GCCC Online Practice Questions and Answers
During a security audit which test should result in a source packet failing to reach its intended destination?
A. A new connection request from the Internet is sent to a host on the company 's internal net work
B. A packet originating from the company's DMZ is sent to a host on the company's internal network
C. A new connection request from the internet is sent to the company's DNS server
D. A packet originating from the company's internal network is sent to the company's DNS server
An organization is implementing a control for the Limitation and Control of Network Ports, Protocols, and Services CIS Control. Which action should they take when they discover that an application running on a web server is no longer needed?
A. Uninstall the application providing the service
B. Turn the service off in the host configuration files
C. Block the protocol for the unneeded service at the firewall
D. Create an access list on the router to filter traffic to the host
Given the audit finding below, which CIS Control was being measured?
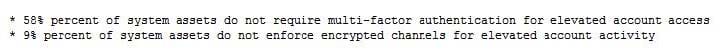
A. Controlled Access Based on the Need to Know
B. Controlled Use of Administrative Privilege
C. Limitation and Control of Network Ports, Protocols and Services
D. Secure Configurations for Hardware and Software on Laptops, Workstations, and Servers
E. Inventory and Control of Hardware Assets
What is the list displaying?

A. Allowed program in a software inventory application
B. Unauthorized programs detected in a software inventory
C. Missing patches from a patching server
D. Installed software on an end-user device
Janice is auditing the perimeter of the network at Sugar Water InC. According to documentation, external SMTP traffic is only allowed to and from 10.10.10.25. Which of the following actions would demonstrate the rules are configured incorrectly?
A. Receive spam from a known bad domain
B. Receive mail at Sugar Water Inc. account using Outlook as a mail client
C. Successfully deliver mail from another host inside the network directly to an external contact
D. Successfully deliver mail from web client using another host inside the network to an external contact.
Dragonfly Industries requires firewall rules to go through a change management system before they are configured. Review the change management log. Which of the following lines in your firewall ruleset has expired and should be removed from the configuration?
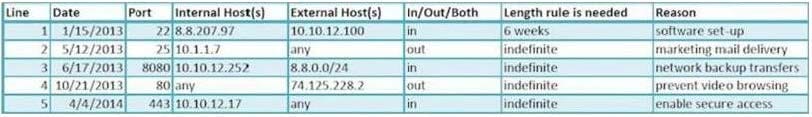
A. access-list outbound permit tcp host 10.1.1.7 any eq smtp
B. access-list outbound deny tcp any host 74.125.228.2 eq www
C. access-list inbound permit tcp 8.8.0.0 0.0.0.255 10.10.12.252 eq 8080
D. access-list inbound permit tcp host 8.8.207.97 host 10.10.12.100 eq ssh
An organization has implemented a policy to detect and remove malicious software from its network. Which of the following actions is focused on correcting rather than preventing attack?
A. Configuring a firewall to only allow communication to whitelisted hosts and ports
B. Using Network access control to disable communication by hosts with viruses
C. Disabling autorun features on all workstations on the network
D. Training users to recognize potential phishing attempts
A global corporation has major data centers in Seattle, New York, London and Tokyo. Which of the following is the correct approach from an intrusion detection and event correlation perspective?
A. Configure all data center systems to use local time
B. Configure all data center systems to use GMT time
C. Configure all systems to use their default time settings
D. Synchronize between Seattle and New York, and use local time for London and Tokyo
