C9510-401 Online Practice Questions and Answers
A system administrator is asked by a development team to monitor the performance of a newly deployed EJB application. The administrator noticed that the heap size of the application server is growing.
What should the administrator do to fix the problem using ORB settings?
A. Use J2EE managed object MBeans.
B. Enable the pass by reference option.
C. Disable the application scoped resources in the application deployment descriptor.
D. Ensure that Process embedded configurations is not selected when exporting the EAR.
A system administrator wants to learn some of the Python scripting commands for the administration of the environment.
Which product feature should the administrator use?
A. The wsadmin.properties file to load a profile.
B. The AdminTask object to generate wsadmin scripts.
C. The guided activities panel from the Integrated Solutions Console (ISC).
D. The "Log command assistance commands" option in the Integrated Solutions Console (ISC).
A system administrator needs to configure a JDBC provider and a data source for an application in a clustered environment. The administrator also needs to copy the JDBC drivers from the database server to the application server machines.
How can the administrator meet these requirements?
A. Create a JDBC provider and the data source in the cluster scope.Copy the driver to all nodes.Set the environment variable at the node level to the driver's path.
B. Create a JDBC provider in the server scope and the data source in the node scope.Copy the driver to all application servers.Set the environment variable at the node level to the driver's path.
C. Create a JDBC provider in the node scope and the data source in the cell scope.Copy the driver to the deployment manager.Set the environment variable at the server level to point to the deployment manager path.
D. Create a JDBC provider in the application scope and the data source in the server scope.Copy the driver to all application server directories.Set the environment variable in each JVM to the driver's path.
A performance test team was testing the capacity of concurrent users of a web application deployed on a multi-processor server. While testing 250 concurrent users, the administrator discovers connections to the database are failing.
In response, a system administrator increased the connection pool to the maximum limit which the database allows and increased the prepared statement cache size. The test passed, but the application response time was slower.
How should the system administrator tune the data source properties to improve the application response time?
A. Change connection pools purge policy.
B. Decrease connection pool reap time.
C. Decrease number of free pool partitions.
D. Decrease the prepared statement cache size.
While coordinating a flexible management topology, the job manager can send commands to which components?
A. Application server and name server.
B. On demand router and load balancer.
C. Deployment manager and admin agent.
D. Node agent and web administration server.
A system administrator has configured a cluster containing 40 servers. The cluster members all belong to one core group. While examining the log files, the administrator notices that the core group coordinator is consuming abnormally high amounts of memory and CPU resources. How can the system administrator reduce the memory and CPU resource usage of the core group coordinator?
A. Configure a core group bridge.
B. Configure a second active coordinator.
C. Decrease the memory on the machine.
D. Move the coordinator to another machine.
A system administrator has added a server cluster as a member of a service integration bus (SIB). The administrator needs to configure one messaging engine for each server in this cluster and to have a failover location for each messaging engine.
What should the administrator do to achieve the required design?
A. Configure a new messaging engine in each server to support failover.
B. Configure the data store for each messaging engine for each server in the cluster.
C. Select scalability with high availability as the messaging engine policy.
D. Create a core group policy to restrict each messaging engine to a particular server.
Which of the following comprises an initial Liberty profile server process?
A. A single JVM, the Liberty kernel, and feature manager.
B. A single JVM, and OSGI framework and an object request broker.
C. an OSGI framework, a web container and an EJB container.
D. AN administrative agent, the Liberty kernel and shared libraries.
A system administrator was asked by the development team to inform them of any warning message which contains a string "Connection" on a WebSphere Application Server with High Performance Extensible Logging (HPEL) enabled.
A. Configure log detail levels to include filter on "Connection" string.
B. Use the Log Viewer in the administrative console with filter on "Connection" string.
C. Use the logviewer.sh or logviewer.bat command with appropriate options.
D. Use the Log Viewer in the administrative console with filter on "Connection" string and enable the "Refresh automatically" feature.
A system administrator needs to deploy a new enterprise application which requires that application security be enabled, but, the existing applications in the cell cannot be executed with application security enabled. The cell has the global security and Java 2 security disabled.
How can the administrator handle this requirement?
A. Enable Java 2 security for the cell.Create a security domain with application security enabled.Associate the security domain to the new application.
