350-701 Online Practice Questions and Answers
Which API is used for Content Security?
A. NX-OS API
B. IOS XR API
C. OpenVuln API
D. AsyncOS API
What two mechanisms are used to redirect users to a web portal to authenticate to ISE for guest services? (Choose two)
A. multiple factor auth
B. local web auth
C. single sign-on
D. central web auth
E. TACACS+
In a PaaS model, which layer is the tenant responsible for maintaining and patching?
A. hypervisor
B. virtual machine
C. network
D. application
Which Cisco product provides proactive endpoint protection and allows administrators to centrally manage the deployment?
A. NGFW
B. AMP
C. WSA
D. ESA
What is a commonality between DMVPN and FlexVPN technologies?
A. FlexVPN and DMVPN use IS-IS routing protocol to communicate with spokes
B. FlexVPN and DMVPN use the new key management protocol
C. FlexVPN and DMVPN use the same hashing algorithms
D. IOS routers run the same NHRP code for DMVPN and FlexVPN
Which ID store requires that a shadow user be created on Cisco ISE for the admin login to work?
A. RSA SecureID
B. Internal Database
C. Active Directory
D. LDAP
What is an attribute of the DevSecOps process?
A. mandated security controls and check lists
B. security scanning and theoretical vulnerabilities
C. development security
D. isolated security team
Which industry standard is used to integrate Cisco ISE and pxGrid to each other and with other interoperable security platforms?
A. IEEE
B. IETF
C. NIST
D. ANSI
Which two authentication protocols are supported by the Cisco WSA? (Choose two.)
A. WCCP
B. NTLM
C. TLS
D. SSL
E. LDAP
A network engineer must migrate a Cisco WSA virtual appliance from one physical host to another physical host by using VMware vMotion. What is a requirement for both physical hosts?
A. The hosts must run Cisco AsyncOS 10.0 or greater.
B. The hosts must run different versions of Cisco AsyncOS.
C. The hosts must have access to the same defined network.
D. The hosts must use a different datastore than the virtual appliance.
Which solution is made from a collection of secure development practices and guidelines that developers must follow to build secure applications?
A. AFL
B. Fuzzing Framework
C. Radamsa
D. OWASP
What is the term for the concept of limiting communication between applications or containers on the same node?
A. container orchestration
B. software-defined access
C. microservicing
D. microsegmentation
What is the recommendation in a zero-trust model before granting access to corporate applications and resources?
A. to use multifactor authentication
B. to use strong passwords
C. to use a wired network, not wireless
D. to disconnect from the network when inactive
In which two customer environments is the Cisco WSAv connector traffic direction method selected? (Choose two.)
A. Customer owns ASA Appliance and Virtual Form Factor is required.
B. Customer does not own Cisco hardware and needs Explicit Proxy.
C. Customer owns ASA Appliance and SSL Tunneling is required.
D. Customer needs to support roaming users.
E. Customer does not own Cisco hardware and needs Transparent Redirection (WCCP).
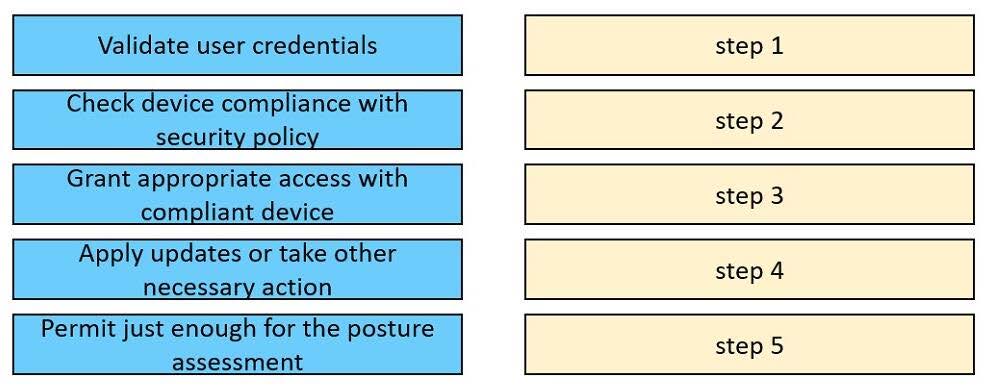
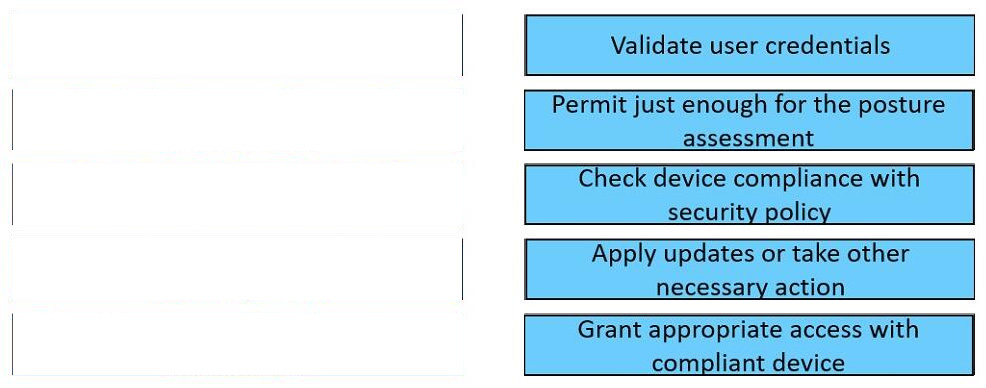
DRAG DROP
Drag and drop the posture assessment flow actions from the left into a sequence on the right.
Select and Place: