CKS Online Practice Questions and Answers
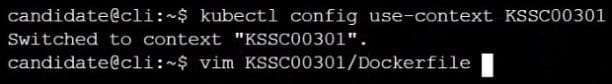
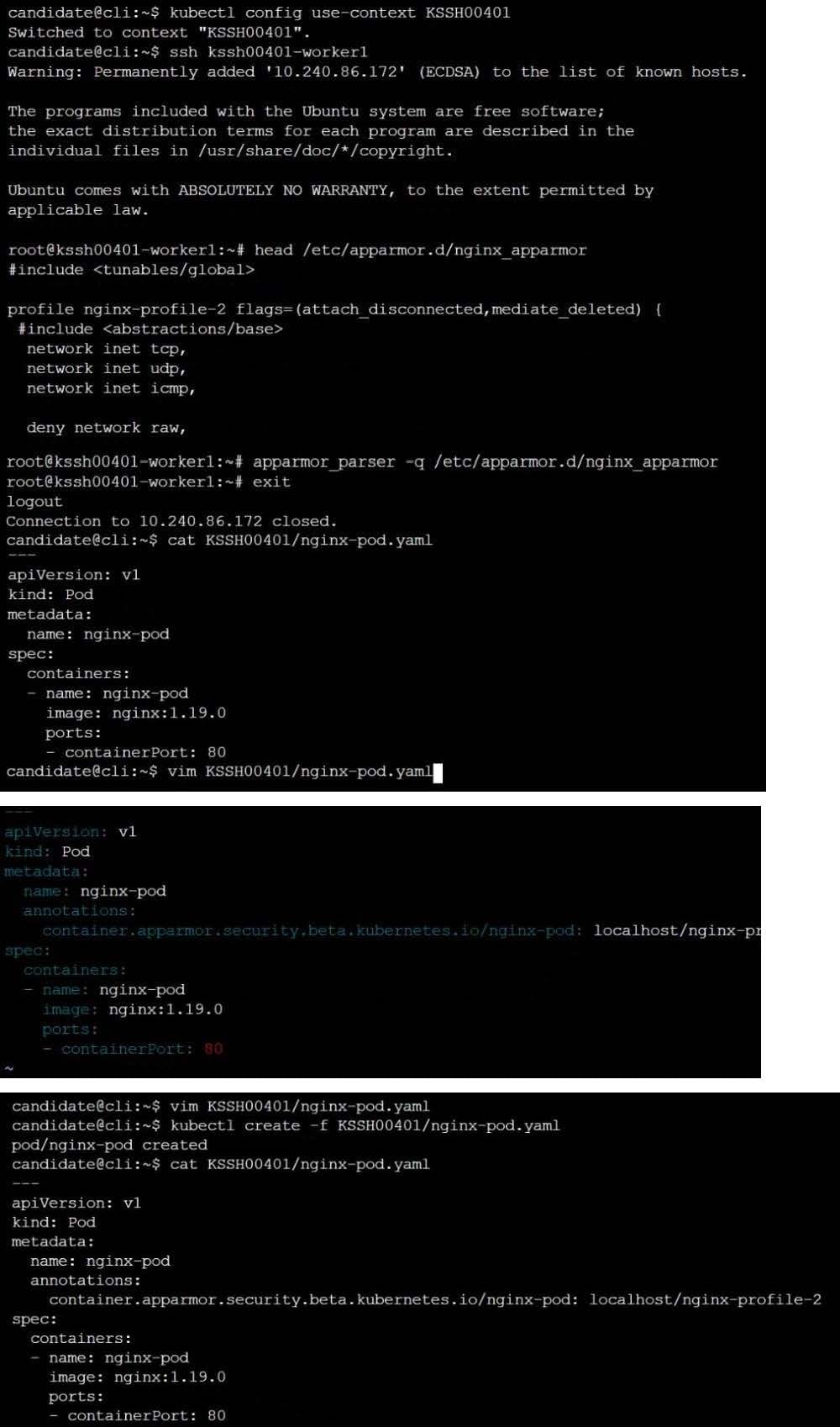
On the Cluster worker node, enforce the prepared AppArmor profile
1.
#include
2.
profile nginx-deny flags=(attach_disconnected) {
3.
#include
4.
file,
5.
# Deny all file writes.
6.
deny /** w,
7.
}
8.
EOF'
Edit the prepared manifest file to include the AppArmor profile.
1.
apiVersion: v1
2.
kind: Pod
3.
metadata:
4.
name: apparmor-pod
5.
spec:
6.
containers:
7.
- name: apparmor-pod
8.
image: nginx
Finally, apply the manifests files and create the Pod specified on it.
Verify: Try to make a file inside the directory which is restricted.
A. See explanation below.
B. PlaceHolder
Fix all issues via configuration and restart the affected components to ensure the new setting takes effect. Fix all of the following violations that were found against the API server:
1.
Ensure that the RotateKubeletServerCertificate argument is set to true.
2.
Ensure that the admission control plugin PodSecurityPolicy is set.
3.
Ensure that the --kubelet-certificate-authority argument is set as appropriate. Fix all of the following violations that were found against the Kubelet:
1.
Ensure the --anonymous-auth argument is set to false.
2.
Ensure that the --authorization-mode argument is set to Webhook. Fix all of the following violations that were found against the ETCD:
1.
Ensure that the --auto-tls argument is not set to true
2.
Ensure that the --peer-auto-tls argument is not set to true
Hint: Take the use of Tool Kube-Bench
A. See the below.
B. PlaceHolder
Create a PSP that will only allow the persistentvolumeclaim as the volume type in the namespace restricted.
Create a new PodSecurityPolicy named prevent-volume-policy which prevents the pods which is having different volumes mount apart from persistentvolumeclaim.
Create a new ServiceAccount named psp-sa in the namespace restricted.
Create a new ClusterRole named psp-role, which uses the newly created Pod Security Policy prevent-volume-policy
Create a new ClusterRoleBinding named psp-role-binding, which binds the created ClusterRole psp-role to the created SA psp-sa.
Hint:
Also, Check the Configuration is working or not by trying to Mount a Secret in the pod maifest, it should get failed.
POD Manifest:
1.
apiVersion: v1
2.
kind: Pod
3.
metadata:
4.
name:
5.
spec:
6.
containers:
7.
- name:
8.
image:
9.
