Flow.
D. Create a Connected App that supports the User-Agent OAuth Flow.
In a typical SSL setup involving a trusted party and trusting party, what consideration should an Architect take into account when using digital certificates?
A. Use of self-signed certificate leads to lower maintenance for trusted party because multiple self-signed certs need to be maintained.
B. Use of self-signed certificate leads to higher maintenance for trusted party because they have to act as the trusted CA
C. Use of self-signed certificate leads to lower maintenance for trusting party because there is no trusted CA cert to maintain.
D. Use of self-signed certificate leads to higher maintenance for trusting party because the cert needs to be added to their truststore.
A financial services company uses Salesforce and has a compliance requirement to track information about devices from which users log in. Also, a Salesforce Security Administrator needs to have the ability to revoke the device from which users log in.
What should be used to fulfill this requirement?
A. Use multi-factor authentication (MFA) to meet the compliance requirement to track device information.
B. Use the Activations feature to meet the compliance requirement to track device information.
C. Use the Login History object to track information about devices from which users log in.
D. Use Login Flows to capture device from which users log in and store device and user information in a custom object.
What information does the 'Relaystate' parameter contain in sp-Initiated Single Sign-on?
A. Reference to a URL redirect parameter at the identity provider.
B. Reference to a URL redirect parameter at the service provider.
C. Reference to the login address URL of the service provider.
D. Reference to the login address URL of the identity Provider.
What are three capabilities of Delegated Authentication? Choose 3 answers
A. It can be assigned by Custom Permissions.
B. It can connect to SOAP services.
C. It can be assigned by Permission Sets.
D. It can be assigned by Profiles.
E. It can connect to REST services.
Which three types of attacks would a 2-Factor Authentication solution help garden against?
A. Key logging attacks
B. Network perimeter attacks
C. Phishing attacks
D. Dictionary attacks
E. Man-in-the-middle attacks
An organization has a central cloud-based Identity and Access Management (IAM) Service for
authentication and user management, which must be utilized by all applications as follows:
1 - Change of a user status in the central IAM Service triggers provisioning or deprovisioining in the
integrated cloud applications.
2 - Security Assertion Markup Language single sign-on (SSO) is used to facilitate access for users
authenticated at identity provider (Central IAM Service).
Which approach should an IAM architect implement on Salesforce Sales Cloud to meet the requirements?
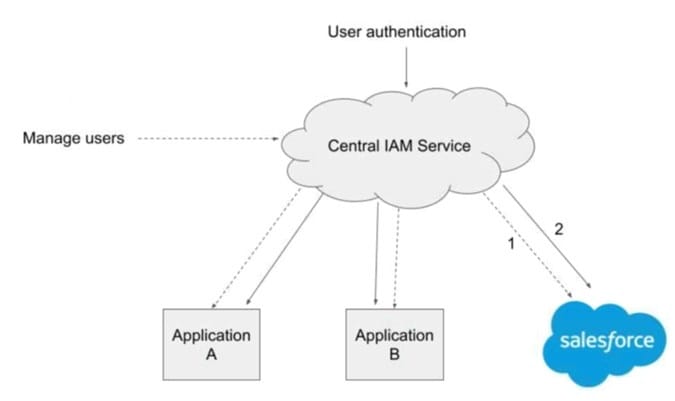
A. A Configure Salesforce as a SAML Service Provider, and enable SCIM (System for Cross-Domain Identity Management) for provisioning and deprovisioning of users.
B. Configure Salesforce as a SAML service provider, and enable Just-in Time (JIT) provisioning and deprovisioning of users.
C. Configure central IAM Service as an authentication provider and extend registration handler to manage provisioning and deprovisioning of users.
D. Deploy Identity Connect component and set up automated provisioning and deprovisioning of users, as well as SAML-based SSO.
A manufacturer wants to provide registration for an Internet of Things (IoT) device with limited display input or capabilities.
Which Salesforce OAuth authorization flow should be used?
A. OAuth 2.0 JWT Bearer How
B. OAuth 2.0 Device Flow
C. OAuth 2.0 User-Agent Flow
D. OAuth 2.0 Asset Token Flow
