400-007 Online Practice Questions and Answers
Which undesired effect of increasing the jitter compensation buffer is true?
A. The overall transport jitter decreases and quality improves.
B. The overall transport jitter increases and quality issues can occur.
C. The overall transport delay increases and quality issues can occur.
D. The overall transport delay decreases and quality improves.
Which two points must network designers consider when designing a new network design or when evaluating an existing network design to help them understand the high-level design direction with regards to the security aspects? (Choose two.)
A. Consider for only complex networks
B. Consider organization's security policy standards
C. Consider for only new network technologies and components
D. Consider for only multi-site networks
E. Consider Business objectives and goals
A healthcare provider discovers that protected health information of patients was altered without patient consent. The healthcare provider is subject to HIPAA compliance and is required to protect PHI data. Which type of security safeguard should be implemented to resolve this issue?
A. technical and physical access control
B. administrative security management processes
C. physical device and media control
D. technical integrity and transmission security
Company XYZ is migrating their existing network to IPv6 and they must plan for Layer 2 and Layer 3 devices Some of the access layer switches do not support IPv6, however, core and distribution switches fully support unicast and multicast routing. The company wants to minimize cost of the migration. Which migration strategy should be used in the design?
A. The access layer switches must support IGMP snooping at a minimum. Any switches that do not support IGM snooping must be replaced.
B. Upgrade the nonsupporting switches Otherwise, it will cause an issue with the migration.
C. Layer 2 switches will not affect the implementation of IPv6. They can be included in the design in their current state.
D. The access layer switches must support DHCPv6. Any switches that do not support DHCPv6 must be replaced.
A customer has a functional requirement that states HR systems within a data center should be segmented from other systems that reside in the same data center and same VLAN. The systems run legacy applications by using hard-coded IP addresses. Which segmentation method is suitable and scalable for the customer?
A. data center perimeter firewalling
B. VACLs on data center switches
C. transparent firewalling
D. routed firewalls
The administrator of a small branch office wants to implement the Layer 2 network without running STP The office has some redundant paths.
Which mechanism can the administrator use to allow redundancy without creating Layer 2 loops?
A. Use double-sided VPC on both switches
B. Use two port channels as Flex links
C. Use fabric path with ECMP
D. Use 802.3ad link bundling.
A European national bank considers migrating its on-premises systems to a private cloud offering in a non-European location to significantly reduce IT costs. What is a primary factor prior to migration?
A. data governance
B. additional latency
C. security
D. cloud connectivity
An enterprise requires MPLS connected branches to access cloud-based Microsoft 365 services over an SD-WAN solution. Internet access Is available only at dual regional hub sites that are connected to the MPLS network. Which connectivity method provides an optimum access method to the cloud-based services If one ISP suffers loss or latency?
A. Cloud onRamp gateway site
B. Cloud onRamp SWG
C. Cloud onRamp
D. Cloud onRamp SaaS
Which two factors must be considered for high availability in campus LAN designs to mitigate concerns about unavailability of network resources? (Choose two.)
A. device resiliency
B. device type
C. network type
D. network resiliency
E. network size
While designing a switched topology, in which two options is UplinkFast recommended? (Choose two )
A. when switches of different spanning-tree types are connected (for example. 802.1d connecting to 802.1w)
B. on distribution layer switches
C. when hello timers are changed to more aggressive values
D. on access layer switches
E. on the core switches
What is a web-based model in which a third-party provider hosts applications that are available to customers over the Internet?
A. PaaS
B. SaaS
C. laaS D. WaaS
Refer to the exhibit.
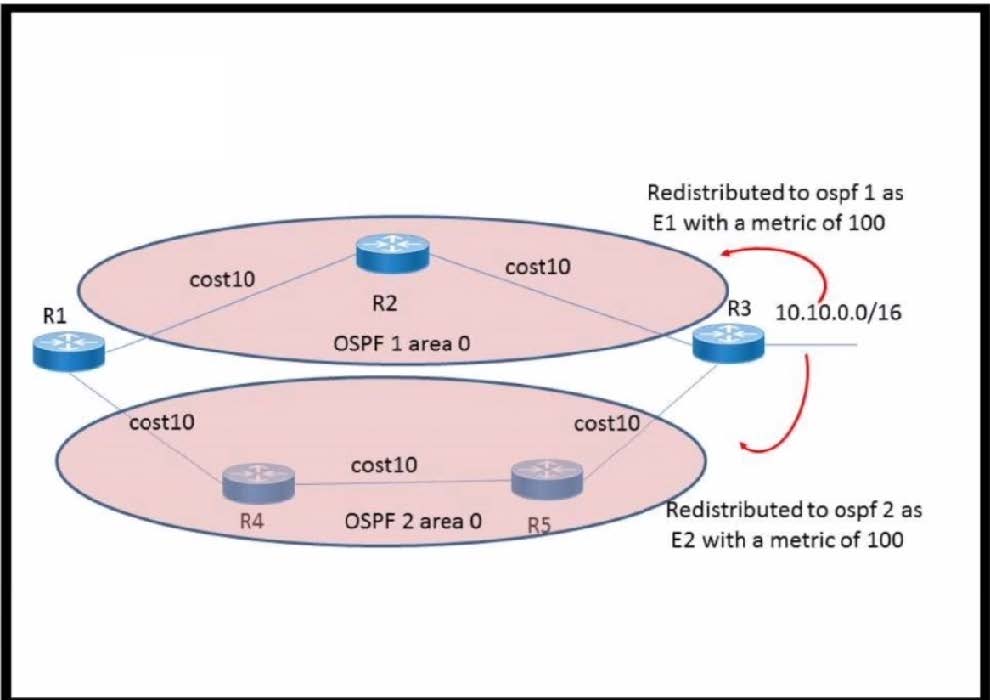
The network 10.10.0 .0/16 has been redistributed to OSPF processes and the best path to the destination from R1 has been chosen as R1-R2-R3 A failure occurred on the link between R2 and R3 and the path was changed to R1-R4-R5-R3. What happens when the link between R2 and R3 is restored?
