412-79V8 Online Practice Questions and Answers
The IP protocol was designed for use on a wide variety of transmission links. Although the maximum length of an IP datagram is 64K, most transmission links enforce a smaller maximum packet length limit, called a MTU. The value of the MTU depends on the type of the transmission link. The design of IP accommodates MTU differences by allowing routers to fragment IP datagrams as necessary. The receiving station is responsible for reassembling the fragments back into the original full size IP datagram. IP fragmentation involves breaking a datagram into a number of pieces that can be reassembled later. The IP source, destination, identification, total length, and fragment offset fields in the IP header, are used for IP fragmentation and reassembly.
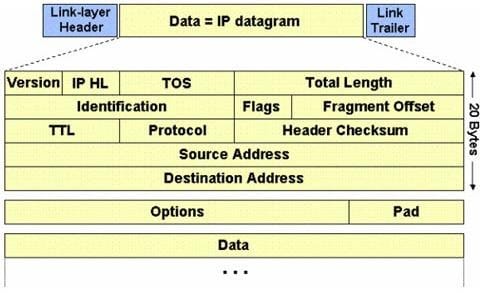
The fragment offset is 13 bits and indicates where a fragment belongs in the original IP datagram. This value is a:
A. Multiple of four bytes
B. Multiple of two bytes
C. Multiple of eight bytes
D. Multiple of six bytes
Which of the following statement holds true for TCP Operation?
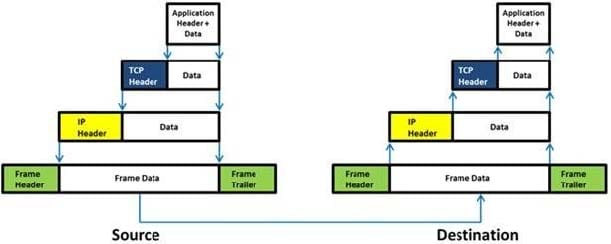
A. Port numbers are used to know which application the receiving host should pass the data to
B. Sequence numbers are used to track the number of packets lost in transmission
C. Flow control shows the trend of a transmitting host overflowing the buffers in the receiving host
D. Data transfer begins even before the connection is established
In a TCP packet filtering firewall, traffic is filtered based on specified session rules, such as when a session is initiated by a recognized computer.

Identify the level up to which the unknown traffic is allowed into the network stack.
A. Level 5 Application
B. Level 2 Data Link
C. Level 4 TCP
D. Level 3 Internet Protocol (IP)
A penetration test consists of three phases: pre-attack phase, attack phase, and post-attack phase.
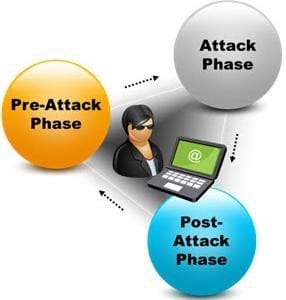
Active reconnaissance which includes activities such as network mapping, web profiling, and perimeter mapping is a part which phase(s)?
A. Post-attack phase
B. Pre-attack phase and attack phase
C. Attack phase
D. Pre-attack phase
Identify the transition mechanism to deploy IPv6 on the IPv4 network from the following diagram.
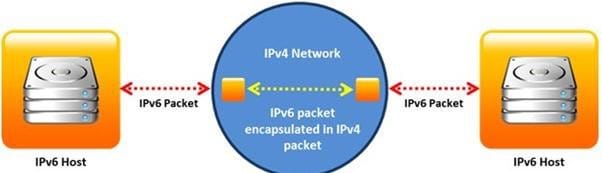
A. Translation
B. Tunneling
C. Dual Stacks
D. Encapsulation
Why is a legal agreement important to have before launching a penetration test?
A. Guarantees your consultant fees
B. Allows you to perform a penetration test without the knowledge and consent of the organization's upper management
C. It establishes the legality of the penetration test by documenting the scope of the project and the consent of the company.
D. It is important to ensure that the target organization has implemented mandatory security policies
In the process of hacking a web application, attackers manipulate the HTTP requests to subvert the application authorization schemes by modifying input fields that relate to the user ID, username, access group, cost, file names, file identifiers, etc. They first access the web application using a low privileged account and then escalate privileges to access protected resources. What attack has been carried out?
A. XPath Injection Attack
B. Authorization Attack
C. Authentication Attack
D. Frame Injection Attack
Which of the following password hashing algorithms is used in the NTLMv2 authentication mechanism?
A. AES
B. DES (ECB mode)
C. MD5
D. RC5
An attacker injects malicious query strings in user input fields to bypass web service authentication mechanisms and to access back-end databases. Which of the following attacks is this?
A. Frame Injection Attack
B. LDAP Injection Attack
C. XPath Injection Attack
D. SOAP Injection Attack
Internet Control Message Protocol (ICMP) messages occur in many situations, such as whenever a datagram cannot reach the destination or the gateway does not have the buffering capacity to forward a datagram. Each ICMP message contains three fields: type, code, and checksum. Different types of Internet Control Message Protocols (ICMPs) are identified by a type and code field.
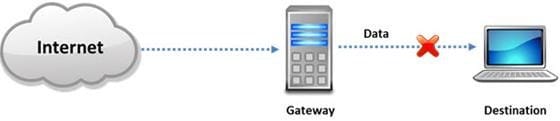
Which of the following ICMP messages will be generated if the destination port is not reachable?
A. ICMP Type 11 code 1
B. ICMP Type 5 code 3
C. ICMP Type 3 code 2
D. ICMP Type 3 code 3
Port numbers are used to keep track of different conversations crossing the network at the same time. Both TCP and UDP use port (socket) numbers to pass information to the upper layers. Port numbers have the assigned ranges. The port numbers above 1024 are considered as which one of the following? (Select all that apply)
A. Well-known port numbers
B. Dynamically assigned port numbers
C. Unregistered port numbers
D. Statically assigned port numbers
Internet Control Message Protocol (ICMP) messages occur in many situations, such as whenever a datagram cannot reach the destination or the gateway does not have the buffering capacity to forward a datagram. Each ICMP message contains three fields: type, code, and checksum. Different types of Internet Control Message Protocols (ICMPs) are identified by a TYPE field. If the destination is not reachable, which one of the following are generated?
A. Type 8 ICMP codes
B. Type 12 ICMP codes
C. Type 3 ICMP codes
D. Type 7 ICMP codes
Nessus can test a server or a network for DoS vulnerabilities. Which one of the following script tries to kill a service?
A. ACT_DENIAL
B. ACT_FLOOD
C. ACT_KILL_HOST
D. ACT_ATTACK
Variables are used to define parameters for detection, specifically those of your local network and/or specific servers or ports for inclusion or exclusion in rules. These are simple substitution variables set with the var keyword. Which one of the following operator is used to define meta- variables?
A. "$"
B. "#"
C. "*"
D. "?"
NTP protocol is used to synchronize the system clocks of computers with a remote time server or time source over a network. Which one of the following ports is used by NTP as its transport layer?
A. TCP port 152
B. UDP port 177
C. UDP port 123
D. TCP port 113
