CAS-002 Online Practice Questions and Answers
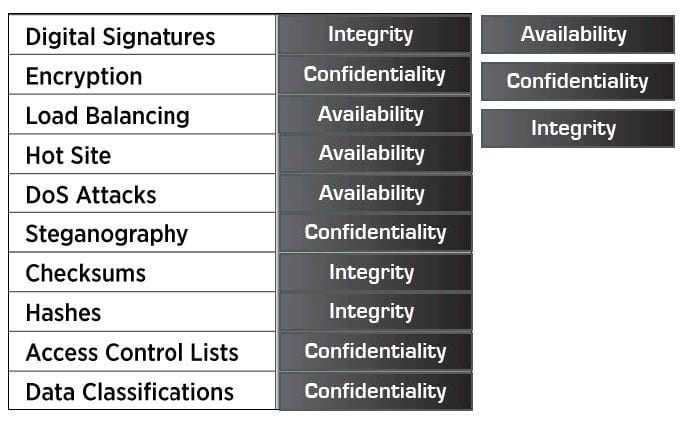
Drag and Drop the following information types on to the appropriate CIA category.
Select and Place:
The security administrator is reviewing the business continuity plan which consists of virtual infrastructures at corporate headquarters and at the backup site. The administrator is concerned that the VLAN used to perform live migrations of
virtual machines to the backup site is across the network provider's MPLS network.
This is a concern due to which of the following?
A. The hypervisor virtual switches only support Q-in-Q VLANS, not MPLS. This may cause live migrations to the backup site to fail.
B. VLANs are not compatible with MPLS, which may cause intermittent failures while performing live migrations virtual machines during a disaster.
C. Passwords are stored unencrypted in memory, which are then transported across the MPLS network.
D. Transport encryption is being used during the live migration of virtual machines which will impact the performance of the MPLS network.
The security administrator of a large enterprise is tasked with installing and configuring a solution that will allow the company to inspect HTTPS traffic for signs of hidden malware and to detect data exfiltration over encrypted channels. After installing a transparent proxy server, the administrator is ready to configure the HTTPS traffic inspection engine and related network equipment. Which of the following should the security administrator implement as part of the network and
proxy design to ensure the browser will not display any certificate errors when browsing HTTPS sites? (Select THREE).
A. Install a self-signed Root CA certificate on the proxy server.
B. The proxy configuration of all users' browsers must point to the proxy IP.
C. TCP port 443 requests must be redirected to TCP port 80 on the web server.
D. All users' personal certificates' public key must be installed on the proxy.
E. Implement policy-based routing on a router between the hosts and the Internet.
F. The proxy certificate must be installed on all users' browsers.
A sensitive database needs its cryptographic integrity upheld. Which of the following controls meets this goal? (Select TWO).
A. Data signing
B. Encryption
C. Perfect forward secrecy
D. Steganography
E. Data vaulting
F. RBAC
G. Lock and key
The helpdesk manager wants to find a solution that will enable the helpdesk staff to better serve company employees who call with computer-related problems. The helpdesk staff is currently unable to perform effective troubleshooting and relies on callers to describe their technology problems. Given that the helpdesk staff is located within the company headquarters and 90% of the callers are telecommuters, which of the following tools should the helpdesk manager use to make the staff more effective at troubleshooting while at the same time reducing company costs? (Select TWO).
A. Web cameras
B. Email
C. Instant messaging
D. BYOD
E. Desktop sharing
F. Presence
An organization has decided to reduce labor costs by outsourcing back office processing of credit applications to a provider located in another country. Data sovereignty and privacy concerns raised by the security team resulted in the third-party provider only accessing and processing the data via remote desktop sessions. To facilitate communications and improve productivity, staff at the third party has been provided with corporate email accounts that are only accessible via the remote desktop sessions. Email forwarding is blocked and staff at the third party can only communicate with staff within the organization. Which of the following additional controls should be implemented to prevent data loss? (Select THREE).
A. Implement hashing of data in transit
B. Session recording and capture
C. Disable cross session cut and paste
D. Monitor approved credit accounts
E. User access audit reviews
F. Source IP whitelisting
A network engineer wants to deploy user-based authentication across the company's wired and wireless infrastructure at layer 2 of the OSI model. Company policies require that users be centrally managed and authenticated and that each user's network access be controlled based on the user's role within the company. Additionally, the central authentication system must support hierarchical trust and the ability to natively authenticate mobile devices and workstations. Which of the following are needed to implement these requirements? (Select TWO).
