C2150-609 Online Practice Questions and Answers
A customer has a developed an OAuth 2.0 Client application to access resources on behalf of a user. The customer states that the OAuth client has the following two constraints:
1.
The OAuth client is not capable of maintaining its credentials confidential for authentication with the authorization server.
2.
The resources owner does not have a trust relationship with the client.
What is the suitable OAuth 2.0 grant type for the API Protection Policy if the user resource accessed by the OAuth 2.0 client is to be protected by IBM Security Access Manager V9.0?
A. Implicit Grant
B. Client Credential Grant
C. Authorization Code Grant
D. Resource Owner Password Credentials Grant
After a test cycle the deployment professional wants to search the WebSEAL WGA1 instance request log for HTTP 404 responses.
Where can this log be found in the Local Management Interface?
A. Monitor> Manage Reverse Proxy Log Files, select the WGA1 instance, select the request.log file and click View
B. Monitor> Application Log Files, expand the var/logs/pdweb/WGA 1 folder, select the request.log file and click View
C. From the Home page, click on the WGA1 instance in Reverse Proxy Health widget, select the request.log file and click View.
D. Secure Web Settings> Reverse Proxy, select the WGA1 instance, access the Manage> Troubleshooting> Tracing menu item, select the request.log file and click View
A customer has configured the IBM Security Access Manager V9.0 appliance authentication to an external LDAP server. The customer wants to allow support staff with LDAP accounts that are members of the HelpDesk group to view appliance and audit logs.
Where should the deployment professional configure a new role and map it to the HelpDesk LDAP group for the support staff?
A. Manage System Settings-> Management Delegation
B. Manage System Settings-> Administrator Settings
C. Manage System Settings-> Management Authorization
D. Manage System Settings-> Management Authentication
The Distributed Session Cache has been enabled to replace the Session Management Server in a recently migrated IBM Security Access Manager V9.0 environment. Several Reverse Proxies have not yet been migrated from ISAM V7.0. The help desk is now receiving user complaints due to multiple logins required for applications protected by the ISAM V7.0 Reverse Proxies.
Which Distributed Session Cache option should be checked?
A. enable_sms-functionality
B. provide_700_attribute_ids
C. Replicate certificate databases
D. Support internal and external clients
A company has deployed an IBM Security Manager V9.0 solution to protect web resources and now wants to secure access to enterprise resources from mobile devices. The security deployment professional needs to run a utility to configure the existing WebSEAL with the instance of the appliance that provides the authorization server for Advanced Access Control.
Which utility tool will perform this configuration?
A. isamcfg
B. pdadmin
C. Web Administration Tool (WAT)
D. Middleware Configuration Utility
A deployment professional has created an Access Control Policy to protect sensitive business information: Which Policy decision is returned for a user with a risk score of 35 and has consented to registering a device?
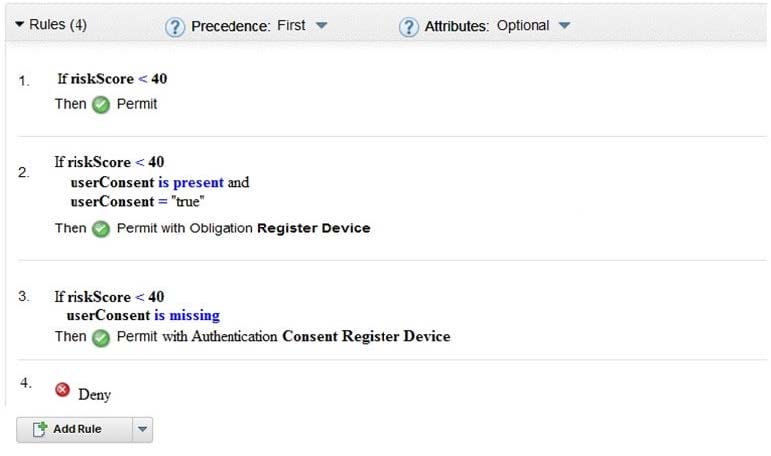
A. Deny
B. Permit
C. Permit with Obligation Register Device
D. Permit with Authentication Consent Register Device
A deployment professional has created a new SAML 2.0 Service Provider federation and added an Identity Provider partner.