volumeMounts: 10.- name: 11.mountPath: 12.volumes: 13.- name: 14.secret: 15.secretName:
A. See the below:
B. PlaceHolder
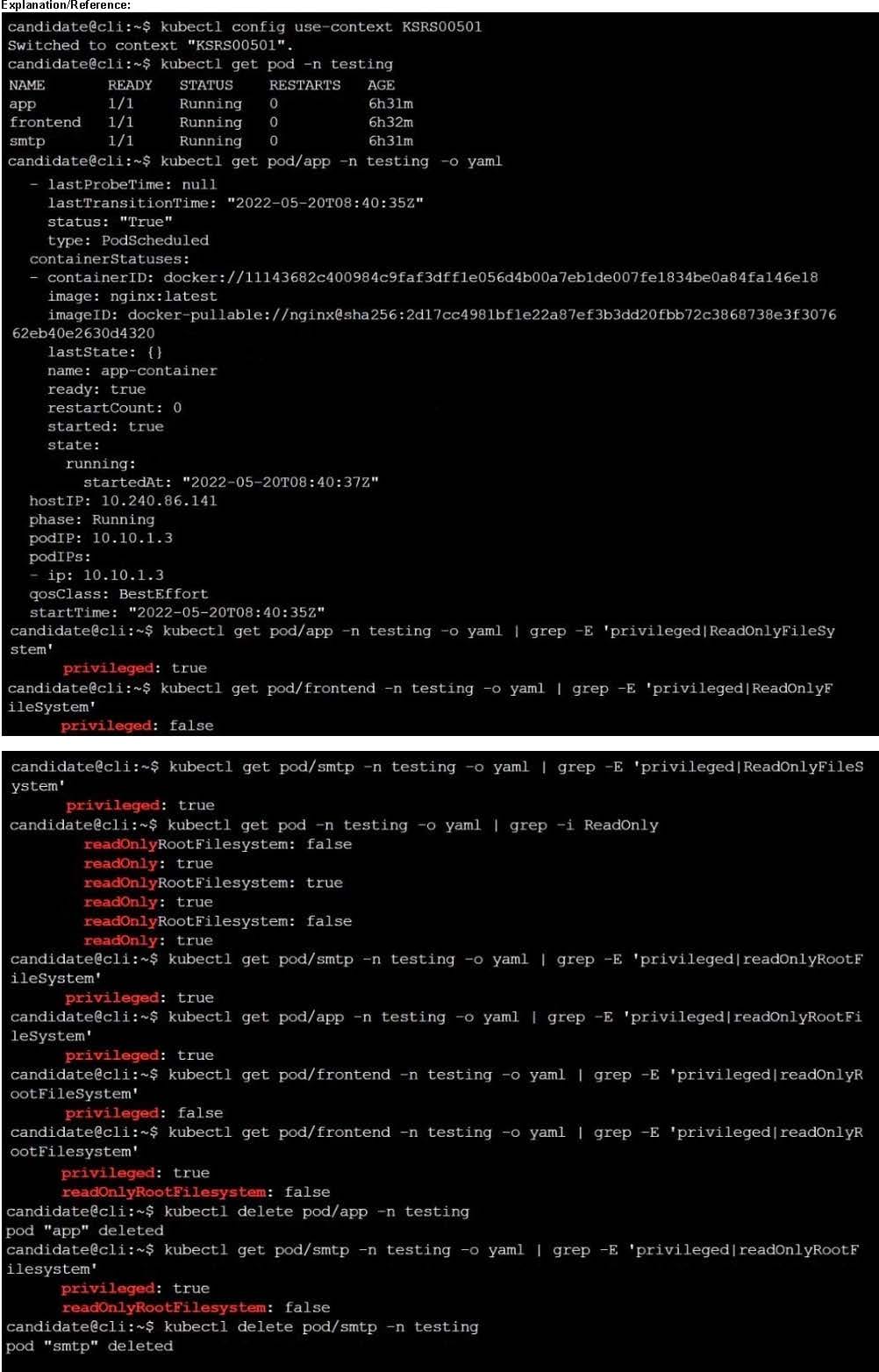
You must complete this task on the following cluster/nodes: Cluster: immutable-cluster
Master node: master1
Worker node: worker1
You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context immutable-cluster
Context: It is best practice to design containers to be stateless and immutable.
Task:
Inspect Pods running in namespace prod and delete any Pod that is either not stateless or not immutable.
Use the following strict interpretation of stateless and immutable:
1.
Pods being able to store data inside containers must be treated as not stateless.
Note: You don't have to worry whether data is actually stored inside containers or not already.
2.
Pods being configured to be privileged in any way must be treated as potentially not stateless or not immutable.
A. See the explanation below
B. PlaceHolder
Context:
Cluster: prod
Master node: master1
Worker node: worker1
You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context prod
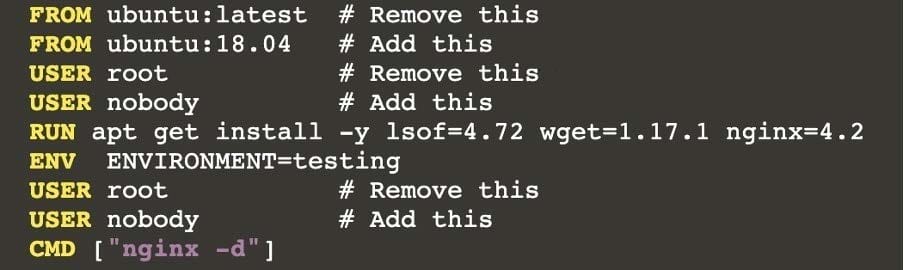
Task:
Analyse and edit the given Dockerfile (based on the ubuntu:18:04 image)
