ISSMP Online Practice Questions and Answers
SIMULATION Fill in the blank with an appropriate phrase.___________ is the process of using a strategy and plan of what patches should be applied to which systems at a specified time. Correct
SIMULATION
Fill in the blank with an appropriate phrase.______________ is used to provide security mechanisms for the storage, processing, and transfer of data.
Which of the following statements reflect the 'Code of Ethics Preamble' in the '(ISC)2 Code of Ethics'? Each correct answer represents a complete solution. Choose all that apply.
A. Strict adherence to this Code is a condition of certification.
B. Safety of the commonwealth, duty to our principals, and to each other requires that we adhere, and be seen to adhere, to the highest ethical standards of behavior.
C. Advance and protect the profession.
D. Provide diligent and competent service to principals.
You work as a Product manager for Marioiss Inc. You have been tasked to start a project for securing the network of your company. You want to employ configuration management to efficiently manage the procedures of the project. What will be the benefits of employing configuration management for completing this project? Each correct answer represents a complete solution. Choose all that apply.
A. It provides object, orient, decide and act strategy.
B. It provides a live documentation of the project.
C. It provides the risk analysis of project configurations.
D. It provides the versions for network devices.
Which of the following backup sites takes the longest recovery time?
A. Cold site
B. Hot site
C. Warm site
D. Mobile backup site
Which of the following are the responsibilities of a custodian with regard to data in an information classification program? Each correct answer represents a complete solution. Choose three.
A. Determining what level of classification the information requires
B. Running regular backups and routinely testing the validity of the backup data
C. Controlling access, adding and removing privileges for individual users
D. Performing data restoration from the backups when necessary
DIACAP applies to the acquisition, operation, and sustainment of any DoD system that collects, stores, transmits, or processes unclassified or classified information since December 1997. What phases are identified by DIACAP? Each correct answer represents a complete solution. Choose all that apply.
A. System Definition
B. Accreditation
C. Verification
D. Re-Accreditation
E. Validation
F. Identification
Which of the following governance bodies provides management, operational and technical controls to satisfy security requirements?
A. Senior Management
B. Business Unit Manager
C. Information Security Steering Committee
D. Chief Information Security Officer
In which of the following mechanisms does an authority, within limitations, specify what objects can be accessed by a subject?
A. Role-Based Access Control
B. Discretionary Access Control
C. Task-based Access Control
D. Mandatory Access Control
Which of the following are the ways of sending secure e-mail messages over the Internet? Each correct answer represents a complete solution. Choose two.
A. TLS
B. PGP
C. S/MIME
D. IPSec
You are the project manager of the GHE Project. You have identified the following risks with the characteristics as shown in the following figure:
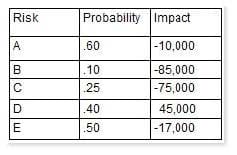
How much capital should the project set aside for the risk contingency reserve?
A. $142,000
B. $232,000
C. $41,750
D. $23,750
Which of the following security controls will you use for the deployment phase of the SDLC to build secure software? Each correct answer represents a complete solution. Choose all that apply.
A. Vulnerability Assessment and Penetration Testing
B. Security Certification and Accreditation (CandA)
C. Change and Configuration Control
D. Risk Adjustments
What is a stakeholder analysis chart?
A. It is a matrix that documents stakeholders' threats, perceived threats, and communication needs.
B. It is a matrix that identifies all of the stakeholders and to whom they must report to.
C. It is a matrix that documents the stakeholders' requirements, when the requirements were created, and when the fulfillment of the requirements took place.
D. It is a matrix that identifies who must communicate with whom.
Which of the following response teams aims to foster cooperation and coordination in incident prevention, to prompt rapid reaction to incidents, and to promote information sharing among members and the community at large?
A. CSIRT
B. CERT
C. FIRST
D. FedCIRC
Which of the following issues are addressed by the change control phase in the maintenance phase of the life cycle models? Each correct answer represents a complete solution. Choose all that apply.
A. Performing quality control
B. Recreating and analyzing the problem
C. Developing the changes and corresponding tests
D. Establishing the priorities of requests
