A2090-610 Online Practice Questions and Answers
What functionality allows users to perform a UNION operation between a DB2 table and an Oracle view?
A. Oracle connect
B. Trusted context
C. Oracle federation
D. Distributed request
You have a business need to query DB2 10 and DB2 9 databases and you want to write an application that can run on most platforms unchanged. Which interface would you use to achieve your goal?
A. CLI
B. XML
C. JDBC
D. RUBY
Which tool allows users to connect to a DB2 database using a wizard?
A. Control Center
B. IBM Data Studio
C. Universal Connection Expert
D. DB2 Connection Pool Manager
What is the primary function of an Online Transaction Processing (OLTP) workload?
A. To combine data from multiple sources.
B. To discover hidden relationships in data.
C. To analyze large amounts of data to find patterns.
D. To make changes to a small number of records within a single transaction.
Which statement will prevent concurrent application processes from performing anything other than read-only operations against a table named TAB1?
A. LOCK TABLE tab1 IN READ MODE
B. LOCK TABLE tab1 IN SHARE MODE
C. LOCK TABLE tab1 IN EXCLUSIVE MODE
D. LOCK TABLE tab1 IN READ-ONLY MODE
What is the act of exchanging one lock an application holds on a resource for a more restrictive lock on the same resource known as?
A. Lock escalation
B. Lock substitution
C. Lock switch/exchange
D. Lock conversion/promotion
If the following result set is desired:
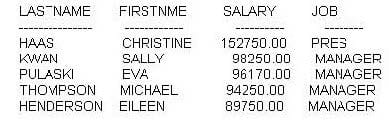
Which SQL statement must be executed?
A. SELECT lastname, firstnme, salary, jobFROM employeeORDER BY 3FETCH FIRST 5 ROWS ONLY
B. SELECT lastname, firstnme, salary, jobFROM employeeORDER BY 3 DESCFETCH FIRST 5 ROWS ONLY
C. SELECT lastname, firstnme, salary, jobFROM employeeORDER BY 3FETCH FIRST 5 ROWS
D. SELECT lastname, firstnme, salary, jobFROM employeeORDER BY 3 DESCFETCH FIRST 5 ROWS
Which two statements are true about foreign key constraints? (Choose two.)
A. The foreign key constraint columns must be supported by an index.
B. The foreign key constraint columns must be defined as NOT NULL.
C. The number and data types of foreign key constraint columns must match the parent key.
D. The columns of one foreign key constraint cannot be used in another foreign key constraint.
E. To define a foreign key constraint there must be an associated primary key or unique key in the same or different table.
Which type of constraint can be used to ensure that an INTEGER column in a table will never be assigned more than one record that contains a NULL value?
A. Unique constraint
B. Primary key constraint
C. Informational constraint
D. Column default constraint
What is used in conjunction with a foreign key to define a relationship between two tables?
A. Primary key
B. Partitioning key
C. Check constraint
D. Unique constraint
Which type of table should you use if you want to define specific time periods when data is valid?
A. Materialized query table
B. System-period temporal table
C. Declared global temporary table
D. Application-period temporal table
Which statement about bitemporal tables is valid?
A. Bitemporal tables are system tables and can only be queried by the schema owner.
B. Creating a bitemporal table is similar to creating a regular table except users must specify a system time period column.
C. When data in a bitemporal table is updated, a row is added to it's associated history table.
D. Querying a bitemporal table will produce results for a complete timeline; a view must be created to obtain results for a specific time period.
Which DB2 product is NOT suitable for very large data warehouse applications?
A. DB2 for i
B. DB2 for AIX
C. DB2 for z/OS
D. DB2 for Linux
When a user-defined function (UDF) is created and no schema is specified, what schema is used to store the UDF?
A. The SYSIBM schema.
B. The SYSFUN schema.
C. A schema with the name of the UDF.
D. A schema with the userid of the UDF definer.
What isolation level prevents dirty reads, nonrepeatable reads, and phantoms?
A. Read stability (RS)
B. Cursor stability (CS)
C. Repeatable read (RR)
D. Uncommitted read (UR)
