ECSAv8 Online Practice Questions and Answers
HTTP protocol specifies that arbitrary binary characters can be passed within the URL by using %xx notation, where 'xx' is the
A. ASCII value of the character
B. Binary value of the character
C. Decimal value of the character
D. Hex value of the character
Identify the injection attack represented in the diagram below:
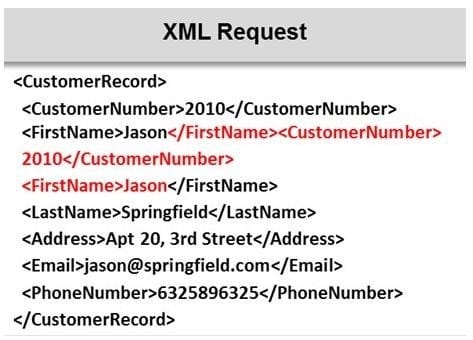
A. XPath Injection Attack
B. XML Request Attack
C. XML Injection Attack
D. Frame Injection Attack
In a TCP packet filtering firewall, traffic is filtered based on specified session rules, such as when a session is initiated by a recognized computer.
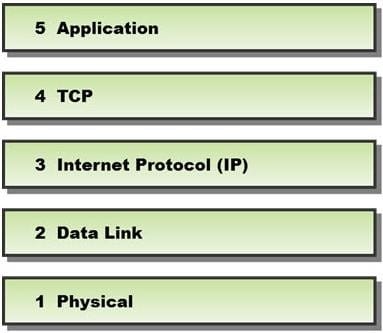
Identify the level up to which the unknown traffic is allowed into the network stack.
A. Level 5 ?Application
B. Level 2 ?Data Link
C. Level 4 ?TCP
D. Level 3 ?Internet Protocol (IP)
Which of the following policies states that the relevant application owner must authorize requests for additional access to specific business applications in writing to the IT Department/resource?
A. Special-Access Policy
B. User Identification and Password Policy
C. Personal Computer Acceptable Use Policy
D. User-Account Policy
A penetration test consists of three phases: pre-attack phase, attack phase, and post- attack phase.
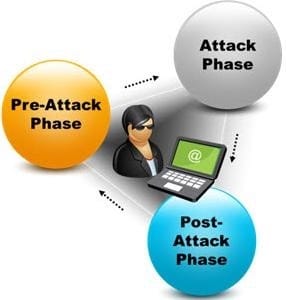
Active reconnaissance which includes activities such as network mapping, web profiling, and perimeter mapping is a part which phase(s)?
A. Post-attack phase
B. Pre-attack phase and attack phase
C. Attack phase
D. Pre-attack phase
Which type of vulnerability assessment tool provides security to the IT system by testing for vulnerabilities in the applications and operation system?
A. Active/Passive Tools
B. Application-layer Vulnerability Assessment Tools
C. Location/Data Examined Tools
D. Scope Assessment Tools
Which of the following attributes has a LM and NTLMv1 value as 64bit + 64bit + 64bit and NTLMv2 value as 128 bits?
A. Hash Key Length
B. C/R Value Length
C. C/R Key Length
D. Hash Value Length
Which of the following equipment could a pen tester use to perform shoulder surfing?
A. Binoculars
B. Painted ultraviolet material
C. Microphone
D. All the above
Which of the following acts is a proprietary information security standard for organizations that handle cardholder information for the major debit, credit, prepaid, e-purse, ATM, and POS cards and applies to all entities involved in payment card processing?
A. PIPEDA
B. PCI DSS
C. Human Rights Act 1998
D. Data Protection Act 1998
By default, the TFTP server listens on UDP port 69. Which of the following utility reports the port status of target TCP and UDP ports on a local or a remote computer and is used to troubleshoot TCP/IP connectivity issues?
A. PortQry
B. Netstat
C. Telnet
D. Tracert
In the example of a /etc/passwd file below, what does the bold letter string indicate?
nomad:HrLNrZ3VS3TF2:501:100: Simple Nomad:/home/nomad:/bin/bash
A. Maximum number of days the password is valid
B. Group number
C. GECOS information
D. User number
In the TCP/IP model, the transport layer is responsible for reliability and flow control from source to the destination. TCP provides the mechanism for flow control by allowing the sending and receiving hosts to communicate. A flow control mechanism avoids the problem with a transmitting host overflowing the buffers in the receiving host.
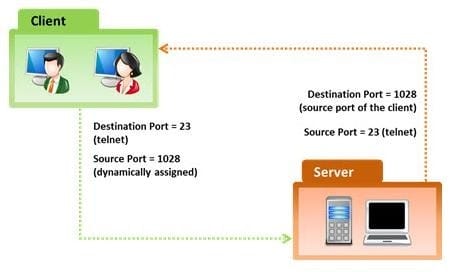
Which of the following flow control mechanism guarantees reliable delivery of data?
A. Sliding Windows
B. Windowing
C. Positive Acknowledgment with Retransmission (PAR)
D. Synchronization
The first phase of the penetration testing plan is to develop the scope of the project in consultation with the client. Pen testing test components depend on the client's operating environment, threat perception, security and compliance requirements, ROE, and budget. Various components need to be considered for testing while developing the scope of the project.
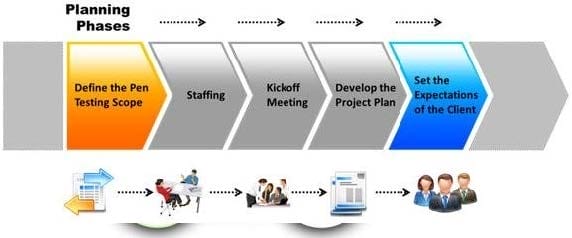
Which of the following is NOT a pen testing component to be tested?
A. System Software Security
B. Intrusion Detection
C. Outside Accomplices
D. Inside Accomplices
A directory traversal (or path traversal) consists in exploiting insufficient security validation/sanitization of user-supplied input file names, so that characters representing "traverse to parent directory" are passed through to the file APIs.
The goal of this attack is to order an application to access a computer file that is not intended to be accessible. This attack exploits a lack of security (the software is acting exactly as it is supposed to) as opposed to exploiting a bug in the code.
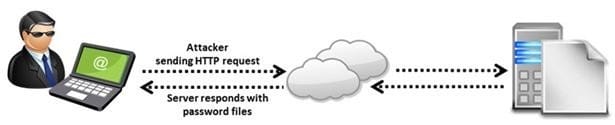
To perform a directory traversal attack, which sequence does a pen tester need to follow to manipulate variables of reference files?
A. dot-dot-slash (../) sequence
B. Denial-of-Service sequence
C. Brute force sequence
D. SQL Injection sequence
Assessing a network from a hacker's point of view to discover the exploits and vulnerabilities that are accessible to the outside world is which sort of vulnerability assessment?
A. Network Assessments
B. Application Assessments
C. Wireless Network Assessments
D. External Assessment