What will be the next step to allow users to single sign-on to the service?
A. Configure trigger URL
B. Upload a mapping rule
C. Import Identity Provider metadata
D. Create a certificate to sign SAML messages
The IBM Security Access Manager (ISAM) V9.0 deployment professional has recently discovered an entire deployment of over 100 junctions was performed incorrectly.
How can a repair operation be scripted for this, and future deployment personnel?
A. Use the CLI SSH interface, navigating to isam-> admin and authenticating as sec_master.
B. Use a text editor and create the correct junction XML files, then import them using the LMI.
C. Use the LMI Secure Web Settings-> Reverse Proxy-> Manage-> Junction Management interface.
D. Use the REST API interface https://{appliance_hostname}/isam/pdadmin, JSON files and the CURL utility.
The security deployment professional of an IBM Security Access Manager V9.0 solution has been using routing files to customize message logging.
Which aspect of the logging activity can be controlled?
A. Size of log file
B. Delete log files
C. Log compression
D. HTML formatting
IBM Security Access Manager (ISAM) V.90 provides an External Authentication Interface (EAI) that enables the extension of the authentication process for WebSEAL. The identity information returned by the EAI service is used to generate user credentials. This can be used as one of the methods to implement step-up authentication.
How is this authentication information returned from the EAI server?
A. HTTP headers
B. HTTP parameters
C. [step-up] stanza
D. [authentication-levels] stanza
There are random network errors occurring so the IBM Security Access Manager V9.0 deployment specialist has decided to enable Packet Tracing and feed the resulting pcap file into Wireshark for analysis.
Which information is required to enable this feature?
A. Filter
B. Protocol
C. Destination IP
D. Trace file size
A customer is deploying an IBM Security Access Manager V9.0 solution to protect back end resources and is planning to use an LDAP Server that is set up to use SSL server authentication.
What is required to enable SSL to secure communications with LDAP?
A. LDAP server's private key
B. LDAP server's public key stash file
C. LDAP server's CA signer certificate
D. LDAP server's private and public key
A customer has an IBM Security Access Manager V9.0 appliance cluster spanning two data centers A and
B. Data center A has the Primary Master and two Restricted nodes. Data center B has a Secondary Master
and two Restricted Nodes.
A Load Balancer with redundancy across data centers provides sticky load balancing to reverse proxies in
both data centers.
What is true if a disaster recovery testing scenario takes down all appliances in data center A?
A. The Secondary Master will automatically be promoted to Primary Master
B. Reverse Proxies in Data Center B will service all end-users with no intervention
C. The Secondary Master has to be promoted to Primary for Data Center B to service end-users
D. Reverse Proxies in Data Center B need to be recycled sequentially to handle users assigned Data Center A reverse proxies.
The deployment professional wants to back up the embedded LDAP personal certificate, including the private key. They navigate to Manage System Settings -> SSL Certificates -> and select the "extract" option.
Which file format is the resulting certificate backup?
A. .p12
B. .kdb
C. .jks
D. .cer
Prior to installing a firmware update the deployment professional creates a snapshot of the appliance configuration. During acceptance testing of the new firmware it is discovered that the update introduced a bug.
How should the deployment professional restore the previous configuration?
A. Manage System Settings > System Settings > Snapshots, select the snapshot and click Apply
B. Manage System Settings > System Settings > Snapshots, select the snapshot and click Restore
C. Manage System Settings > Updates and Licensing > Available Updates, select the update and click Uninstall
D. Manage System Settings > Updates and Licensing > Firmware Settings, click the Set Active link on the inactive partition
