C2150-400 Online Practice Questions and Answers
Which two actions can be selected from the license drop-down in the system and license management screen when working with a new license? (Choose two.)
A. Apply license
B. Upload license
C. Allocate license to system
D. Allocate system to license
E. Register system to license
What two are valid actions that a user can perform when monitoring offenses? (Choose two.)
A. Import offenses
B. Backup offenses
C. Restore offenses
D. Send email notifications
E. Hide or close an offense from any offense list
Which NetFlow versions does QRadar SIEM support?
A. 1, 2, 3, and 4
B. 1, 4, 7, and 9
C. 1, 3, 5, and 9
D. 1, 5, 7, and 9
From the given event payload format:
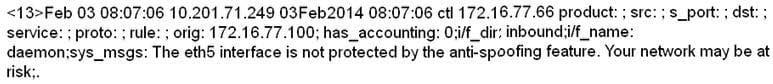
You are tasked with creating a Reference Set of the second IPs in the payload.
What needs to be done to complete this task?
A. Create a Custom Event Property to parse the second IP in the payload. From the Log Source config for the above event, choose "add to reference set" and select your reference set.
B. From the Reference Set Management screen, select "create reference set from Log Source Event". Pick the Log Source from the drop down. Pick the Event Name from the drop down.
C. From the Reference Set Management screen, select "create reference set from Log Source Event". Pick the Log Source from the drop down. Pick the Custom Event Property from the drop down.
D. Create a Custom Event Property to parse the second IP in the payload. Create a rule that tests for events from the Log Source that is collecting the above event, and for Rule Response add the Custom
Event Property to the Reference Set.
Which IP address of a NATed server is used to access the server from outside the network?
A. Public IP address
B. Private IP address
C. Cluster IP address
D. Secondary IP address
Where does the information about total number of Assets and Vulnerability processed appear?
A. Asset table in Assets tab
B. VA Scanner Configuration screen
C. Vulnerabilities Tab > Scan Result
D. Mouse Ober popup on Schedule Scan Status field
Which serial option needs to be set in the syslinux configuration file to reinstall a malfunctioning appliance via serial port from an USB flash-drive?
A. Default serial
B. Serial port redirect
C. Serial install option
D. Serial console redirect
Which two primary data sources send updates to the Asset profiler? (Choose two.)
A. Source IP
B. Source Port
C. Scan Result
D. Destination IP
E. Identity Events
How do you view an offense that is associated with an event from the Log Activity tab?
A. Double click the event
B. Click the Offense icon next to the event
C. Right click the event, select View Offenses
D. Select the event, and select Offenses from the View list box
Which network monitoring port does Juniper Jflow require to be configured in QRadar?
A. Port 80
B. Port 443
C. Port 1080
D. Port 2055
What is QRadar QFlow Collector combined with QRadar SIEM designed to do?
A. Collect Netflow records
B. Layer 7 application visibility
C. Receive Syslog messages
D. Ensure secure message collection
Who can view all offenses?
A. All users
B. Admin user
C. User who has access to All Log Sources and All Networks
D. Restricted User who has access to a Specific Log Source and Network
Given the network IP range of 192.168.160.1 to 192.168.160.127, what format would this be entered into a network hierarchy object?
A. 192.168.160.128/24
B. 192.168.160.0/24
C. 192.168.160.0/23
D. 192.168.160.0/25
A customer wants to view Log Sources based on functionality on QRadar console. The customer wants to categorize its Log Sources into multiple groups, which allows the customer to efficiently view and track its log sources.
What is the maximum number of log sources a log source group can display on the QRadar console?
A. 100
B. 500
C. 750
D. 1000
Which attribute is valid when defining the user roles to provide the necessary access?
A. Assets: Server Discovery
B. Offenses: View Custom Rules
C. Offenses: Maintain Custom Rules
D. Network Activity: User Defined Flow Properties