B. Enable Java 2 security for the cell.Create a security domain with application security enabled.Associate the security domain to a new cluster to be used to deploy the new application.
C. Enable administrative security for the cell.Create a security domain with application security enabled.Associate the security domain at the application level for the new application.
D. Enable administrative security for the cell.Create a security domain with application security enabled.Associate the security domain to the new cluster where the new application is deployed.
A new cell contains a cluster with members defined in two managed nodes running on two different machines. The cell also contains two unmanaged nodes running on HTTP servers with HTTP plug-in. Session persistence has been enabled.
Which additional component(s) can the system administrator configure to make this environment highly available?
A. Enable administrative security.
B. Configure a DMZ secure proxy.
C. Configure High Performance Extensible Logging.
D. Configure primary and backup load balancers for the HTTP servers.
A system administrator needs to install WebSphere Application Server Network Deployment V8.5.5 multiple times and would like to automate the task of installing the product. The administrator wants to create a response file based on an initial installation and use this for future installations.
How can the administrator accomplish this task?
A. Use the IBM Packaging Utility.
B. Use the Installation Manager console mode.
C. Complete a silent installation with the -log option.
D. Start the Installation Manager GUI with the -record option.
A system administrator ran the backup Config command to backup the configuration using the -nostop option. The administrator changed the properties for the service integration environment by modifying the sib.properties file. During testing the administrator noticed Service Integration Bus related errors and wanted to restore the service integration environment. The administrator used the restore config command, but the tuning properties for the service integration environment were not restored.
How can the administrator prevent this issue?
A. Use full repository checkpoints for both the backup and the restore.
B. Use the restore config command with -nostop for the restore.
C. Use the manage profiles command for both the backup and the restore.
D. Use the backup config command without -nostop for the backup.
E. Use the restore config command without -nostop for the restore.
A web application is hosted on an application server that receives HTTP requests from a third party application named myApp. The URIGroup mapping for this application is called default_host_myApp.
The development team asks a system administrator to configure the HTTP plug-in to prevent routing requests to any application server except server1.
The following exhibit shows the parts of the plugin-cfg.xml file that are relevant for myApp. The UriGroups for other applications are not shown in the exhibit.
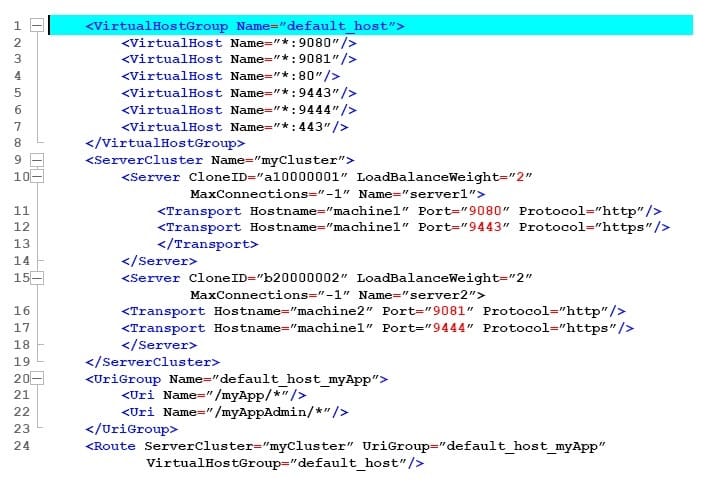
What should the administrator do to the plugin-cfg.xml file to ensure that requests for default_host_myApp URIGroup are routed only to machine1?
A. Delete the Server tag for CloneId="b20000002"Delete all of the tags within the Server tag
B. Delete the UriGroup tag for default_host_myAppDelete all of the tags within the UriGroup tag
C. Delete the VirtualHostGroup tag for default_hostDelete all of the tags within the VirtualHostGroup tag
D. Edit the LoadBalanceWeight for server1 to 20Edit the LoadBalanceWeight for server2 to
An application contains a web services client and the application is deployed and running. A system administrator has to add a response timeout to the deployed web services client, so the call fails in a timely fashion.
Which artifact should the administrator use?
A. web.xml
B. was-webservices-sca.xml
C. ibm-webservices-bnd.xml
D. ibm-webservicesclient-bnd.xml
