HPE6-A68 Online Practice Questions and Answers
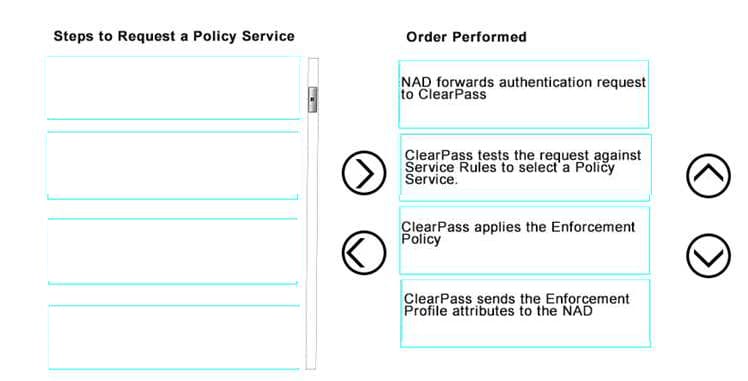
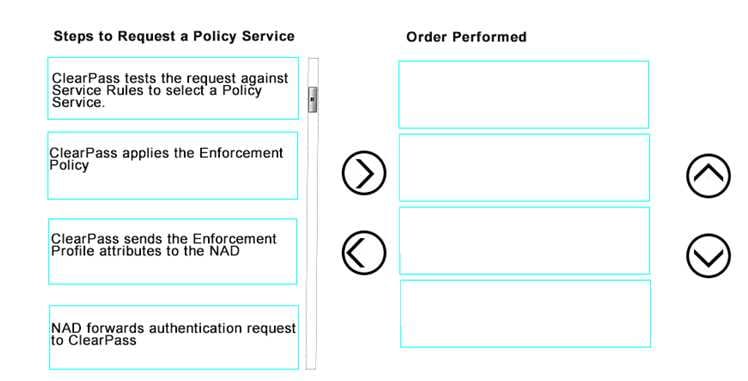
DRAG DROP
Use the arrows to sort the steps to request a Policy Service on the left into the order they are performed on the right.
Select and Place:
Refer to the exhibit.
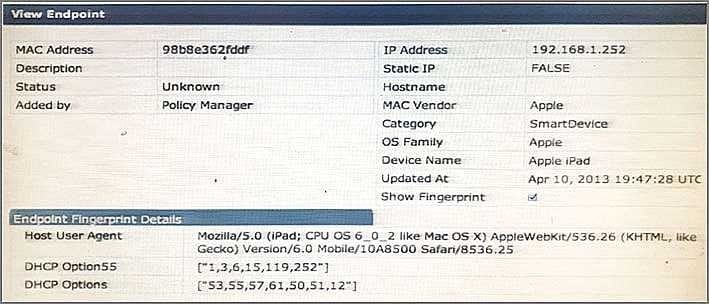
Based on the Endpoint information shown, which collectors were used to profile the device as Apple iPad? (Select two.)
A. HTTP User-Agent
B. SNMP
C. DHCP fingerprinting
D. SmartDevice
E. Onguard Agent
ClearPass and a wired switch are configured for 802.1x authentication with RADIUS CoA (RFC 3576) on UDP port 3799. This port has been blocked by a firewall between the wired switch and ClearPass. What will be the outcome of this state?
A. RADIUS Authentications will fail because the wired switch will not be able to reach the ClearPass server.
B. During RADIUS Authentication, certificate exchange between the wired switch and ClearPass will fail.
C. RADIUS Authentications will timeout because the wired switch will not be able to reach the ClearPass server.
D. RADIUS Authentication will succeed, but Post-Authentication Disconnect-Requests from ClearPass to the wired switch will not be delivered.
E. RADIUS Authentication will succeed, but RADIUS Access-Accept messages from ClearPass to the wired switch for Change of Role will not be delivered.
An employee provisions a personal smart phone using the Onboard process. In addition, the employee has a corporate laptop provided by IT that connects to the secure network. How many licenses does the employee consume?
A. 1 Policy Manager license, 2 Guest Licenses
B. 2 Policy Manager licenses, 1 Onboard License
C. 1 Policy Manager license, 1 Onboard License
D. 1 Policy Manager license, 1 Guest License
E. 2 Policy Manager licenses, 2 Onboard Licenses
A customer would like to deploy ClearPass with these requirements:
every day, 100 employees need to authenticate with their corporate laptops using EAP-TLS every Friday, a meeting with business partners takes place and an additional 50 devices need to authenticate using Web Login Guest Authentication
What should the customer do regarding licenses? (Select two.)
A. When counting policy manager licenses, include the additional 50 business partner devices.
B. When counting policy manager licenses, exclude the additional 50 business partner devices.
C. Purchase Onboard licenses.
D. Purchase guest licenses.
E. Purchase Onguard licenses.
Refer to the exhibit.
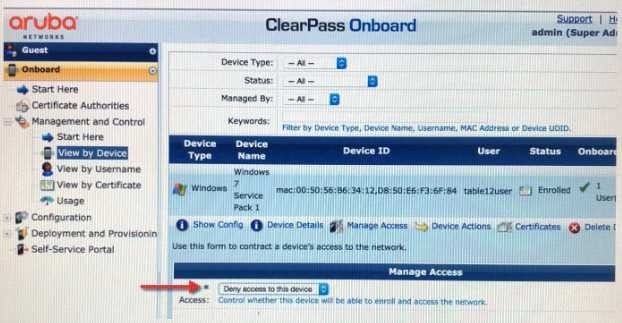
Based on the information shown, what will be the outcome when the administrator chooses "Deny Access to this Device? (Select two.)
A. EAP-TLS Authentication will be unaffected
B. The user can Onboard their device again
C. A new device certificate will be automatically pushed out to the device
D. The user cannot Onboard their device again
E. EAP-TLS Authentication will fail
Which types of files are stored in the Local Shared Folders database in ClearPass? (Select two.)
A. Software image
B. Backup files
C. Log files
D. Device fingerprint dictionaries
E. Posture dictionaries
Under which circumstances is it necessary to use an SNMP based Enforcement profile to send a VLAN?
A. when a VLAN must be assigned to a wired user on an Aruba Mobility Controller
B. when a VLAN must be assigned to a wireless user on an Aruba Mobility Controller
C. when a VLAN must be assigned to a wired user on a third party wired switch that does not support RADIUS return attributes
D. when a VLAN must be assigned to a wired user on an Aruba Mobility Access Switch
E. when a VLAN must be assigned to a wired user on a third party wired switch that does not support RADIUS accounting
What must be configured to enable RADIUS authentication with ClearPass on a network access device (NAD)? (Select two.)
A. the ClearPass server must have the network device added as a valid NAD
B. the ClearPass server certificate must be installed on the NAD
C. a matching shared secret must be configured on both the ClearPass server and NAD
D. an NTP server needs to be set up on the NAD
E. a bind username and bind password must be provided
Refer to the exhibit.
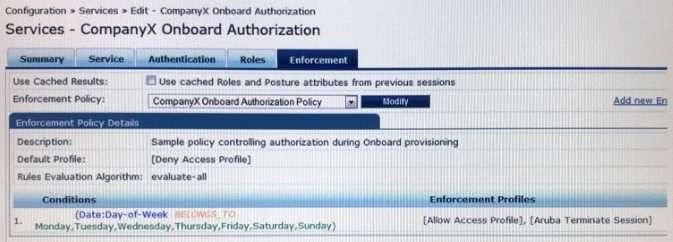
Based on the configuration of the Enforcement Profiles in the Onboard Authorization service shown, which Onboarding action will occur?
A. The device will be disconnected from the network after Onboarding so that an EAP-TLS authentication is not performed.
B. The device will be disconnected from and reconnected to the network after Onboarding is completed.
C. The device's onboard authorization request will be denied.
D. The device will be disconnected after post-Onboarding EAP-TLS authentication, so a second EAP- TLS authentication is performed.
E. After logging in on the Onboard web login page, the device will be disconnected form and reconnected to the network before Onboard begins.
An organization implements dual SSID Onboarding. The administrator used the Onboard service template to create services for dual SSID Onboarding. Which statement accurately describes the outcome?
A. The Onboard Provisioning service is triggered when the user connects to the provisioning SSID to Onboard their device.
B. The Onboard Authorization service is triggered when the user connects to the secure SSID.
C. The Onboard Authorization service is triggered during the Onboarding process.
D. The device connects to the secure SSID for provisioning.
E. The Onboard Authorization service is never triggered.
What is the purpose of ClearPass Onboard?
A. to provide MAC authentication for devices that don't support 802.1x
B. to run health checks on end user devices
C. to provision personal devices to securely connect to the network
D. to configure self-registration pages for guest users
E. to provide guest access for visitors to connect to the network
Which statement is true about the databases in ClearPass?
A. Entries in the guest user database do not expire.
B. A Static host list can only contain a list of IP addresses.
C. Entries in the guest user database can be deleted.
D. Entries in the local user database cannot be modified.
E. The endpoints database can only be populated by manually adding MAC addresses to the table.
Which is a valid policy simul-ation types in ClearPass? (Choose three.)
A. Enforcement Policy
B. Posture token derivation
C. Role Mapping
D. Endpoint Profiler
E. Chained simulation
Which statement is true? (Choose two.)
A. Mobile device Management is the result of Onboarding.
B. Third party Mobile Device Management solutions can be integrated with ClearPass.
C. Mobile Device Management is the authentication that happens before Onboarding.
D. Mobile Device Management is an application container that is used to provision work applications.
E. Mobile Device Management is used to control device functions post-Onboarding.