/home/cert_masters/Dockerfile fixing two instructions present in the file being prominent security/best-practice issues.
Analyse and edit the given manifest file
/home/cert_masters/mydeployment.yaml fixing two fields present in the file being prominent security/best-practice issues.
Note: Don't add or remove configuration settings; only modify the existing configuration settings, so that two configuration settings each are no longer security/best-practice concerns.
Should you need an unprivileged user for any of the tasks, use user nobody with user id 65535
A. See the explanation below
B. PlaceHolder
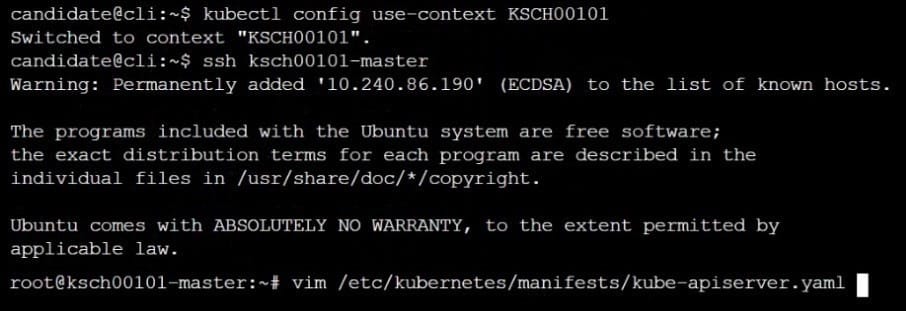
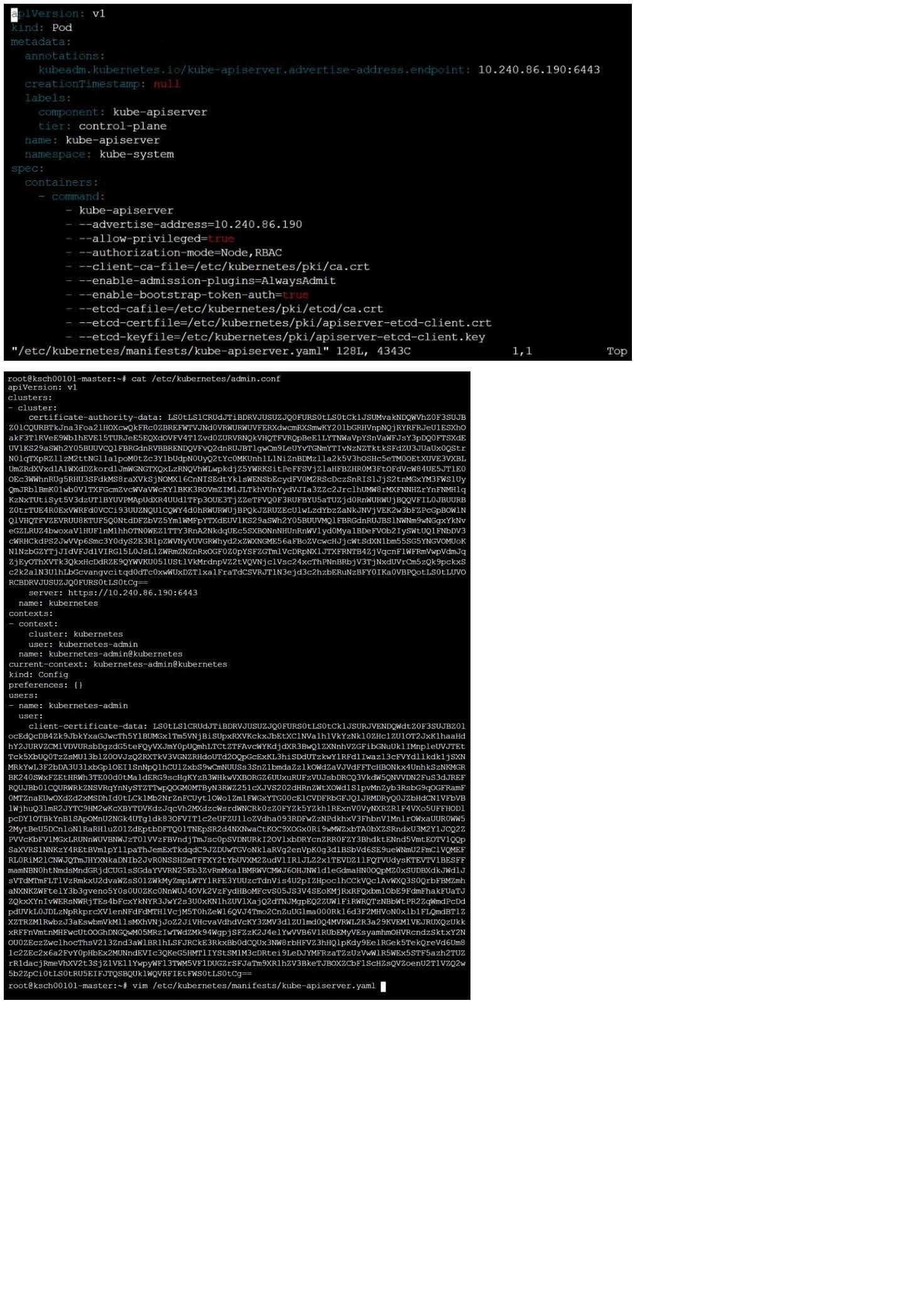
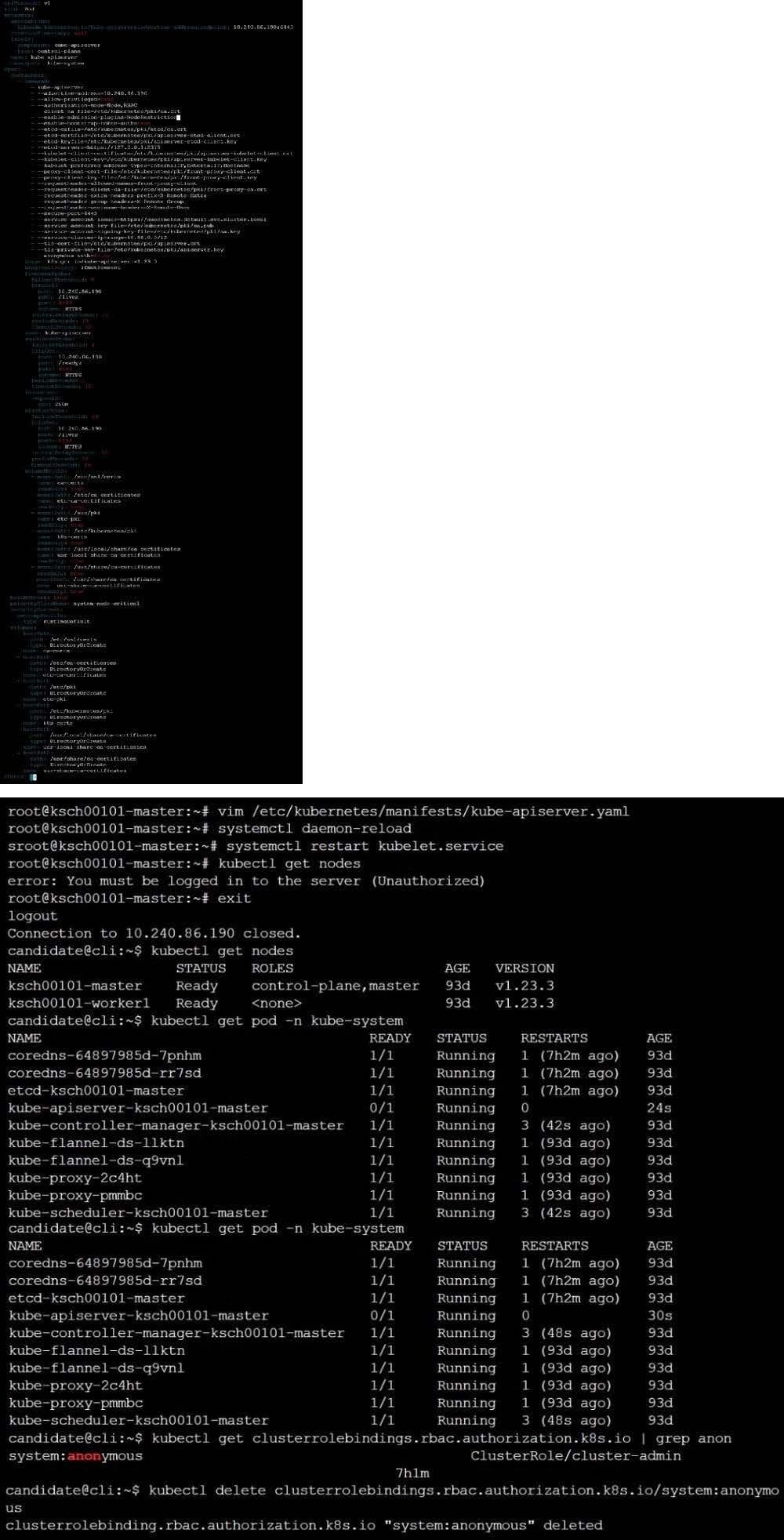
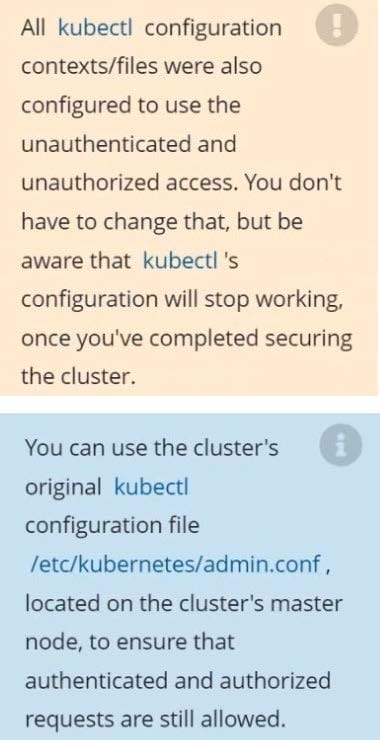
The kubeadm-created cluster's Kubernetes API server was, for testing purposes, temporarily configured to allow unauthenticated and unauthorized access granting the anonymous user duster-admin access.
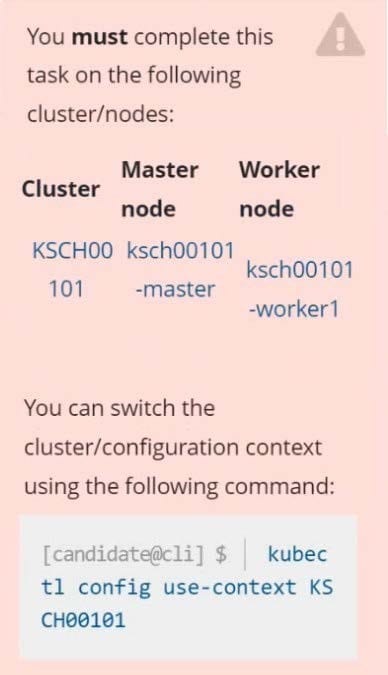
Task
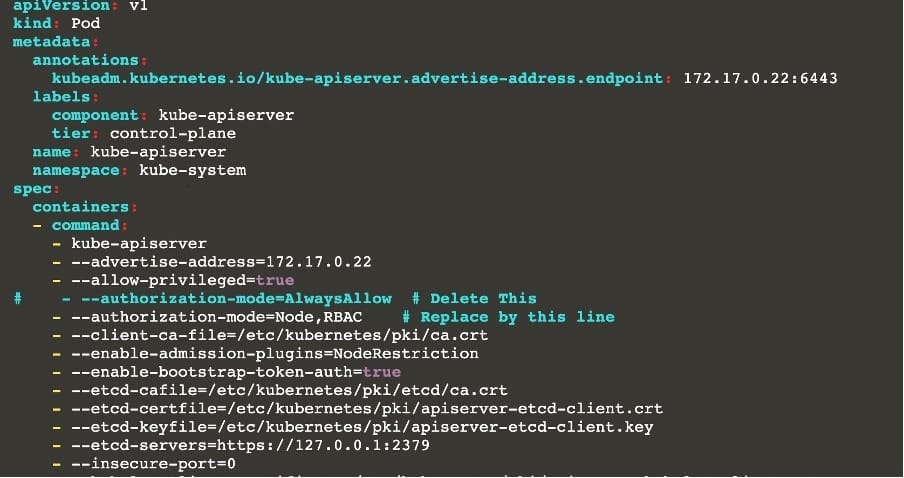
Reconfigure the cluster's Kubernetes API server to ensure that only authenticated and authorized REST requests are allowed.
