ECSAV10 Online Practice Questions and Answers
Sandra, a wireless network auditor, discovered her client is using WEP. To prove the point that the WEP
encryption is very weak, she wants to decrypt some WEP packets. She successfully captured the WEP
data packets, but could not reach the content as the data is encrypted.
Which of the following will help Sandra decrypt the data packets without knowing the key?
A. Fragmentation Attack
B. Chopchop Attack
C. ARP Poisoning Attack
D. Packet injection Attack
Identify the PRGA from the following screenshot: A. replay_src-0124-161120.cap
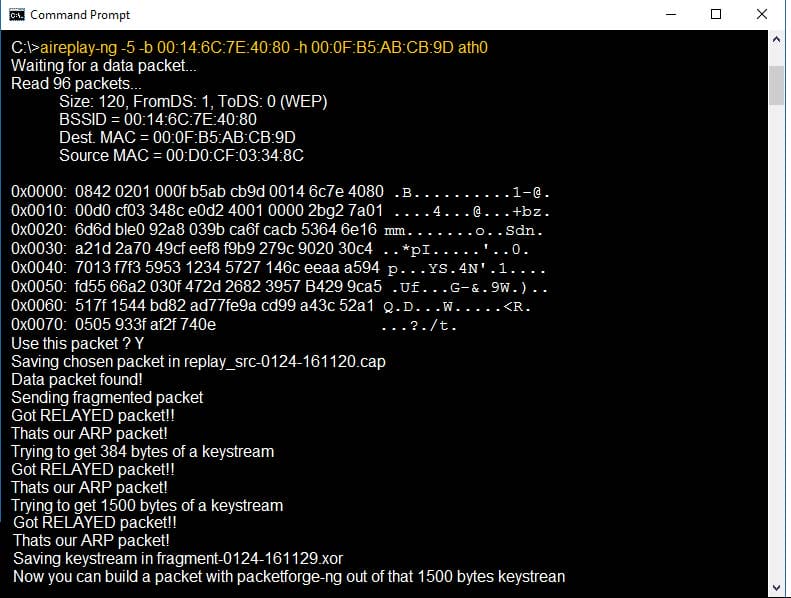
B. fragment-0124-161129.xor
C. 0505 933f af2f 740e
D. 0842 0201 000f b5ab cd9d 0014 6c7e 4080
Robert is a network admin in XYZ Inc. He deployed a Linux server in his enterprise network and wanted to share some critical and sensitive files that are present in the Linux server with his subordinates. He wants to set the file access permissions using chmod command in such a way that his subordinates can only read/view the files but cannot edit or delete the files. Which of the following chmod commands can Robert use in order to achieve his objective?
A. chmod 666
B. chmod 644
C. chmod 755
D. chmod 777
Edward is a penetration tester hired by the OBC Group. He was asked to gather information on the client's
network. As part of the work assigned, Edward needs to find the range of IP addresses and the subnet
mask used by the target organization.
What does Edward need to do to get the required information?
A. Search for web pages posting patterns and revision numbers
B. Search for an appropriate Regional Internet Registry (RIR)
C. Search for link popularity of the company's website
D. Search for Trade Association Directories
What is the objective of the following bash script?

A. It gives a list of IP addresses that have an FTP port open
B. It tries to connect to FTP port on a target machine C. It checks if a target host has the FTP port open and quits
D. It checks if an FTP port on a target machine is vulnerable to arracks
George, an ex-employee of Netabb Ltd. with bruised feelings due to his layoff, tries to take revenge against the company. He randomly tried several attacks against the organization. As some of the employees used weak passwords to their user accounts, George was successful in cracking the user accounts of several employees with the help of a common passwords file. What type of password cracking attack did George perform?
A. Hybrid attack
B. Dictionary attack
C. Brute forcing attack
D. Birthday attack
Which of the following information security acts enables to ease the transfer of financial information between institutions and banks while making the rights of the individual through security requirements more specific?