A. The path R1-R4-R5-R3 continues to be the best path because the metric is better
B. The path reverts back to R1-R2-R3 because the route type is E1
C. The path R1-R4-R5-R3 continues to be the best path because OSPF does not compare the metrics between two domains
D. The path reverts to R1-R2-R3 because this was the previous best path
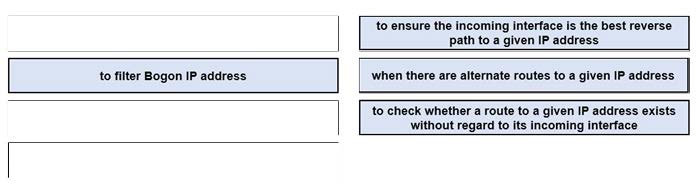
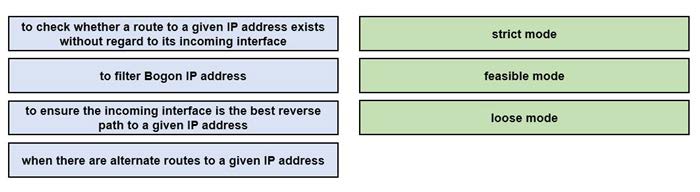
DRAG DROP
Drag and drop the design use cases from the left onto the correct uRPF techniques used to prevent spoofing attacks Not all options are used.
Select and Place:
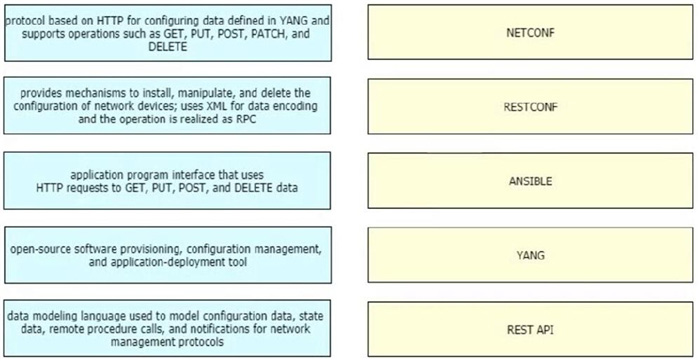
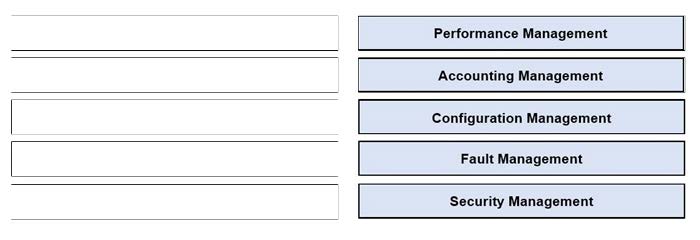
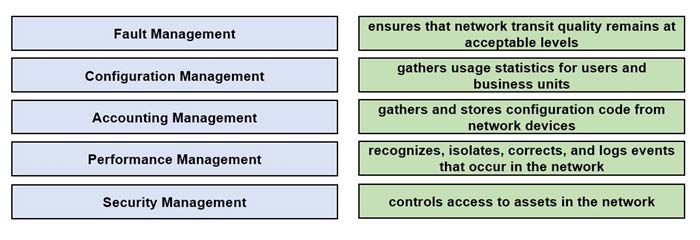
DRAG DROP
Drag and drop the FCAPS network management reference models from the left onto the correct definitions on the right.
Select and Place:
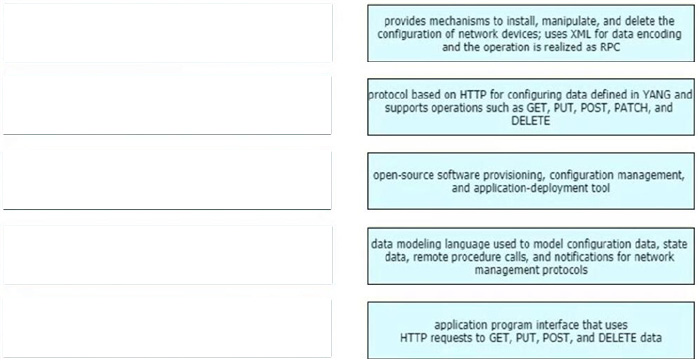
DRAG DROP
Drag and drop the characteristics from the left onto the corresponding network management options on the right.
Select and Place: