HPE2-W05 Online Practice Questions and Answers
You are troubleshooting ClearPass with IntroSpect, and you notice that in Access Tracker the IntroSpect Logon Logoff actions profile is executing. However, the ClearPass Log Source on the IntroSpect Analyzer is showing dropped entries.
Would this be a good troubleshooting step? (Confirm that the ClearPass context action is sending the User name, MAC Address, Entity Type, and User Role)
A. Yes
B. No
While troubleshooting integration between ClearPass and IntroSpect, you notice that there are no log events for either THROUGHPUT or ERROR in the ClearPass log source on the IntroSpect Analyzer. You are planning your troubleshooting actions.
Is this something you should check? (Check the authentication service being used in ClearPass for the Login - Logout enforcement policy.)
A. Yes
B. No
Refer to the exhibit.
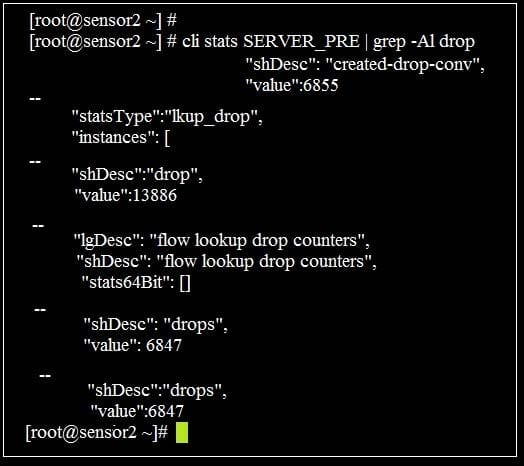
You are monitoring a new virtual packet processor with a network tap. You run the command "cli stats SERVER_PRE | gre-a1 drop" and then return an hour later and run the same command, but notice there is a significant increase in the number dropped packets.
Could this be a reason for the increase? (The Packet Processor may not be allocated the proper number of memory allocated on the VM server for the size of the TAP.)
A. Yes
B. No
A customer with approximately 200 users in Active Directory, is running Aruba Mobility Controllers, Palo Alto firewalls, and Pulse Secure VPN and InfoBlox DNS on their network. They would like to implement the 2RU Fixed Configuration Analyzer Standard Edition.
Would this be a good response to the customer? (The Standard Edition will work for this customer as long as they do not want to capture the InfoBlox DNS logs.)
A. Yes
B. No
Refer to the exhibit.
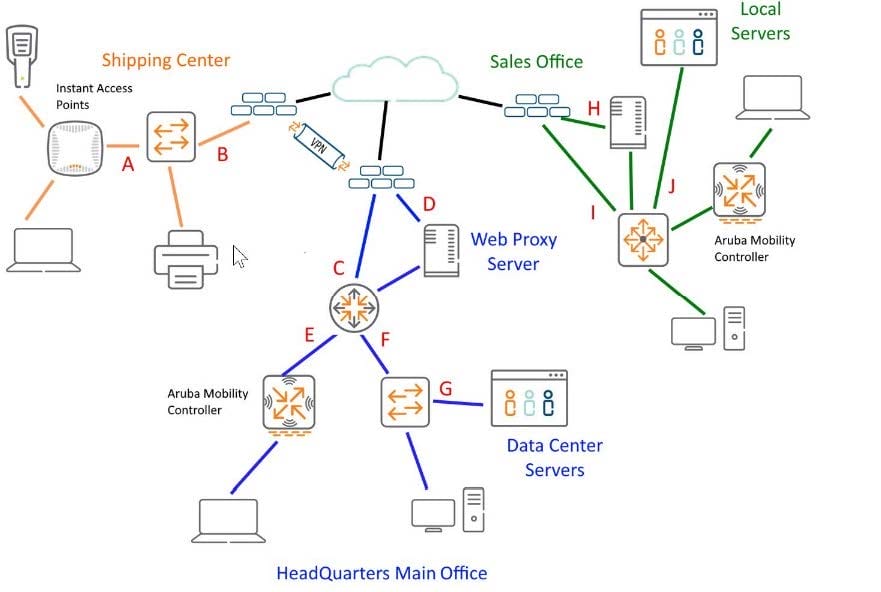
Given the network diagram, would this be a proper location for a network tap? (Port G at the Head Quarters Site would expose all East/West traffic bound for the data center.)
A. Yes
B. No
You deploy IntroSpect Analyzer in your existing network. You want to monitor email for suspect malware activity. Would this action be supported by IntroSpect? (Deploy a supported DNP like Proofpoint Email Protection, and integrate with The IntroSpect Analyzer.)
A. Yes
B. No
You have been asked to provide a Bill of Materials (BoM) for a mature small business with two sites. The IT Director prefers all hardware to be on-premise but is open to cloud-based solution. In conversations with the IT staff, you determine that the main site has approximately 550 network devices and 400 users. All users are in Active Directory. Eighty of the users use a Pulse Secure VPN to work remotely.
The second site is a warehouse operation with approximately 40 users and another 10 users that use Pulse Secure VPN. All wireless is using Aruba Networks Instant APs. There are Active Directory servers at both sites. All logs are currently being gathered into Splunk. The team feels that they can properly monitor the corporate site network with a single tap port on a central switch at the main office. There will be a network tap at the remote site.
Is this a suggestion you would make to the customer? (The customer should purchase the Scale-Out option for their data center, with a Packet Processor at the remote site.)
A. Yes
B. No
You are deploying a new IntroSpect Packet Processor in your data center. It is not communicating with the analyzer in the same data center. You think that you have entered the host name of the analyzer incorrectly while bootstrapping the packet processor. Would this be a logical next step? (Clear out the bootstrap data and restart the system. After the restart, rerun the bootstrap.)
A. Yes
B. No
You are working on an IntroSpect Analyzer to fix an issue, and a restart is required after fixing the issue. Is this the correct procedure to restart? (From the Analyzer Menu navigate to Configuration ->System>Cluster Start/Stop->Restart Cluster.)
A. Yes
B. No
Arube IntroSpect establishes different types of baselines to perform user or device behavior analysis. Is this a correct description of a baseline that IntroSpect establishes? (Individual history baseline: this typically takes 10 to 14 days to establish a "steady state" that can be used.)
A. Yes
B. No
Refer to the exhibit.

You are monitoring network traffic and considering DNS flow patterns. Where is a good location to place the Network Tap or Taps? (Location D will capture all DNS requests.)
A. Yes
B. No
Your company has found some suspicious conversations for some internal users. The security team suspects those users are communicating with entities in other countries. You have been assigned the task of identifying those users who are either uploading or downloading files from servers in other countries. Is this the best way to visualize conversations of suspected users in this scenario? (Visualizing Applications and Ports.)
A. Yes
B. No
In a conversation with a colleague you are asked to give them an idea of what type of monitor source you would use for each attack stage.

Would this be a correct correlation? (For "Command and Control" you can monitor DNS through AMON on the Aruba Mobility Controllers.)
A. Yes
B. No
You want to create a use case to get alerts when the behavior of an internal user has deviated from the norm of other users that work in the same department. Is this a suitable baseline for this use case? (Peer baseline based on the LDAP department from Active Directory.)
A. Yes
B. No
The company has a DMZ with an application server where customers can upload and access their product orders. The security admin wants to know how you configure IntroSpect to monitor this server. Should this be part of your plan? (Configure the server in the DMZ as a High Value Asset in Menu>Configuration>Analytics>Correlator Config>so that IntroSpect will monitor the server for access patterns.)
A. Yes
B. No
