98-367 Online Practice Questions and Answers
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
Hot Area:

For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
Hot Area:

An employee where you work is unable to access the company message board in Internet Explorer. You review her Internet Options dialog box, as shown in the following image:
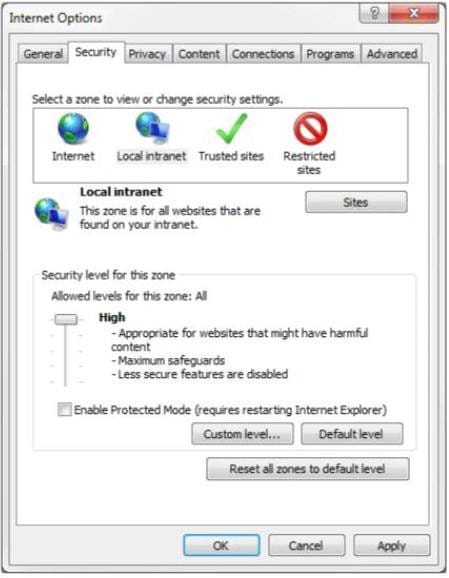
Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.
Hot Area:

To prevent users from copying data to removable media, you should:
A. Lock the computer cases
B. Apply a group policy
C. Disable copy and paste
D. Store media in a locked room
A group of users has access to Folder A and all of its contents. You need to prevent some of the users from accessing a subfolder inside Folder A.
What should you do first?
A. Disable folder sharing
B. Hide the folder
C. Change the owner
D. Block inheritance
You need to limit the programs that can run on client computers to a specific list. Which technology should you implement?
A. Windows Security Center
B. Security Accounts Manager
C. System Configuration Utility
D. AppLocker group policies
Humongous Insurance is an online healthcare insurance company. During an annual security audit a security firm tests the strength of the company's password policy and suggests that Humongous Insurance implement password history policy.
What is the likely reason that the security firm suggests this?
A. Past passwords were easily cracked by the brute force method.
B. Past passwords of users contained dictionary words.
C. Previous password breaches involved use of past passwords.
D. Past passwords lacked complexity and special characters.
To keep third-party content providers from tracking your movements on the web, enable InPrivate Browsing.
Select the correct answer if the underlined text does not make the statement correct. Select "No change is needed'' if the underlined text makes the statement correct.
A. InPrivate Filtering
B. SmartScreen Filter
C. Compatibility Mode
D. No change is needed
You suspect a user's computer is infected by a virus. What should you do first?
A. Restart the computer in safe mode
B. Replace the computer's hard disk drive
C. Disconnect the computer from the network
D. Install antivirus software on the computer
You create a new file in a folder that has inheritance enabled. By default, the new file:
A. Takes the permissions of the parent folder
B. Does not take any permissions
C. Takes the permissions of other folders in the same directory
D. Takes the permissions of other files in the same directory
Windows Server Update Services (WSUS) is a tool that:
A. Updates data stored in Windows servers
B. Manages the services that run on a server
C. Updates licensing for Windows servers
D. Manages updates for Microsoft software
Media Access Control (MAC) filtering enables you to:
A. limit access to a network based on the client computer's network adapter.
B. set access permissions to a shared folder.
C. prevent communications between specific IP addresses.
D. restrict communications to a specific website.
Which of the following are the main features of a key logger? Each correct answer represents a complete solution. Choose all that apply.
A. It can be delivered via FTP or e-mail.
B. It can record all keystrokes.
C. It can capture all screenshots.
D. It can detect viruses on the computer.
Which of the following is method that can be used to identify Internet software in Software Restriction Policies?
A. Restriction rule
B. Identification rule
C. Internet rule
D. Zone rule
What are three ways you can reduce the number of opportunities that attackers have to exploit potential weaknesses or vulnerabilities? (Choose three.)
A. Employ layered defenses
B. Elevate all accounts to administrator accounts
C. Apply the principle of least privilege
D. Employ content filtering for web browsers
E. Restrict access to system services



