5V0-91.20 Online Practice Questions and Answers
An administrator is searching for any child processes of email clients with this query in Carbon Black Enterprise EDR:
parent_name:outlook.exe OR parent_name:thunderbird.exe OR parent_name:eudora.exe The administrator would like to modify this query to only show child processes that do not have a known reputation in the Carbon Black Cloud.
Which search field can be added to the query to show the desired results?
A. process_integrity_level
B. process_reputation
C. process_privileges
D. process_cloud_reputation
An administrator receives an alert with the TTP DATA_TO_ENCRYPTION.
What is known about the alert based on this TTP even if other parts of the alert are unknown?
A. A process attempted to delete encrypted data on the disk.
B. A process attempted to write a file to the disk.
C. A process attempted to modify a monitored file written by the sensor.
D. A process attempted to transfer encrypted data on the disk over the network.
An administrator wants to find instances where the binary Is unsigned. Which term will accomplish this search?
A. NOT process_publisher:FILE_SIGNATURE_STATE_SIGNED
B. NOT process_publisher_state:FILE_SIGNATURE_STATE_SIGNED
C. process_publisher_state:FILE_SIGNATURE_STATE_NOT_SIGNED
D. process_publisher:FILE_SIGNATURE_STATE_NOT_SIGNED
A Carbon Black administrator received an alert for an untrusted hash executing in the environment. Which two information items are found in the alert pane? (Choose two.)
A. Launch Live Query
B. Launch process analysis
C. User quarantine
D. Add hash to banned list
E. IOC short name
An administrator ran the following query.
SELECT name, VERSION, install_location, install_source, publisher, install_date, uninstall_string FROM
programs WHERE publisher = "Microsoft Corporation";
The administrator notices a lot of installed programs are not returned.
How can the administrator alter the query to see all results?
A. Edit the WHERE clause to remove the quotes
B. Remove the WHERE clause
C. Replace the = with LIKE
D. Change the WHERE clause to = "*"
An administrator is troubleshooting App Control agent issues. When navigating to the Computer Details page, the administrator sees the following: What is the status of the WINDOWS-CLIENT agent?
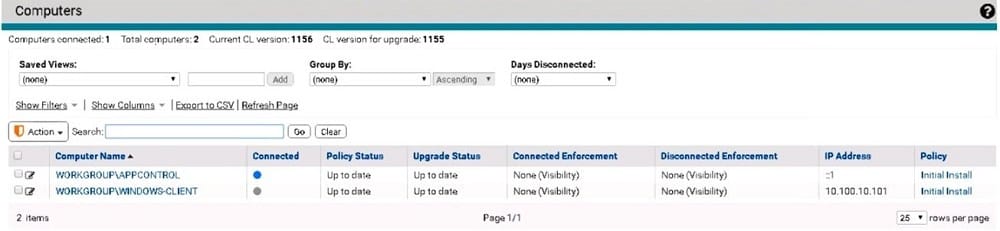
A. Connected and Up to date
B. Disconnected and Up to date
C. Connected but unsupported
D. Connected but health check failed
An Enterprise EDR administrator is reviewing the Investigate page and believes they are receiving false positive hits from specific watchlist.
Which three options reduce future false positive hits from this watchlist? (Choose three.)
A. Disable/remove the IOC associated with the false positives.
B. Disable/remove the report associated with the false positives.
C. Dismiss the watchlist hit.
D. Select edit watchlist and uncheck alert on hits.
E. Modify policy rules to exclude the false positive directory.
F. Disable the watchlist associated with the false positives.
Level 3 service desk personnel have been approved to modify computer enforcement levels by security
governance.
Which set of steps is required to implement this change?
A. Assign permission "Temporary assign computers" to each user.
B. Create new user role, assign permission "Manage computers" to role.
C. Create new user role, map AD group to role, assign permission "Manage computers" to role.
D. Create new user role, map AD group to role, assign permission "Temporary assign computers" to role.
