GNSA Online Practice Questions and Answers
You work as a Network Administrator for XYZ CORP. The company has a TCP/IP-based network environment. The network contains Cisco switches and a Cisco router.
You run the following command for a router interface:
show interface serial0
You get the following output:
Serial0 is administratively down, line protocol is down
What will be your conclusion after viewing this output?
A. There is a physical problem either with the interface or the cable attached to it.
B. The router has no power.
C. There is a problem related to encapsulation.
D. The interface is shut down.
John works as a professional Ethical Hacker. He is assigned a project to test the security of www.we-are-secure.com. He is working on the Linux operating system. He wants to sniff the we-are-secure network and intercept a conversation between two employees of the company through session hijacking.
Which of the following tools will John use to accomplish the task?
A. IPChains
B. Tripwire
C. Hunt
D. Ethercap
You are the security manager of Microliss Inc. Your enterprise uses a wireless network infrastructure with access points ranging 150-350 feet. The employees using the network complain that their passwords and important official information
have been traced.
You discover the following clues:
The information has proved beneficial to another company.
The other company is located about 340 feet away from your office.
The other company is also using wireless network.
The bandwidth of your network has degraded to a great extent.
Which of the following methods of attack has been used?
A. A piggybacking attack has been performed.
B. A DOS attack has been performed.
C. The information is traced using Bluebugging.
D. A worm has exported the information.
You work as a Network Administrator for Blue Well Inc. The company has a TCP/IP-based routed network. Two segments have been configured on the network as shown below:
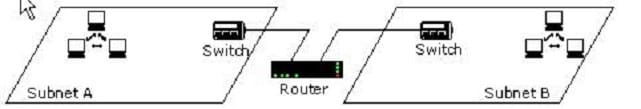
One day, the switch in Subnet B fails. What will happen?
A. Communication between the two subnets will be affected.
B. The whole network will collapse.
C. Workstations on Subnet A will become offline
D. Workstations on Subnet B will become offline.
Sam works as a Network Administrator for Blue Well Inc. All client computers in the company run the Windows Vista operating. Sam creates a new user account. He wants to create a temporary password for the new user such that the user is forced to change his password when he logs on for the first time.
Which of the following options will he choose to accomplish the task?
A. User cannot change password
B. Delete temporary password at next logon
C. User must change password at next logon
D. Password never expires
Which of the following statements is true about residual risks?
A. It is the probabilistic risk after implementing all security measures.
B. It can be considered as an indicator of threats coupled with vulnerability.
C. It is a weakness or lack of safeguard that can be exploited by a threat.
D. It is the probabilistic risk before implementing all security measures.
Wired Equivalent Privacy (WEP) is a security protocol for wireless local area networks (WLANs). It has two components, authentication and encryption. It provides security equivalent to wired networks for wireless networks. WEP encrypts data on a wireless network by using a fixed secret key.
Which of the following statements are true about WEP?
A. WEP uses the RC4 encryption algorithm.
B. The Initialization Vector (IV) field of WEP is only 24 bits long.
C. It provides better security than the Wi-Fi Protected Access protocol.
D. Automated tools such as AirSnort are available for discovering WEP keys.
You work as a Network Administrator for XYZ CORP. The company has a small TCP/IP-based network environment. The network contains a Cisco Catalyst 6000 family switch. A few sales people come to your outer office and use your local network to access the Internet, as well as to demonstrate their products. What will you do to prevent your network from being accessed by any outside computers?
A. Configure port security.
B. Configure a firewall for IP blocking on the network.
C. Configure a firewall for MAC address blocking on the network.
D. Configure a port scanner.
Which of the following is a basic feature of the Unix operating system? (Choose three)
A. It is highly portable across hardware.
B. All files can be individually protected using read, write, and execute permissions for the user, group, and others.
C. It allows all the modules to be loaded into memory.
D. A user can execute multiple programs at the same time from a single terminal.
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He finds that the We-are-secure server is vulnerable to attacks. As a countermeasure, he suggests that the Network Administrator should remove the IPP printing capability from the server.
He is suggesting this as a countermeasure against __________.
A. NetBIOS NULL session
B. DNS zone transfer
C. IIS buffer overflow
D. SNMP enumeration
You work as a Database Administrator for BigApple Inc. The Company uses Oracle as its database. You enabled standard database auditing. Later, you noticed that it has a huge impact on performance of the database by generating a large amount of audit data.
How will you keep control on this audit data?
A. By implementing principle of least privilege.
B. By removing some potentially dangerous privileges.
C. By setting the REMOTE_LOGIN_PASSWORDFILE instance parameter to NONE.
D. By limiting the number of audit records generated to only those of interest.
The Security Auditor's Research Assistant (SARA) is a third generation network security analysis tool. Which of the following statements are true about SARA? (Choose two)
A. It operates under Unix, Linux, MAC OS/X, or Windows (through coLinux) OS.
B. It cannot be used to perform exhaustive XSS tests.
C. It cannot be used to perform SQL injection tests.
D. It supports plug-in facility for third party apps.
Which of the following tools is used for port scanning?
A. L0phtcrack
B. NSLOOKUP
C. NETSH
D. Nmap
You have been assigned a project to develop a Web site for a construction company. You plan to develop a Web site and want to use cascading style sheets (CSS) as it helps you to get more control over the appearance and presentation of your Web pages and also extends your ability to precisely specify the position and appearance of the elements on a page and create special effects. You want to define styles for individual elements of a page.
Which type of style sheet will you use?
A. Embedded Style Sheet
B. Internal Style Sheet
C. External Style Sheet
D. Inline Style Sheet
Which of the following is used to execute a SQL statement from the SQL buffer?
A. Entering an asterisk (*)
B. Pressing [RETURN] once
C. Pressing [RETURN] twice
D. Entering a slash (/)
E. Pressing [ESC] twice.