A. SAML
B. WAYF
C. LDAP
D. RADIUS
E. Shibboleth
F. PKI
Which of the following provides the BEST risk calculation methodology?
A. Annual Loss Expectancy (ALE) x Value of Asset
B. Potential Loss x Event Probability x Control Failure Probability
C. Impact x Threat x Vulnerability
D. Risk Likelihood x Annual Loss Expectancy (ALE)
A small company is developing a new Internet-facing web application. The security requirements are:
1.
Users of the web application must be uniquely identified and authenticated.
2.
Users of the web application will not be added to the company's directory services.
3.
Passwords must not be stored in the code. Which of the following meets these requirements?
A. Use OpenID and allow a third party to authenticate users.
B. Use TLS with a shared client certificate for all users.
C. Use SAML with federated directory services.
D. Use Kerberos and browsers that support SAML.
The following has been discovered in an internally developed application:
Error - Memory allocated but not freed:
char *myBuffer = malloc(BUFFER_SIZE);
if (myBuffer != NULL) {
*myBuffer = STRING_WELCOME_MESSAGE;
printf("Welcome to: %s\n", myBuffer);
}
exit(0);
Which of the following security assessment methods are likely to reveal this security weakness? (Select TWO).
A. Static code analysis
B. Memory dumping
C. Manual code review
D. Application sandboxing
E. Penetration testing
F. Black box testing
The network administrator at an enterprise reported a large data leak. One compromised server was used to aggregate data from several critical application servers and send it out to the Internet using HTTPS. Upon investigation, there have been no user logins over the previous week and the endpoint protection software is not reporting any issues. Which of the following BEST provides insight into where the compromised server collected the information?
A. Review the flow data against each server's baseline communications profile.
B. Configure the server logs to collect unusual activity including failed logins and restarted services.
C. Correlate data loss prevention logs for anomalous communications from the server.
D. Setup a packet capture on the firewall to collect all of the server communications.
A systems security consultant is hired by Corporation X to analyze the current enterprise network environment and make recommendations for increasing network security. It is the consultant's first day on the job. Which of the following network design considerations should the consultant consider? (Select THREE).
A. What hardware and software would work best for securing the network?
B. What corporate assets need to be protected?
C. What are the business needs of the organization?
D. What outside threats are most likely to compromise network security?
E. What is the budget for this project?
F. What time and resources are needed to carry out the security plan?
A security administrator wants to perform an audit of the company password file to ensure users are not using personal information such as addresses and birthdays as part of their password. The company employs 200,000 users, has virtualized environments with cluster and cloud-based computing resources, and enforces a minimum password length of 14 characters. Which of the following options is BEST suited to run the password auditing software and produce a report in the SHORTEST amount of time?
A. The system administrator should take advantage of the company's cluster based computing resources, upload the password file to the cluster, and run the password cracker on that platform.
B. The system administrator should upload the password file to a virtualized de-duplicated storage system to reduce the password entries and run a password cracker on that file.
C. The system administrator should build a virtual machine on the administrator's desktop, transfer the password file to it, and run the a password cracker on the virtual machine.
D. The system administrator should upload the password file to cloud storage and use on- demand provisioning to build a purpose based virtual machine to run a password cracker on all the users.
A Physical Security Manager is ready to replace all 50 analog surveillance cameras with IP cameras with built-in web management. The Security Manager has several security guard desks on different networks that must be able to view the cameras without unauthorized people viewing the video as well. The selected IP camera vendor does not have the ability to authenticate users at the camera level. Which of the following should the Security Manager suggest to BEST secure this environment?
A. Create an IP camera network and deploy NIPS to prevent unauthorized access.
B. Create an IP camera network and only allow SSL access to the cameras.
C. Create an IP camera network and deploy a proxy to authenticate users prior to accessing the cameras.
D. Create an IP camera network and restrict access to cameras from a single management host.
During an incident involving the company main database, a team of forensics experts is hired to respond to the breach. The team is in charge of collecting forensics evidence from the company's database server. Which of the following is the correct order in which the forensics team should engage?
A. Notify senior management, secure the scene, capture volatile storage, capture non- volatile storage, implement chain of custody, and analyze original media.
B. Take inventory, secure the scene, capture RAM, capture had drive, implement chain of custody, document, and analyze the data.
C. Implement chain of custody, take inventory, secure the scene, capture volatile and non- volatile storage, and document the findings.
D. Secure the scene, take inventory, capture volatile storage, capture non-volatile storage, document, and implement chain of custody.