Use authorization mode Node,RBAC and admission controller NodeRestriction.
Cleaning up, remove the ClusterRoleBinding for user system:anonymous.
A. See explanation below.
B. PlaceHolder
Cluster: qa-cluster
Master node: master Worker node: worker1 You can switch the cluster/configuration context using the following command: [desk@cli] $ kubectl config use-context qa-cluster
Task:
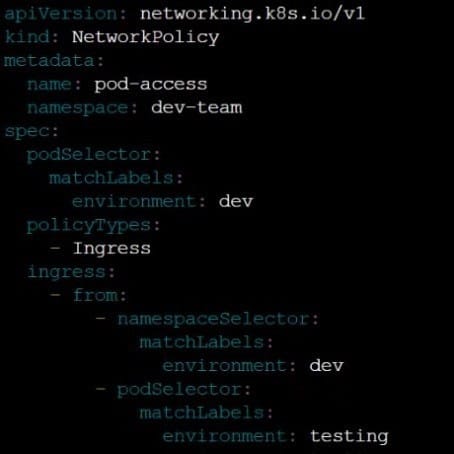
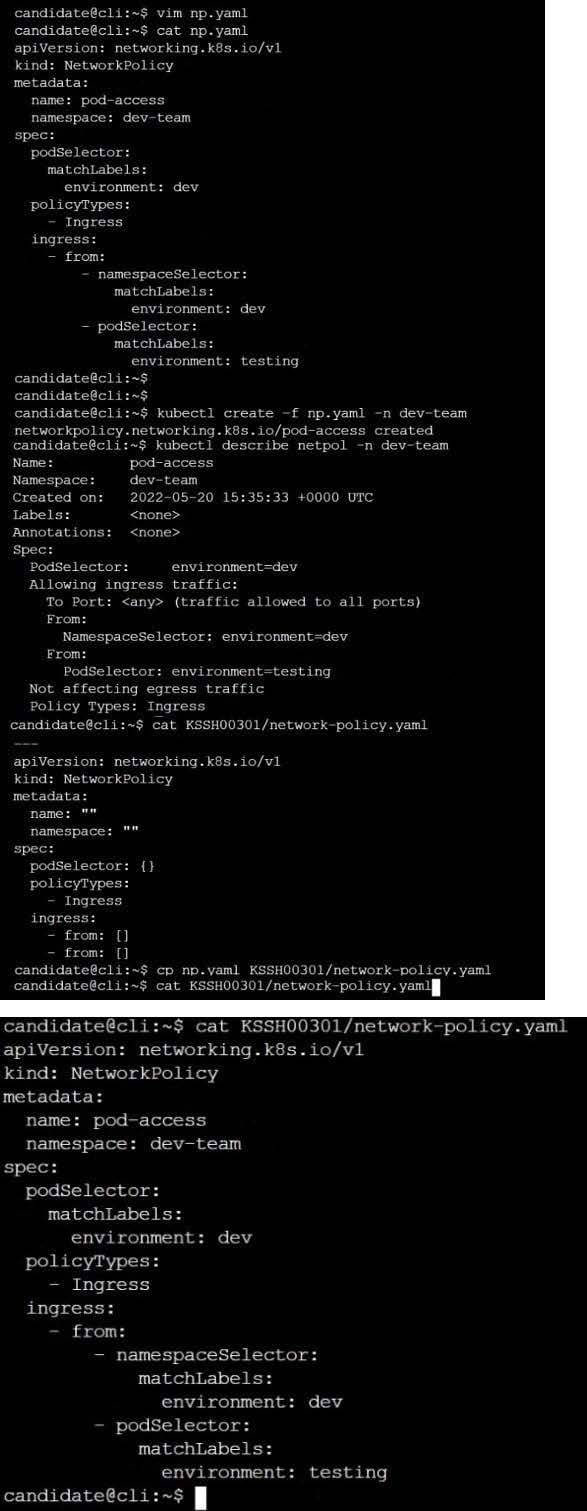
Create a NetworkPolicy named restricted-policy to restrict access to Pod product running in namespace dev.
Only allow the following Pods to connect to Pod products-service:
1.
Pods in the namespace qa
2.
Pods with label environment: stage, in any namespace
A. See the below.
B. PlaceHolder
1.
Retrieve the content of the existing secret named default-token-xxxxx in the testing namespace.
Store the value of the token in the token.txt
2.
Create a new secret named test-db-secret in the DB namespace with the following content:
username: mysql password: password@123
Create the Pod name test-db-pod of image nginx in the namespace db that can access test-db-secret via a volume at path /etc/mysql-credentials
A. See the explanation below:
B. PlaceHolder
Create a PSP that will prevent the creation of privileged pods in the namespace.
Create a new PodSecurityPolicy named prevent-privileged-policy which prevents the creation of privileged pods.
Create a new ServiceAccount named psp-sa in the namespace default.
Create a new ClusterRole named prevent-role, which uses the newly created Pod Security Policy prevent-privileged-policy.
Create a new ClusterRoleBinding named prevent-role-binding, which binds the created ClusterRole prevent-role to the created SA psp-sa.
Also, Check the Configuration is working or not by trying to Create a Privileged pod, it should get failed.
A. See the below.
B. PlaceHolder
Service is running on port 389 inside the system, find the process-id of the process, and stores the names of all the open-files inside the /candidate/KH77539/files.txt, and also delete the binary.
A. See explanation below.
B. PlaceHolder
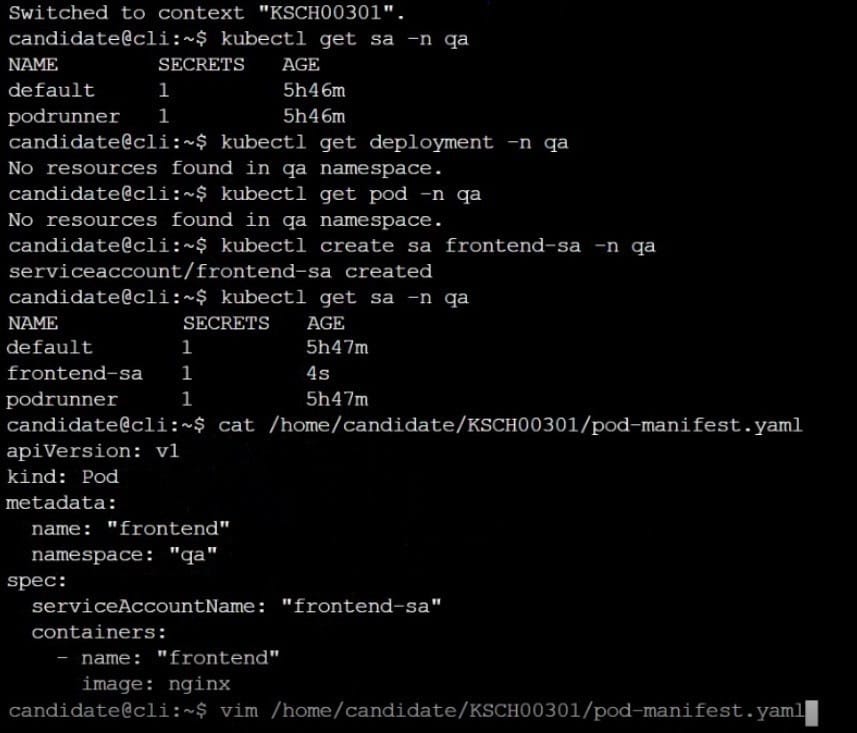
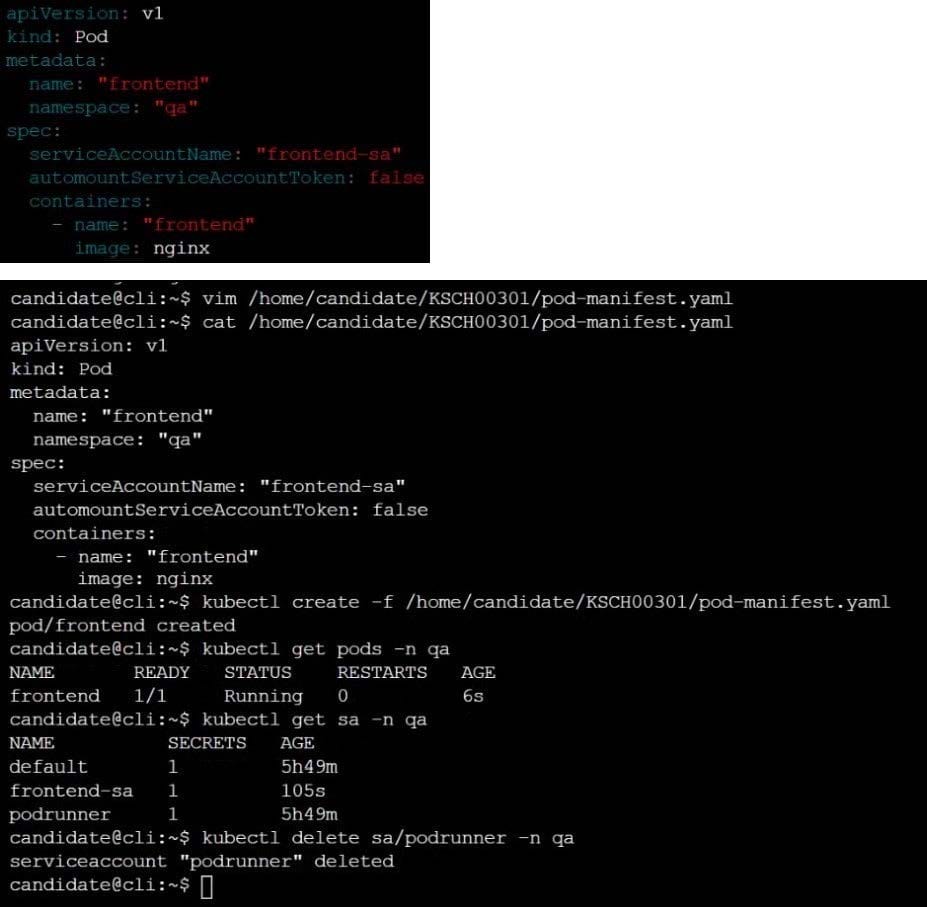
You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context stage
Context:
A PodSecurityPolicy shall prevent the creation of privileged Pods in a specific namespace.
Task:
1.
Create a new PodSecurityPolcy named deny-policy, which prevents the creation of privileged Pods.
2.
Create a new ClusterRole name deny-access-role, which uses the newly created PodSecurityPolicy deny-policy.
3.
Create a new ServiceAccount named psd-denial-sa in the existing namespace development.
Finally, create a new ClusterRoleBindind named restrict-access-bind, which binds the newly created ClusterRole deny-access-role to the newly created ServiceAccount psp-denial-sa
A. See the explanation below
B. PlaceHolder
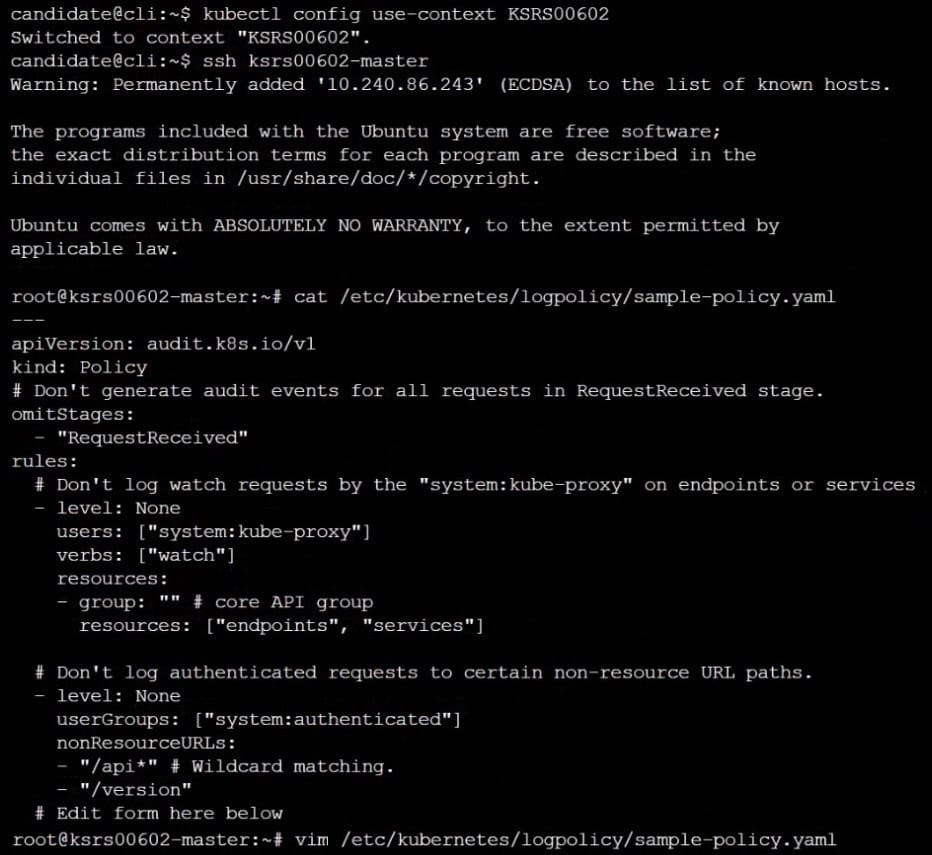
You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context dev
Context:
A CIS Benchmark tool was run against the kubeadm created cluster and found multiple issues that must be addressed.
