CISSP-2018 Online Practice Questions and Answers
HOTSPOT
Which Web Services Security (WS-Security) specification handles the management of security tokens and the underlying policies for granting access? Click on the correct specification in the image below.
Hot Area:

HOTSPOT
Which Web Services Security (WS-Security) specification negotiates how security tokens will be issued, renewed and validated? Click on the correct specification in the image below.
Hot Area:

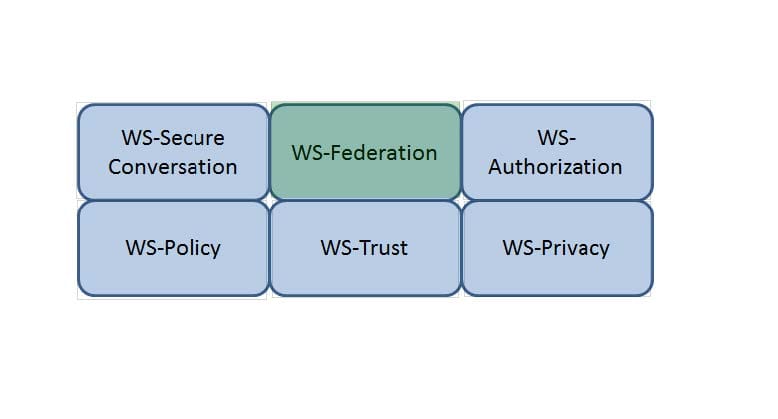
HOTSPOT
Which Web Services Security (WS-Security) specification maintains a single authenticated identity across multiple dissimilar environments? Click on the correct specification in the image below.
Hot Area:

HOTSPOT
Identify the component that MOST likely lacks digital accountability related to information access. Click on the correct device in the image below.
Hot Area:

HOTSPOT
In the network design below, where is the MOST secure Local Area Network (LAN) segment to deploy a Wireless Access Point (WAP) that provides contractors access to the Internet and authorized enterprise services?
Hot Area:

DRAG DROP
In which order, from MOST to LEAST impacted, does user awareness training reduce the occurrence of the events below?
Select and Place:

DRAG DROP
Place the following information classification steps in sequential order.
Select and Place:

DRAG DROP
Place in order, from BEST (1) to WORST (4), the following methods to reduce the risk of data remanence on magnetic media.
Select and Place:

DRAG DROP
Drag the following Security Engineering terms on the left to the BEST definition on the right.
Select and Place:

DRAG DROP
Order the below steps to create an effective vulnerability management process.
Select and Place:

DRAG DROP
Given the various means to protect physical and logical assets, match the access management area to the technology.
Select and Place:

DRAG DROP
Match the objectives to the assessment questions in the governance domain of Software Assurance Maturity Model (SAMM).
Select and Place:

DRAG DROP
During the risk assessment phase of the project the CISO discovered that a college within the University is collecting Protected Health Information (PHI) data via an application that was developed in-house. The college collecting this data is
fully aware of the regulations for Health Insurance Portability and Accountability Act (HIPAA) and is fully compliant.
What is the best approach for the CISO?
Below are the common phases to creating a Business Continuity/Disaster Recovery (BC/DR) plan. Drag the remaining BC\DR phases to the appropriate corresponding location.
Select and Place:

DRAG DROP
A software security engineer is developing a black box-based test plan that will measure the system's reaction to incorrect or illegal inputs or unexpected operational errors and situations. Match the functional testing techniques on the left with the correct input parameters on the right.
Select and Place:

DRAG DROP
Match the access control type to the example of the control type. Drag each access control type net to its corresponding example.
Select and Place: