GSNA Online Practice Questions and Answers
DRAG DROP
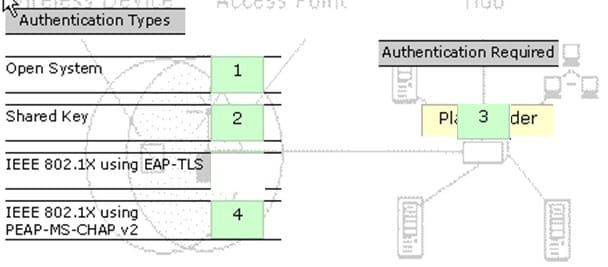
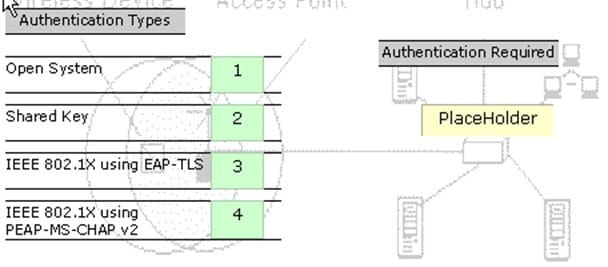
You work as a Network Administrator for Tech Perfect Inc. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single forest single domain network. The company has recently provided laptops to its sales team members. You have configured access points in the network to enable a wireless network. The company's security policy states that all users using laptops must use smart cards for authentication. Select and place the authentication method you are required to configure to implement the security policy of the company.
Select and Place:
Which of the following tools works both as an encryption-cracking tool and as a keylogger?
A. Magic Lantern
B. KeyGhost Keylogger
C. Alchemy Remote Executor
D. SocketShield
You work as a Network Administrator for XYZ CORP. The company has a TCP/IP-based network environment. The network contains Cisco switches and a Cisco router.
You run the following command for a router interface:
show interface serial0
You get the following output:
Serial0 is administratively down, line protocol is down
What will be your conclusion after viewing this output?
A. There is a physical problem either with the interface or the cable attached to it.
B. The router has no power.
C. There is a problem related to encapsulation.
D. The interface is shut down.
Which of the following terms related to risk management represents the estimated frequency at which a threat is expected to occur?
A. Single Loss Expectancy (SLE)
B. Annualized Rate of Occurrence (ARO)
C. Exposure Factor (EF)
D. Safeguard
You work as the Project Engineer for XYZ CORP. The company has a Unix-based network. Your office consists of one server, seventy client computers, and one print device. You raise a request for printing a confidential page. After 30 minutes, you find that your print request job is not processed and is at the seventh position in the printer queue. You analyze that it shall take another one hour to print. You decide to remove your job from the printer queue and get your page printed outside the office.
Which of the following Unix commands can you use to remove your job from the printer queue?
A. tunelp B. pr
C. lprm
D. gs
eBox Platform is an open source unified network server (or a Unified Network Platform) for SMEs. In which of the following forms can eBox Platform be used?
A. Unified Communications Server
B. Network Infrastructure Manager
C. Gateway
D. Sandbox
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to fix partitions on a hard drive.
Which of the following Unix commands can you use to accomplish the task?
A. fdformat
B. exportfs
C. fsck
D. fdisk
Mark works as a Web Developer for XYZ CORP. He is developing a Web site for the company. He wants to use frames in the Web site.
Which of the following is an HTML tag used to create frames?
A.
B.
C.
D.
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. He has recently backed up his entire Linux hard drive into the my_backup.tgz file. The size of the my_backup.tgz file is 800MB. Now, he wants to break this file into two files in which the size of the first file named my_backup.tgz.aa should be 600MB and that of the second file named my_backup.tgz.ab should be 200MB.
Which of the following commands will John use to accomplish his task?
A. split --verbose -b 200m my_backup.tgz my_backup.tgz
B. split --verbose -b 200m my_backup.tgz my_backup.tgz
C. split --verbose -b 600m my_backup.tgz my_backup.tgz
D. split --verbose -b 600m my_backup.tgz my_backup.tgz
Which of the following statements about URL rewriting are true?
A. If cookies are supported by the browser, URL rewriting will return the URL unchanged.
B. The request.encodeRedirectURL() method is used to add a session id info to the URL and send the request to another URL.
C. The request.encodeURL() method is used to add a session id info to the URL.
D. URL rewriting is used in cases where cookies are not supported by the browser.
You work as a Network Administrator for XYZ CORP. The company has a TCP/IP-based network environment. The network contains Cisco switches and a Cisco router. A user is unable to access the Internet from Host B. You also verify that
Host B is not able to connect to other resources on the network.
The IP configuration of Host B is shown below:
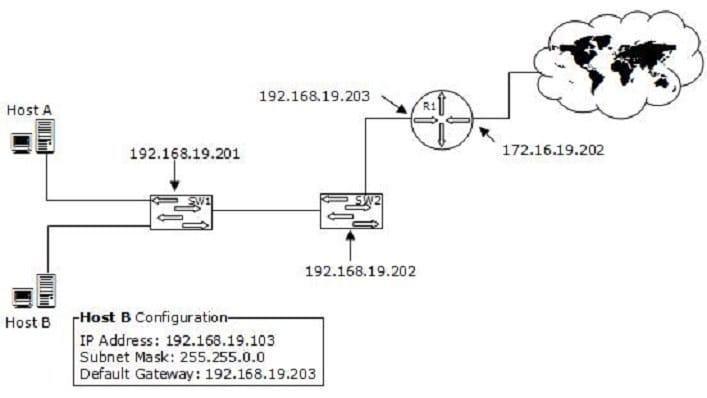
Which of the following is the most likely cause of the issue?
A. An incorrect subnet mask is configured on Host B.
B. The IP address of Host B is not from the correct IP address range of the network.
C. There is an IP address conflict on the network.
D. An incorrect default gateway is configured on Host B.
Which of the following tools can be used to perform ICMP tunneling? (Choose two)
A. Itunnel
B. Ptunnel
C. WinTunnel
D. Ethereal
You are responsible for security at a company that uses a lot of Web applications. You are most concerned about flaws in those applications allowing some attacker to get into your network. What method would be best for finding such flaws?
A. Manual penetration testing
B. Automated penetration testing
C. Vulnerability scanning
D. Code review
Which of the following is an example of penetration testing?
A. Configuring firewall to block unauthorized traffic
B. Implementing HIDS on a computer
C. Simulating an actual attack on a network
D. Implementing NIDS on a network
One of the sales people in your company complains that sometimes he gets a lot of unsolicited messages on his PD A. After asking a few questions, you determine that the issue only occurs in crowded areas like airports. What is the most likely problem?
A. Spam
B. Blue snarfing
C. A virus
D. Blue jacking