Task:
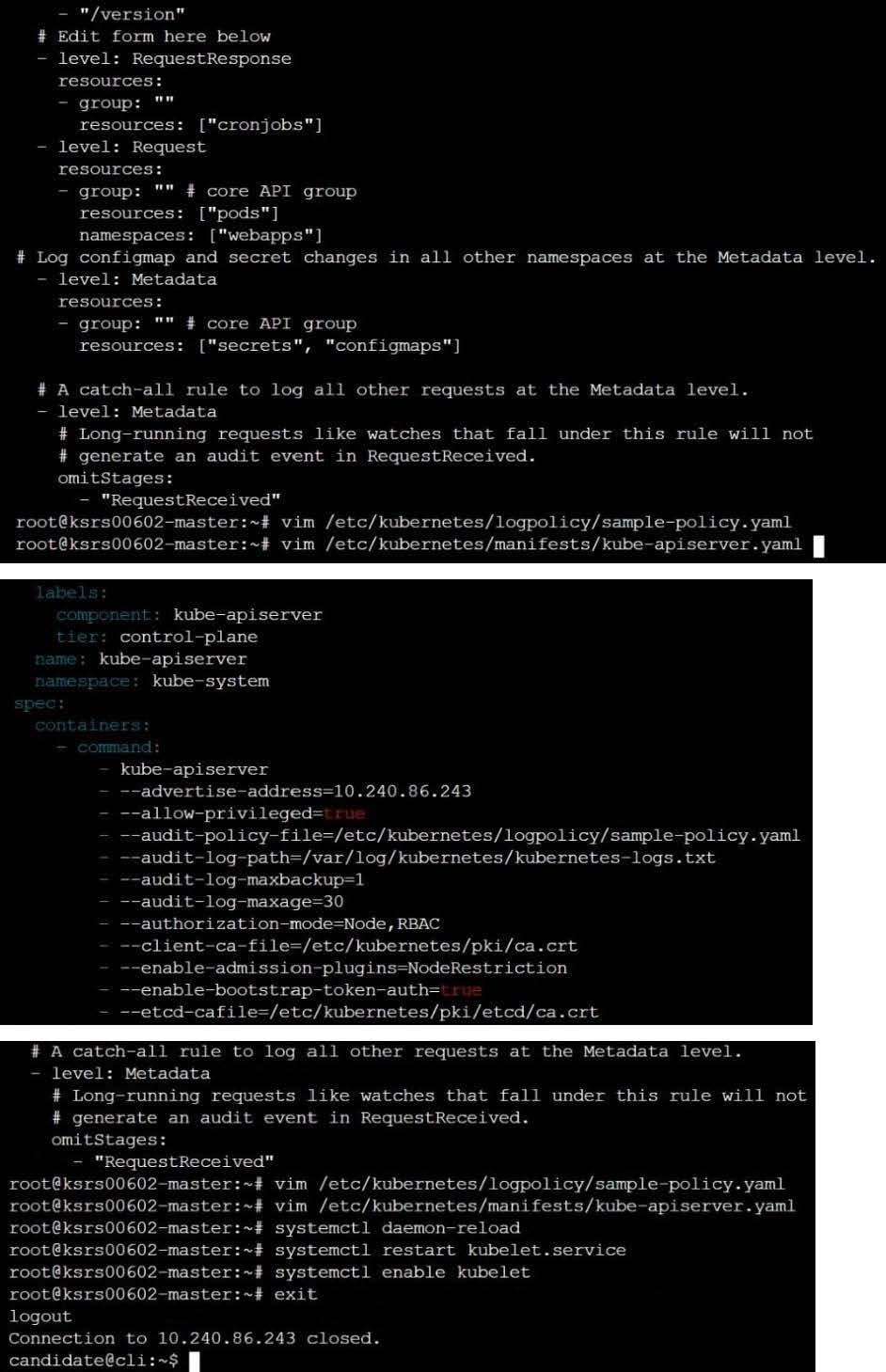
Fix all issues via configuration and restart the affected components to ensure the new settings take effect.
Fix all of the following violations that were found against the API server:
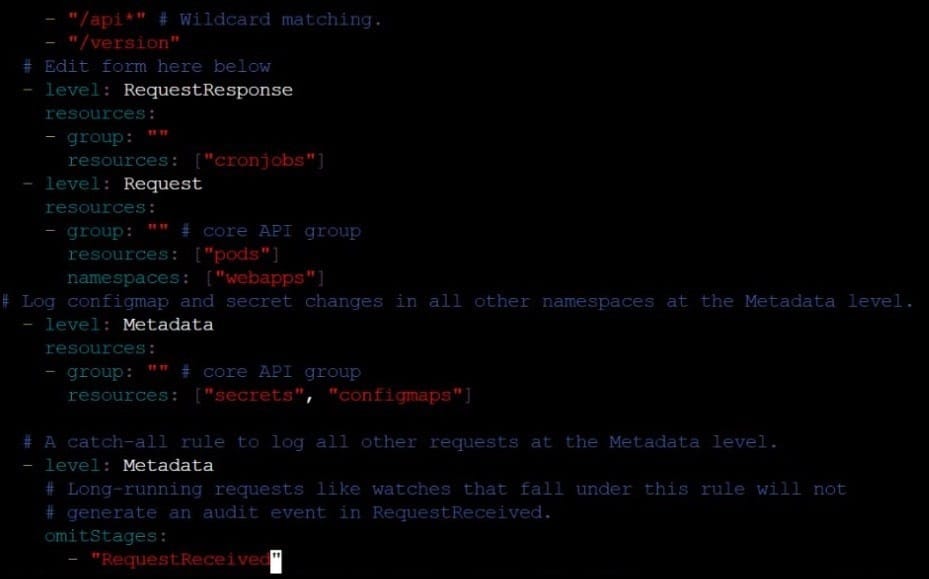
1.2.7 authorization-mode argument is not set to AlwaysAllow FAIL
1.2.8 authorization-mode argument includes Node FAIL
1.2.7 authorization-mode argument includes RBAC FAIL
Fix all of the following violations that were found against the Kubelet:
4.2.1 Ensure that the anonymous-auth argument is set to false FAIL
4.2.2 authorization-mode argument is not set to AlwaysAllow FAIL (Use Webhook autumn/authz where possible)
Fix all of the following violations that were found against etcd:
2.2 Ensure that the client-cert-auth argument is set to true
A. See the explanation below
B. PlaceHolder
CORRECT TEXT
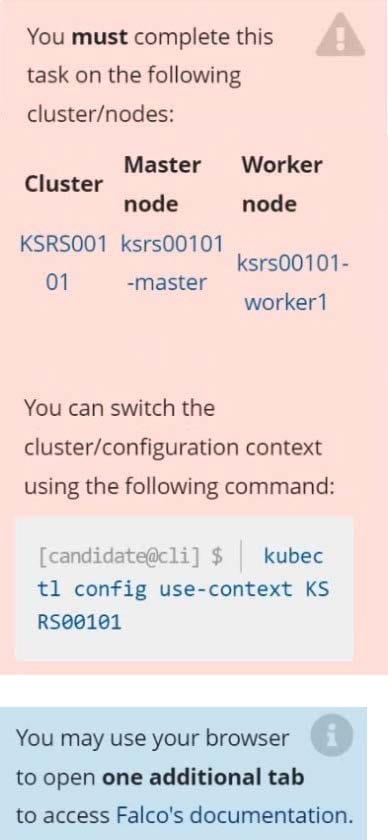
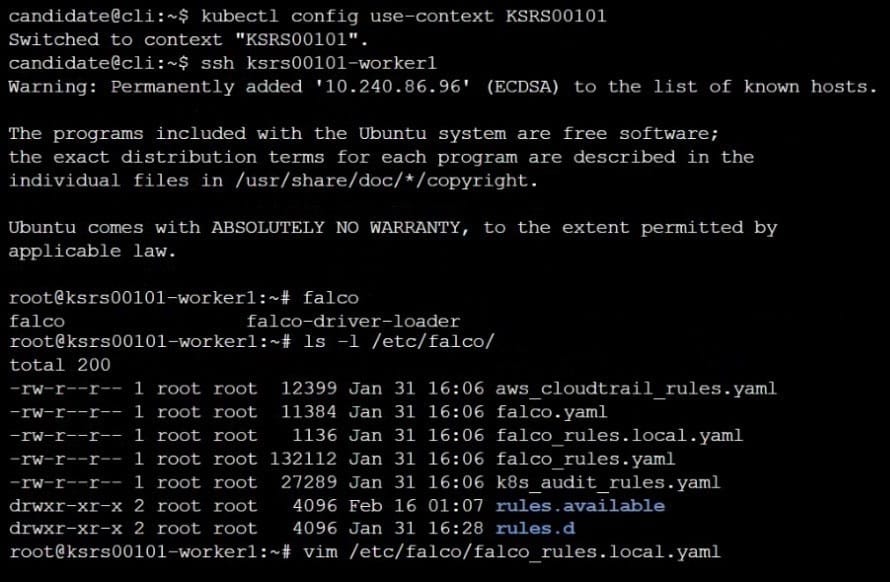
Two tools are pre-installed on the cluster's worker node:
1.
sysdig
2.
