C1000-018 Online Practice Questions and Answers
An analyst wants to analyze the long-term trending of data from a search. Which chart would be used to display this data on a dashboard?
A. Bar Graph
B. Time Series chart
C. Pie Chart
D. Scatter Chart
An analyst is encountering a large number of false positive results. Legitimate internal network traffic contains valid flows and events which are making it difficult to identify true security incidents.
What can the analyst do to reduce these false positive indicators?
A. Create X-Force rules to detect false positive events.
B. Create an anomaly rule to detect false positives and suppress the event.
C. Filter the network traffic to receive only security related events.
D. Modify rules and/or Building Block to suppress false positive activity.
An auditor has requested a report for all Offenses that have happened in the past month. This report generates at the end of every month but the auditor needs to have it for a meeting that is in the middle of the month.
What will happen to the scheduled report if the analyst manually generates this report?
A. The scheduled report needs to be reconfigured.
B. The analyst needs to delete the scheduled report and create a new one.
C. The report will get duplicated so the analyst can then run one manually.
D. The report still generates on the schedule initially configured.
The graph below shows a time series of a value. A rule has been created which will trigger at the indicated point.
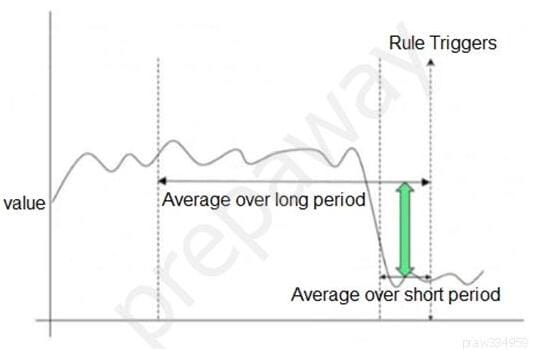
Which type of QRadar rule has been used?
A. Common Rule
B. Threshold Rule
C. Behavioral Rule
D. Anomaly Rule
While creating a new custom property, which is a valid property type selection?
A. Flow Based
B. Event Based
C. AQL Based
D. Regular Expressions Based
What could be a possible reason that events are routed directly to storage by the custom rule engine (CRE)?
A. System is under high load
B. A rule is processing 20,000 EPS
C. Event normalization issue
D. Event Parsing issue
Where can an analyst working with Offenses add a regular expression test into an existing rule?
A. Left
B. Top
C. Bottom
D. Right
An analyst aims to improve the detection capabilities on all the Offense rules. QRadar SIEM has a tool that allows the analyst to update all the Building Blocks related to Host and Port Definition in a single page.
How is this accomplished?
A. Admin –andgt; Reference Set management
B. Assets –andgt; Asset Profiles
C. Assets –andgt; Server Discovery
D. Admin –andgt; Asset Profile Configuration
What information is included in flow details but is not in event details?
A. Log source information
B. Number of bytes and packets transferred
C. Network summary information
D. Magnitude information
From which tab in QRadar SIEM can an analyst search vulnerability data and remediate vulnerabilities?
A. Log Activity
B. Dashboard
C. Assets
D. Admin
What is the difference between a Quick Search and an Advanced Search?
A. An Advanced Search uses a saved search, while a Quick Search uses a query language.
B. A Quick Search displays results by column, while an Advanced Search displays results by Category.
C. A Quick Search uses a saved search, while an Advanced Search requires a query language.
D. An Advanced Search displays results by Category, while a Quick Search displays results by column.
Which QRadar component stored Offenses?
A. Console
B. Data Node
C. Event Processor
D. Event Collector
What does the Assets tab provide?
A unified view of the information that is known about:
A. network devices.
B. triggered Offenses.
C. log sources.
D. events and flows.
Which are the supported protocol configurations for Check Point integration with QRadar? (Choose two.)
A. CHECKPOINT REST API
B. SYSLOG
C. JDBC
D. SFTP
E. OPSEC/LEA
What is the procedure to re-open a closed Offense?
A. A closed Offense cannot be re-opened.
B. Wait for new events/flows that will re-open the closed Offense.
C. Activate the Offense in the action/re-open drop down menu of the Offense tab.
D. Activate the Offense in action/re-open drop down menu in the Admin tab.
