412-79V10 Online Practice Questions and Answers
Which one of the following tools of trade is an automated, comprehensive penetration testing product for assessing the specific information security threats to an organization?
A. Sunbelt Network Security Inspector (SNSI)
B. CORE Impact
C. Canvas
D. Microsoft Baseline Security Analyzer (MBSA)
How many bits is Source Port Number in TCP Header packet?
A. 48
B. 32
C. 64
D. 16
One of the steps in information gathering is to run searches on a company using complex keywords in Google.
Which search keywords would you use in the Google search engine to find all the PowerPoint presentations containing information about a target company, ROCHESTON?
A. ROCHESTON fileformat:+ppt
B. ROCHESTON ppt:filestring
C. ROCHESTON filetype:ppt
D. ROCHESTON +ppt:filesearch
SQL injection attack consists of insertion or "injection" of either a partial or complete SQL query via the
data input or transmitted from the client (browser) to the web application.
A successful SQL injection attack can:
i)Read sensitive data from the database
iii)Modify database data (insert/update/delete)
iii)Execute administration operations on the database (such as shutdown the DBMS)
iV)Recover the content of a given file existing on the DBMS file system or write files into the file system
v)Issue commands to the operating system
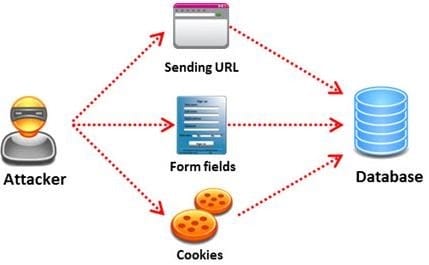
Pen tester needs to perform various tests to detect SQL injection vulnerability. He has to make a list of all input fields whose values could be used in crafting a SQL query, including the hidden fields of POST requests and then test them separately, trying to interfere with the query and to generate an error.
In which of the following tests is the source code of the application tested in a non-runtime environment to detect the SQL injection vulnerabilities?
A. Automated Testing
B. Function Testing
C. Dynamic Testing
D. Static Testing
Which of the following statements is true about Multi-Layer Intrusion Detection Systems (mIDSs)?
A. Decreases consumed employee time and increases system uptime
B. Increases detection and reaction time
C. Increases response time
D. Both a and c
Identify the attack represented in the diagram below:
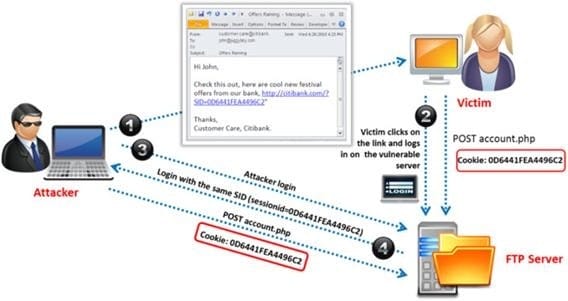
A. Input Validation
B. Session Hijacking
C. SQL Injection
D. Denial-of-Service
Identify the port numbers used by POP3 and POP3S protocols.
A. 113 and 981
B. 111 and 982
C. 110 and 995
D. 109 and 973
A penetration test consists of three phases: pre-attack phase, attack phase, and post- attack phase.
Active reconnaissance which includes activities such as network mapping, web profiling, and perimeter mapping is a part which phase(s)?
A. Post-attack phase
B. Pre-attack phase and attack phase
C. Attack phase
D. Pre-attack phase
Due to illegal inputs, various types of TCP stacks respond in a different manner. Some IDSs do not take into account the TCP protocol's urgency feature, which could allow testers to evade the IDS.
Penetration tester needs to try different combinations of TCP flags (e.g. none, SYN/FIN, SYN/RST, SYN/ FIN/ACK, SYN/RST/ACK, and All Flags) to test the IDS.
Which of the following TCP flag combinations combines the problem of initiation, midstream, and termination flags with the PSH and URG?
A. SYN/RST/ACK
B. SYN/FIN/ACK
C. SYN/FIN
D. All Flags
Why is a legal agreement important to have before launching a penetration test?
A. Guarantees your consultant fees
B. Allows you to perform a penetration test without the knowledge and consent of the organization's upper management
C. It establishes the legality of the penetration test by documenting the scope of the project and the consent of the company.
D. It is important to ensure that the target organization has implemented mandatory security policies
Internet Control Message Protocol (ICMP) messages occur in many situations, such as whenever a datagram cannot reach the destination or the gateway does not have the buffering capacity to forward a datagram. Each ICMP message contains three fields: type, code, and checksum. Different types of Internet Control Message Protocols (ICMPs) are identified by a type and code field.
Which of the following ICMP messages will be generated if the destination port is not reachable?
A. ICMP Type 11 code 1
B. ICMP Type 5 code 3
C. ICMP Type 3 code 2
D. ICMP Type 3 code 3
The framework primarily designed to fulfill a methodical and organized way of addressing five threat classes to network and that can be used to access, plan, manage, and maintain secure computers and communication networks is:
A. Nortells Unified Security Framework
B. The IBM Security Framework
C. Bell Labs Network Security Framework
D. Microsoft Internet Security Framework
Which one of the following tools of trade is a commercial shellcode and payload generator written in Python by Dave Aitel?
A. Microsoft Baseline Security Analyzer (MBSA)
B. CORE Impact
C. Canvas
D. Network Security Analysis Tool (NSAT)
Passwords protect computer resources and files from unauthorized access by malicious users. Using passwords is the most capable and effective way to protect information and to increase the security level of a company.
Password cracking is the process of recovering passwords from data that have been stored in or transmitted by a computer system to gain unauthorized access to a system.
Which of the following password cracking attacks tries every combination of characters until the password is broken?
A. Brute-force attack
B. Rule-based attack
C. Hybrid attack
D. Dictionary attack
Which of the following is the objective of Gramm-Leach-Bliley Act?
A. To ease the transfer of financial information between institutions and banks
B. To protect the confidentiality, integrity, and availability of data
C. To set a new or enhanced standards for all U.S. public company boards, management and public accounting firms
D. To certify the accuracy of the reported financial statement