falco
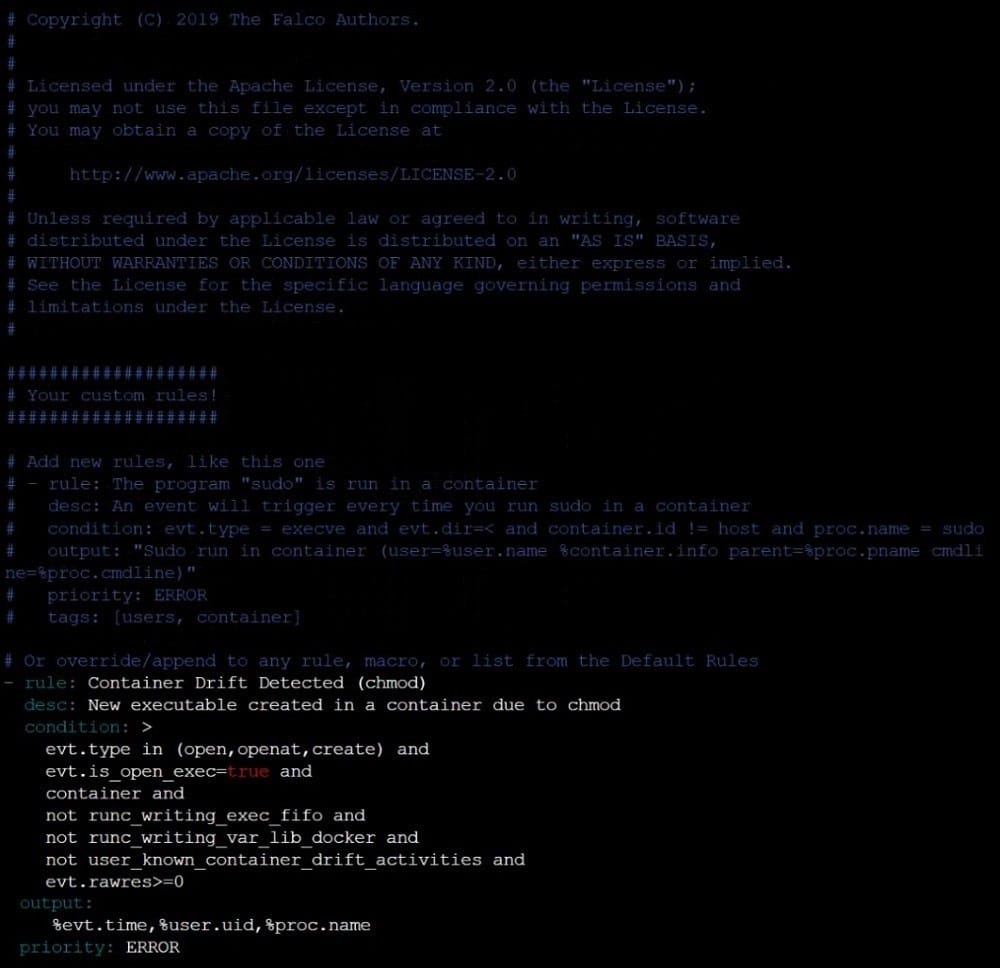
Using the tool of your choice (including any non pre-installed tool), analyze the container's behavior for at least 30 seconds, using filters that detect newly spawning and executing processes. Store an incident file at /opt/KSRS00101/alerts/
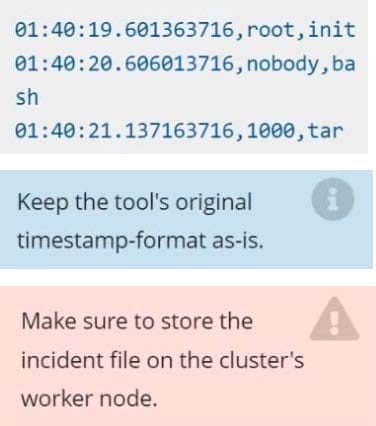
details, containing the detected incidents, one per line, in the following format:

The following example shows a properly formatted incident file:
A. See the explanation below:
B. PlaceHolder
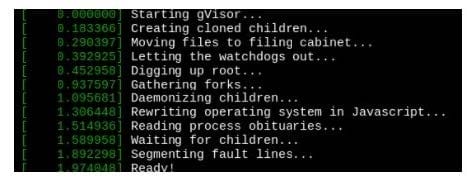
Create a RuntimeClass named untrusted using the prepared runtime handler named runsc.
