CS0-002 Online Practice Questions and Answers
A cyber-incident response analyst is investigating a suspected cryptocurrency miner on a company's server. Which of the following is the FIRST step the analyst should take?
A. Create a full disk image of the server's hard drive to look for the file containing the malware.
B. Run a manual antivirus scan on the machine to look for known malicious software.
C. Take a memory snapshot of the machine to capture volatile information stored in memory.
D. Start packet capturing to look for traffic that could be indicative of command and control from the miner.
An information security analyst is reviewing backup data sets as part of a project focused on eliminating archival data sets. Which of the following should be considered FIRST prior to disposing of the electronic data?
A. Sanitization policy
B. Data sovereignty
C. Encryption policy
D. Retention standards
An organization that handles sensitive financial information wants to perform tokenization of data to enable the execution of recurring transactions. The organization is most interested m a secure, built- in device to support its solution. Which of the following would MOST likely be required to perform the desired function?
A. TPM
B. eFuse
C. FPGA
D. HSM
E. UEFI
A code review reveals a web application is using lime-based cookies for session management. This is a security concern because lime-based cookies are easy to:
A. parameterize.
B. decode.
C. guess.
D. decrypt.
Which of the following describes the difference between intentional and unintentional insider threats'?
A. Their access levels will be different
B. The risk factor will be the same
C. Their behavior will be different
D. The rate of occurrence will be the same
A development team has asked users to conduct testing to ensure an application meets the needs of the business. Which of the following types of testing docs This describe?
A. Acceptance testing
B. Stress testing
C. Regression testing
D. Penetration testing
As part of an Intelligence feed, a security analyst receives a report from a third-party trusted source. Within the report are several detrains and reputational information that suggest the company's employees may be targeted for a phishing campaign. Which of the following configuration changes would be the MOST appropriate for Mergence gathering?
A. Update the whitelist.
B. Develop a malware signature.
C. Sinkhole the domains
D. Update the Blacklist
As part of the SDLC, software developers are testing the security of a new web application by inputting large amounts of random data. Which of the following types of testing is being performed?
A. Fuzzing
B. Regression testing
C. Stress testing
D. Input validation
While preparing for a third-party audit, the vice president of risk management and the vice president of information technology have stipulated that the vendor may not use offensive software during the audit. This is an example of:
A. organizational control.
B. service-level agreement.
C. rules of engagement.
D. risk appetite
Which of the following has the GREATEST impact to the data retention policies of an organization?
A. The CIA classification matrix assigned to each piece of data
B. The level of sensitivity of the data established by the data owner
C. The regulatory requirements concerning the data set
D. The technical constraints of the technology used to store the data
The development team currently consists of three developers who each specialize in a specific programming language:
Developer 1 ?C++/C# Developer 2 ?Python Developer 3 ?Assembly
Which of the following SDLC best practices would be challenging to implement with the current available staff?
A. Fuzzing
B. Peer review
C. Regression testing
D. Stress testing
While reviewing web server logs, a security analyst notices the following code:
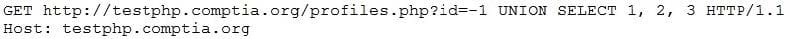
Which of the following would prevent this code from performing malicious actions?
A. Performing web application penetration testing
B. Requiring the application to use input validation
C. Disabling the use of HTTP and requiring the use of HTTPS
D. Installing a network firewall in front of the application
The board of directors made the decision to adopt a cloud-first strategy. The current security infrastructure was designed for on-premises implementation. A critical application that is subject to the Federal Information Security Management Act (FISMA) of 2002 compliance has been identified as a candidate for a hybrid cloud deployment model. Which of the following should be conducted FIRST?
A. Develop a request for proposal.
B. Perform a risk assessment.
C. Review current security controls.
D. Review the SLA for FISMA compliance.
Joe, an analyst, has received notice that a vendor who is coming in for a presentation will require access to a server outside the network. Currently, users are only able to access remote sites through a VPN connection. Which of the following should Joe use to BEST accommodate the vendor?
A. Allow incoming IPSec traffic into the vendor's IP address.
B. Set up a VPN account for the vendor, allowing access to the remote site.
C. Turn off the firewall while the vendor is in the office, allowing access to the remote site.
D. Write a firewall rule to allow the vendor to have access to the remote site.
A small marketing firm uses many SaaS applications that hold sensitive information. The firm has discovered terminated employees are retaining access to systems for many weeks after their end date. Which of the following would BEST resolve the issue of lingering access?
A. Perform weekly manual reviews on system access to uncover any issues.
B. Set up a privileged access management tool that can fully manage privileged account access.
C. Implement MFA on cloud-based systems.
D. Configure federated authentication with SSO on cloud provider systems.
