312-50 Online Practice Questions and Answers
Stephanie works as a records clerk in a large office building in downtown Chicago. On Monday, she went to a mandatory security awareness class (Security5) put on by her company's IT department. During the class, the IT department informed all employees that everyone's Internet activity was thenceforth going to be monitored.
Stephanie is worried that her Internet activity might give her supervisor reason to write her up, or worse get her fired. Stephanie's daily work duties only consume about four hours of her time, so she usually spends the rest of the day surfing the web. Stephanie really enjoys surfing the Internet but definitely does not want to get fired for it.
What should Stephanie use so that she does not get in trouble for surfing the Internet?
A. Cookie Disabler
B. Stealth Anonymizer
C. Stealth Firefox
D. Stealth IE
"Testing the network using the same methodologies and tools employed by attackers" Identify the correct terminology that defines the above statement.
A. Vulnerability Scanning
B. Penetration Testing
C. Security Policy Implementation
D. Designing Network Security
Every company needs a formal written document which spells out to employees precisely what they are allowed to use the company's systems for, what is prohibited, and what will happen to them if they break the rules. Two printed copies of the policy should be given to every employee as soon as possible after they join the organization. The employee should be asked to sign one copy, which should be safely filed by the company. No one should be allowed to use the company's computer systems until they have signed the policy in acceptance of its terms. What is this document called?
A. Information Audit Policy (IAP)
B. Information Security Policy (ISP)
C. Penetration Testing Policy (PTP)
D. Company Compliance Policy (CCP)
What is the correct order of steps in CEH System Hacking Cycle?
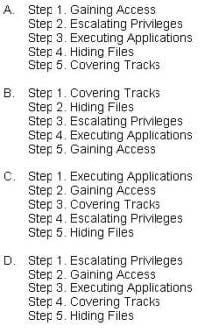
A. Option A
B. Option B
C. Option C
D. Option D
What do you call a pre-computed hash?
A. Sun tables
B. Apple tables
C. Rainbow tables
D. Moon tables
Microsoft Authenticode technology is used for:
A. Digital Signing Activex controls
B. Digitally signing SSL Certificates
C. Digitally Signing JavaScript Files
D. Digitally Signing Java Applets
Angela is trying to access an education website that requires a username and password to login. When Angela clicks on the link to access the login page, she gets an error message stating that the page can't be reached. She contacts the website's support team and they report that no one else is having any issues with the site. After handing the issue over to her company's IT department, it is found that the education website requires any computer accessing the site must be able to respond to a ping from the education's server. Since Angela's computer is behind a corporate firewall, her computer can't ping the education website back.
What ca Angela's IT department do to get access to the education website?
A. Change the IP on Angela's Computer to an address outside the firewall
B. Change the settings on the firewall to allow all incoming traffic on port 80
C. Change the settings on the firewall all outbound traffic on port 80
D. Use a Internet browser other than the one that Angela is currently using
A remote user tries to login to a secure network using Telnet, but accidently types in an invalid user name or password. Which responses would NOT be preferred by an experienced Security Manager? (multiple answer)
A. Invalid Username
B. Invalid Password
C. Authentication Failure
D. Login Attempt Failed
E. Access Denied
Which of the following LM hashes represent a password of less than 8 characters? (Select 2)
A. BA810DBA98995F1817306D272A9441BB
B. 44EFCE164AB921CQAAD3B435B51404EE
C. 0182BD0BD4444BF836077A718CCDF409
D. CEC52EB9C8E3455DC2265B23734E0DAC
E. B757BF5C0D87772FAAD3B435B51404EE
F. E52CAC67419A9A224A3B108F3FA6CB6D
Exhibit
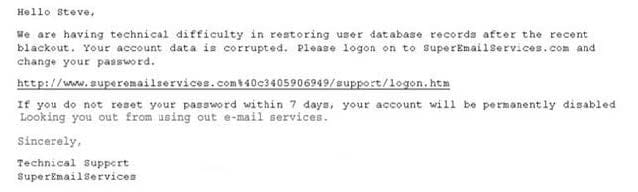
You receive an e-mail with the message displayed in the exhibit. From this e-mail you suspect that this message was sent by some hacker since you have using their e- mail services for the last 2 years and they never sent out an e-mail as
this. You also observe the URL in the message and confirm your suspicion about 340590649. You immediately enter the following at the Windows 2000 command prompt.
ping 340590649
You get a response with a valid IP address. What is the obstructed IP address in the e-mail URL?
A. 192.34.5.9
B. 10.0.3.4
C. 203.2.4.5
D. 199.23.43.4
What hacking attack is challenge/response authentication used to prevent?
A. Replay attacks
B. Scanning attacks
C. Session hijacking attacks
D. Password cracking attacks
SNMP is a protocol used to query hosts, servers, and devices about performance or health status data. This protocol has long been used by hackers to gather great amount of information about remote hosts.
Which of the following features makes this possible? (Choose two)
A. It used TCP as the underlying protocol.
B. It uses community string that is transmitted in clear text.
C. It is susceptible to sniffing.
D. It is used by all network devices on the market.
You are scanning into the target network for the first time. You find very few conventional ports open. When you attempt to perform traditional service identification by connecting to the open ports, it yields either unreliable or no results. You are unsure of what protocols are being used. You need to discover as many different protocols as possible. Which kind of scan would you use to do this?
A. Nmap with the sO (Raw IP packets) switch
B. Nessus scan with TCP based pings
C. Nmap scan with the sP (Ping scan) switch
D. Netcat scan with the u e switches
What are two things that are possible when scanning UDP ports? (Choose two.
A. A reset will be returned
B. An ICMP message will be returned
C. The four-way handshake will not be completed
D. An RFC 1294 message will be returned
E. Nothing
Lori has just been tasked by her supervisor conduct vulnerability scan on the corporate network. She has been instructed to perform a very thorough test of the network to ensure that there are no security holes on any of the machines. Lori's company does not own any commercial scanning products, so she decides to download a free one off the Internet. Lori has never done a vulnerability scan before, so she is unsure of some of the settings available in the software she downloaded. One of the option is to choose which ports that can be scanned. Lori wants to do exactly what her boos has told her, but she does not know ports should be scanned.
If Lori is supposed to scan all known TCP ports, how many ports should she select in the software?
A. 65536
B. 1024
C. 1025
D. Lori should not scan TCP ports, only UDP ports