Create a Pods of image alpine:3.13.2 in the Namespace default to run on the gVisor runtime class.
A. See the explanation below:
B. PlaceHolder
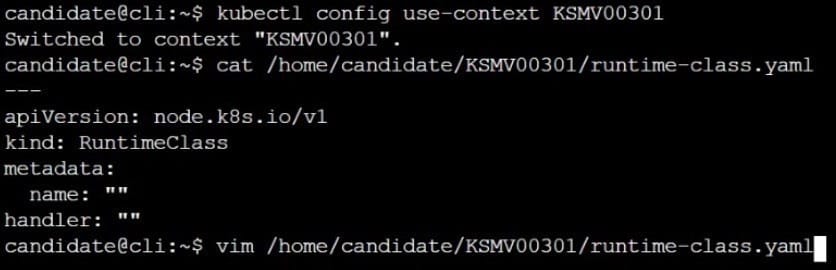
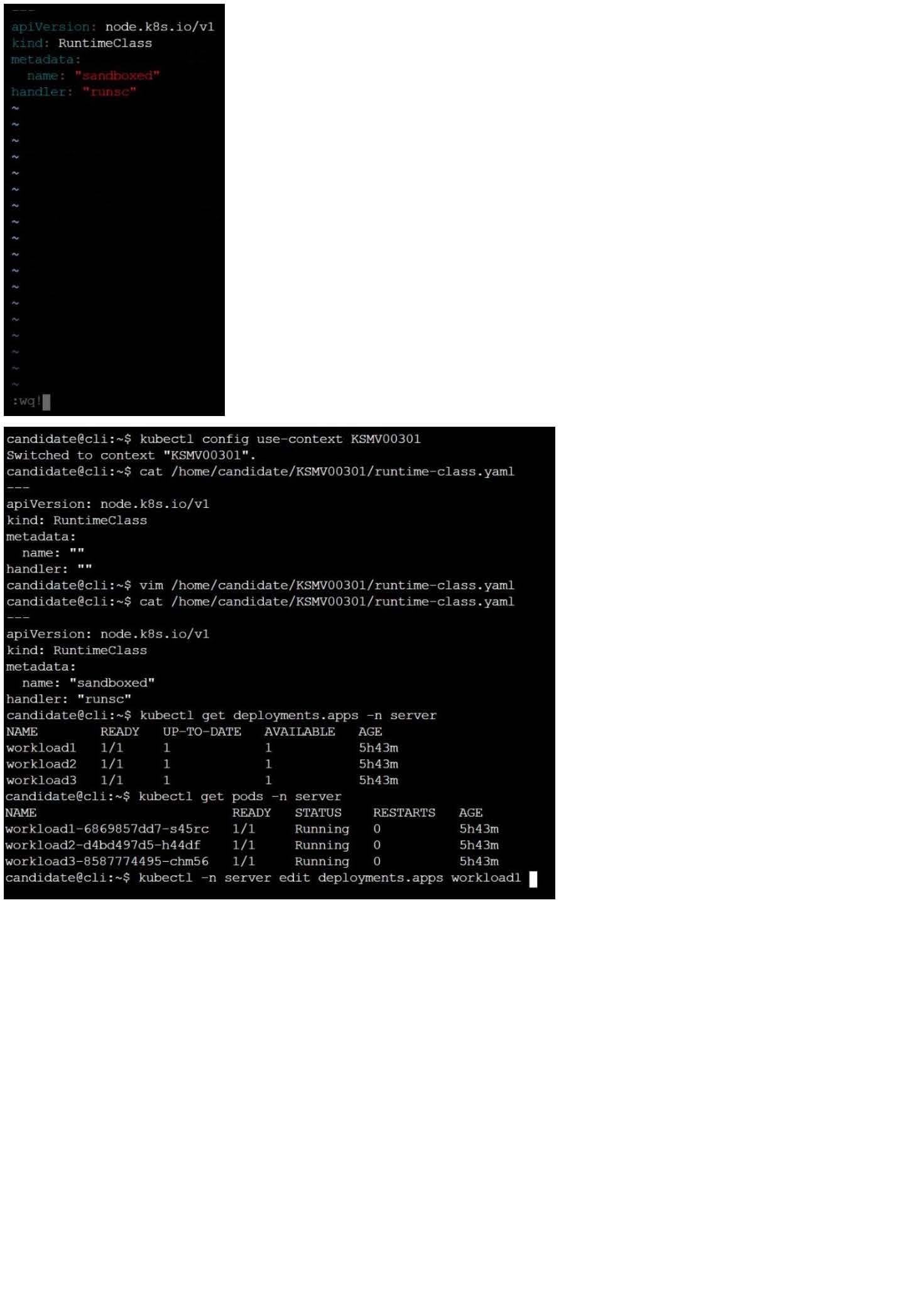
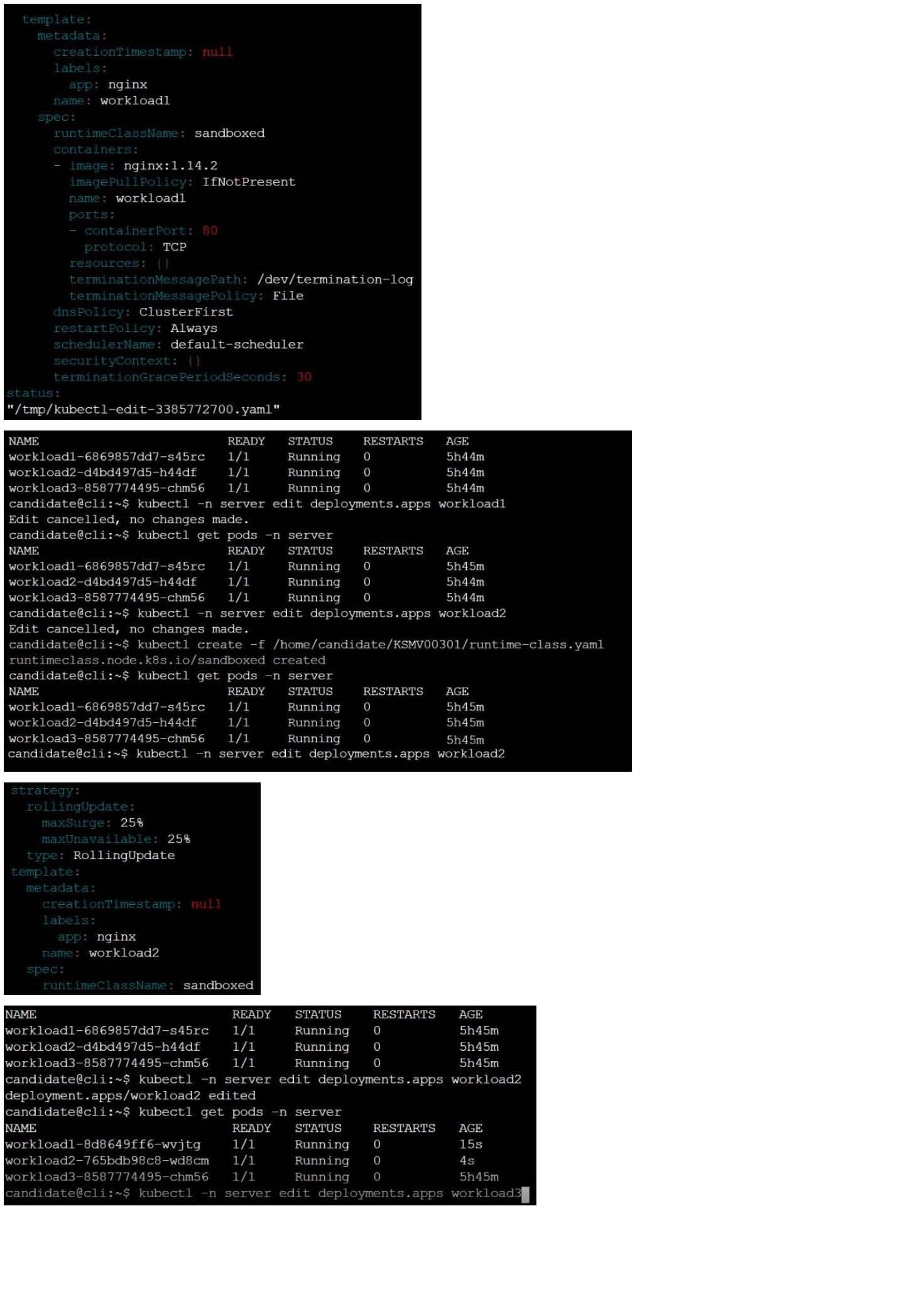
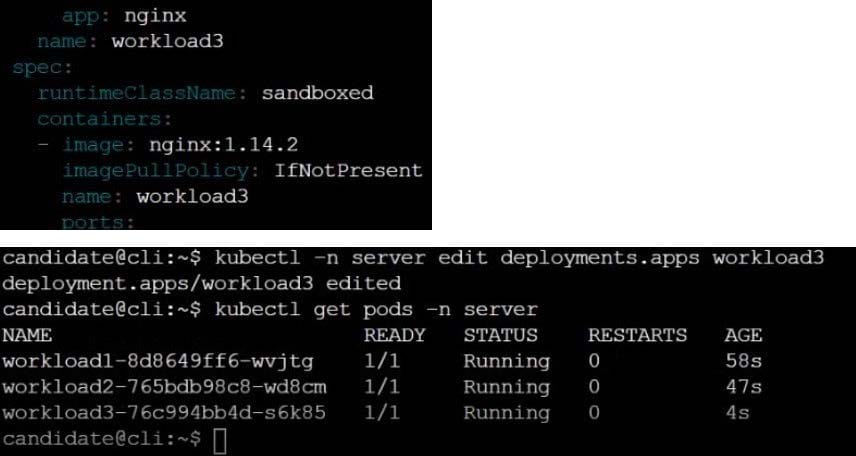
CORRECT TEXT
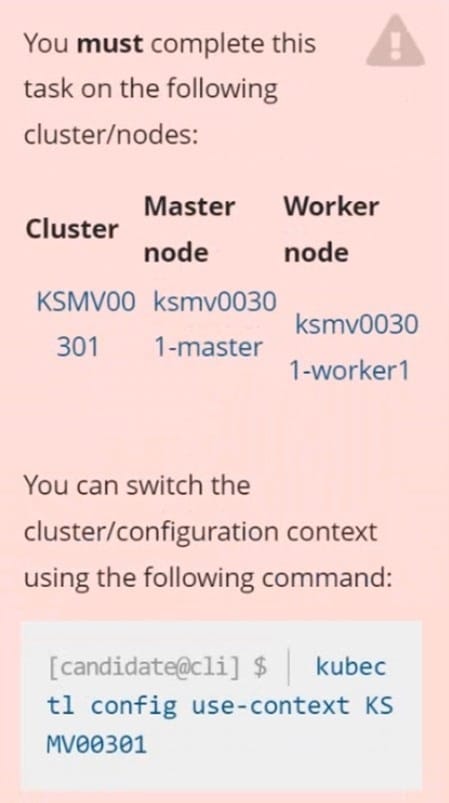
Context
This cluster uses containerd as CRI runtime.
Containerd's default runtime handler is runc. Containerd has been prepared to support an additional runtime handler, runsc (gVisor).
Task
Create a RuntimeClass named sandboxed using the prepared runtime handler named runsc.
Update all Pods in the namespace server to run on gVisor.
A. See the explanation below
B. PlaceHolder