C_AUDSEC_731 Online Practice Questions and Answers
Which the following tables are used to assign authorization groups to tables and views? Note: There are 2 correct answers to this question.
A. V_DDART
B. V_DDAT_54
C. V_BRG
D. V_BRG_54
Which of the following user types is used to set up Central User Administration (CUA)?
A. Reference (L)
B. Dialog (A)
C. Service (S)
D. System (B)
You want to administer the following clients from a master client:
3 clients of a development system 2 clients of a test system 2 clients of a production system
How many Remote Function Call (RFC) connections are required in Central User Administration (CUA)?
A. 15
B. 14
C. 8
D. 10
You have to analyze risk and perform remediation to enable end-to-end compliance.
What is the correct sequence of steps?
A. 1. Identify and select risks to manage.
2.
Build and maintain rules.
3.
Detect authorization risk.
4.
Test and report the risk.
5.
Remediate and mitigate risk.
6.
Prevent the risk.
B. 1. Identify and select risks to manage.
2.
Build and maintain rules.
3.
Remediate and mitigate risk.
4.
Test and report the risk.
5.
Detect authorization risk.
6.
Prevent the risk.
C. 1. Identify and select risks to manage.
2.
Build and maintain rules.
3.
Detect authorization risk.
4.
Remediate and mitigate risk.
5.
Test and report the risk.
6.
Prevent the risk.
D. 1. Identify and select risks to manage.
2.
Build and maintain rules.
3.
Remediate and mitigate risk.
4.
Detect authorization risk.
5.
Test and report the risk.
6.
Prevent the risk.
You have to maintain authorizations for a new role in the Profile Generator (transaction PFCG).
What does the yellow triangle indicate (see attached screenshot)?
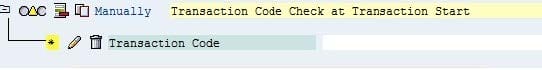
A. You must not give full authorization in this area.
B. The profile for the role has not been generated yet.
C. The maintenance of the authorizations is not done yet; additional work is needed.
D. You do not have the necessary authorization to maintain the authorizations below this level.
Which of following can you modify in basic maintenance of the Profile Generator (PFCG)?
A. Users and organizational management.
B. Profiles and authorization
C. Profiles and workflow
D. Users and workflow
Which of the following is a characteristic of composite roles?
A. Users assigned to composite roles have their own authorization data.
B. They can be assigned to other composite roles.
C. They have their own authorization data.
D. Users assigned to composite roles are automatically assigned to the elementary roles.
You have made changes to tables USOBX_C and USOBT_C. You want to transport these tables from the development environment to the testing environment.
Which transaction do you use to create this transport?
A. Maintain table (SM30)
B. User maintenance (SU01)
C. Profile generator: upgrade and first installation (SU25)
D. User information system (SUIM)
In which table can you find a list of invalid passwords?
A. USR05
B. USR40
C. USR22
D. USR01
How do you delete an existing role in all three SAP systems: development, test, and production?
A. Configure Central User Administration (CUA) to delete the role across the three systems.
B. Log on to the development system. Delete the role across the three systems with transaction SU10.
C. Delete the role in the development system. Create transports without this role. Release the transport to test and production.
D. Enter the role into a transport. Delete the role in the development system. Release the transport to test and production.
Which of the following transactions allows Security Optimization Self Service to add customized authorization checks?
A. ST13
B. ST11
C. ST14
D. ST01
Which of the following authorization objects do users need before they can add external commands, using transaction SM69, to a background job?
A. S_CTS_ADMI
B. S_ADMI_FCD
C. S_RZL_ADM
D. S_LOG_COM
Which of the following can the security audit log record? Note: There are 3 correct answers to this question.
A. Remote Function Calls (RFCs) to function modules
B. User license type usages
C. System performance statistics
D. Changes to user master records
E. Successful and unsuccessful transaction starts
A security manager is asked to gather the average dialog response time over the last 30 minutes. Which of the following transactions can list this information?
A. RZ03
B. RZ10
C. RZ01
D. RZ20
You have to assign multiple roles to multiple users. Which transaction allows you to do this efficiently?
A. SU03
B. SU01
C. SU10
D. SU02