A. The Digital Millennium Copyright Act (DMCA)
B. Sarbanes Oxley Act (SOX)
C. Computer Misuse Act 1990
D. Gramm-Leach-Bliley Act (GLBA)
Adam is working as a senior penetration tester at Eon Tech Services Ltd. The company asked him to
perform penetration testing on their database. The company informs Adam they use Microsoft SQL Server.
As a part of the penetration testing, Adam wants to know the complete information about the company's
database. He uses the Nmap tool to get the information.
Which of the following Nmap commands will Adam use to get the information?
A. nmap -p2051 --script ms-sql-info
B. nmap -p1801 --script ms-sql-info
C. nmap -p1443 --script ms-sql-info
D. nmap -p1521 --script ms-sql-info
Analyze the ICMP packet below and mark the correct statement.
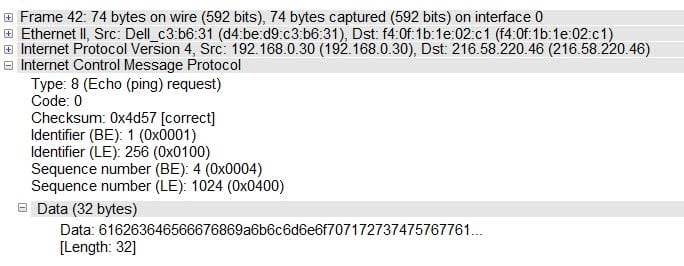
A. It is a ping packet that requires fragmentation, but the Don't Fragment flag is set
B. It is a ping request, but the destination port is unreachable
C. It is a ping response, when the destination host is unknown
D. It is a ping request, but the destination network is unreachable
Harry, a penetration tester in SqSac Solutions Ltd., is trying to check if his company's SQL server database is vulnerable. He also wants to check if there are any loopholes present that can enable the perpetrators to exploit and gain access to the user account login details from the database. After performing various test attempts, finally Harry executes an SQL query that enabled him to extract all the available Windows Login Account details. Which of the following SQL queries did Harry execute to obtain the information?
A. SELECT name FROM sys.server_principals WHERE TYPE = 'R'
B. SELECT name FROM sys.server_principals WHERE TYPE = 'U'
C. SELECT name FROM sys.server_principals WHERE TYPE = 'G'
D. SELECT name FROM sys.server_principals WHERE TYPE = 'S'
Which type of penetration testing will require you to send the Internal Control Questionnaires (ICQ) to the client?
A. White-box testing
B. Black-box testing
C. Blind testing
D. Unannounced testing
Which of the following policies states that the relevant application owner must authorize requests for additional access to specific business applications in writing to the IT Department/resource?
A. Special-Access Policy
B. User Identification and Password Policy
C. Personal Computer Acceptable Use Policy
D. User-Account Policy
You are running known exploits against your network to test for possible vulnerabilities. To test the strength of your virus software, you load a test network to mimic your production network. Your software successfully blocks some simple macro and encrypted viruses. You decide to really test the software by using virus code where the code rewrites itself entirely and the signatures change from child to child, but the functionality stays the same. What type of virus is this that you are testing?
A. Metamorphic
B. Oligomorhic
C. Polymorphic
D. Transmorphic
In which of the following IDS evasion techniques does IDS reject the packets that an end system accepts?
A. IPS evasion technique
B. IDS evasion technique
C. UDP evasion technique
D. TTL evasion technique
Rule of Engagement (ROE) is the formal permission to conduct a pen-test. It provides top-level guidance for conducting the penetration testing. Various factors are considered while preparing the scope of ROE which clearly explain the limits associated with the security test.

Which of the following factors is NOT considered while preparing the scope of the Rules of Engagment (ROE)?
A. A list of employees in the client organization
B. A list of acceptable testing techniques
C. Specific IP addresses/ranges to be tested
D. Points of contact for the penetration testing team
