GSLC Online Practice Questions and Answers
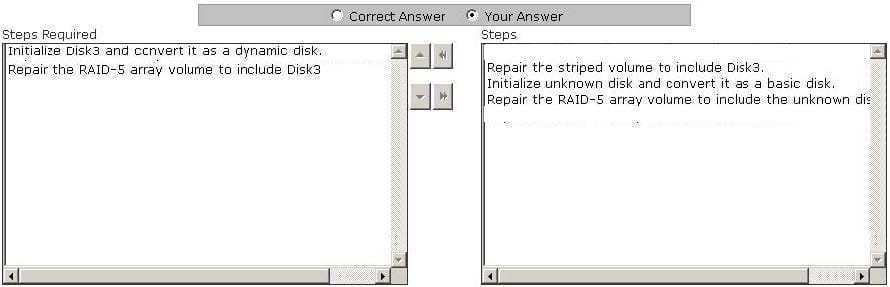
Mark works as a Network Administrator for NetTech Inc. The company has a Windows 2003 single domain-based Active Directory network. The network has five Windows 2003 member servers and 200 Windows XP Professional client computers. One of the member servers named FSERV works as a file server. A three disk RAID-5 array that is used for data storage is configured on FSERV. One morning, during a routine checkup Mark notices that one of the disks of the RAID-5 array has failed. Mark replaces the failed disk with a new one. He restarts the server, runs the Disk Management utility. The status of the RAID-5 array disks shows Disk3 as not initialized and its status as unknown. The array also lists a missing offline dynamic disk. Mark wants to restore the fault tolerant RAID-5 array volume. Choose the required steps that Mark has to take to accomplish the task and arrange them in the correct order.
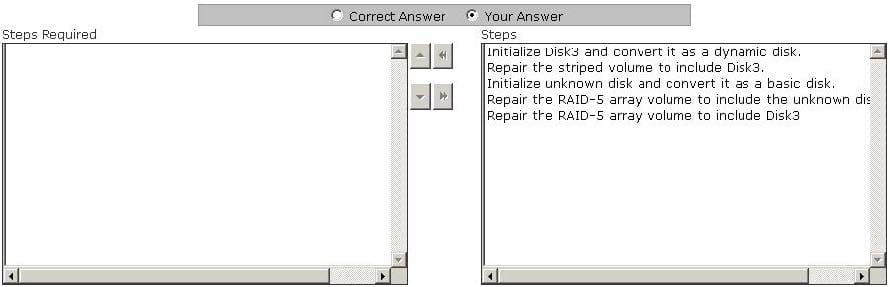
Select and Place:

Which of the following provides security by implementing authentication and encryption on Wireless LAN (WLAN)?
A. WEP
B. WAP
C. L2TP
D. IPSec
You are the project manager for your organization and are trying to determine which vendor your organization will use. You have determined that any vendor that would like to bid on your project work will need to have a Microsoft Certified System Engineer on staff, have eight years of Cisco experience, and have at least two references from similar projects. What have you created in this scenario?
A. Screening system for the vendors
B. Weighting system for the vendors
C. Preferred vendors list
D. Bidders conference
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He wants to use Kismet as a wireless sniffer to sniff the We-are-secure network. Which of the following IEEE-based traffic can be sniffed with Kismet? Each correct answer represents a complete solution. Choose all that apply.
A. 802.11g
B. 802.11a
C. 802.11b
D. 802.11n
Which of the following is used to communicate with an authentication server commonly used in UNIX networks?
A. MS-CHAP
B. IPX/SPX
C. SMTP
D. TACACS
Joseph works as a Network Administrator for WebTech Inc. He has to set up a centralized area on the network so that each employee can share resources and documents with one another. Which of the following will he configure to accomplish the task?
A. VPN
B. Extranet
C. Intranet
D. WEP
Which of the following is a method of defeating a cryptographic scheme by trying a large number of possibilities?
A. Brute force
B. Zero-day
C. FMS
D. IP spoofing
You work as a Network Administrator in a company. The NIDS is implemented on the network. You want to monitor network traffic. Which of the following modes will you configure on the network interface card to accomplish the task?
A. Full Duplex
B. Audit mode
C. Half duplex
D. Promiscuous
Which of the following viruses masks itself from applications or utilities to hide itself by detection of anti-virus software?
A. Macro virus
B. Stealth virus
C. E-mail virus
D. Polymorphic virus
John works as a network security officer in Gentech Inc. The company uses a TCP/IP network. While working on the network, a problem occurs related to the DNS resolution. Which of the following utilities can he use to diagnose the problem?
A. IPConfig
B. Ping
C. Tracert
D. nslookup
Roberta is the project manager of the KJL Project for her company. She is creating a chart that will help categorize the problems discovered during the quality control inspection process. She wants to create a chart where she can categorize the number of instances of problems and rank the problems based on frequency. Which chart should Roberta create?
A. Pareto Chart
B. Scatter diagram
C. Fishbone diagram
D. Control chart
You are the project manager of the NJJ project. Your enterprise environmental factors require that you establish certain risk management rules regarding low risks within your project. What is the best policy for risks with low probability and low impact in the project management?
A. These risks should be placed in the risk register.
B. These risks should be identified, but dismissed.
C. These risks should be accepted.
D. These risks should be placed on a watchlist for future monitoring.
The 3-way handshake method is used by the TCP protocol to establish a connection between a client and the server. It involves three steps:
1.
In the first step, a SYN message is sent from a client to the server.
2.
In the second step, a SYN/ACK message is sent from the server to the client.
3.
In the third step, an ACK (usually called SYN-ACK-ACK) message is sent from the client to the server.
At this point, both the client and the server have received acknowledgements of the TCP connection. If the Initial Sequence Numbers of the client and server were 241713111 and 241824111 respectively at the time when the client was
sending the SYN message in the first step of the TCP 3-way handshake method, what will be the value of the acknowledgement number field of the server's packet when the server was sending the SYN/ACK message to the client in the
second step of the TCP 3-way handshake method?
A. 241824111
B. 241713112
C. 241824112
D. 241713111
Mark works as a Network Administrator for Infonet Inc. The company has a Windows 2003 domainbased network. The network contains five Windows 2003 member servers and 300 Windows XP Professional client computers. Mark is setting up a wireless network for the company. He is planning to implement 802.1x authentication for this new wireless network. Mark is not planning to use a public key infrastructure (PKI) and certificates for authentication. Mark also wants an encrypted authentication channel and a fast reconnect using cached session keys. Which of the following authentication methods will he use to accomplish the task?
A. Protected EAP (PEAP)
B. EAP-Transport Layer Security (EAP-TLS)
C. Shared Key authentication
D. Digest authentication
Which of the following activities result in change requests? Each correct answer represents a complete solution. Choose all that apply.
A. Preventive actions
B. Inspection
C. Defect repair
D. Corrective actions