312-39 Online Practice Questions and Answers
Which of the following formula represents the risk?
A. Risk = Likelihood × Severity × Asset Value
B. Risk = Likelihood × Consequence × Severity
C. Risk = Likelihood × Impact × Severity
D. Risk = Likelihood × Impact × Asset Value
Juliea a SOC analyst, while monitoring logs, noticed large TXT, NULL payloads. What does this indicate?
A. Concurrent VPN Connections Attempt
B. DNS Exfiltration Attempt
C. Covering Tracks Attempt
D. DHCP Starvation Attempt
An organization is implementing and deploying the SIEM with following capabilities.
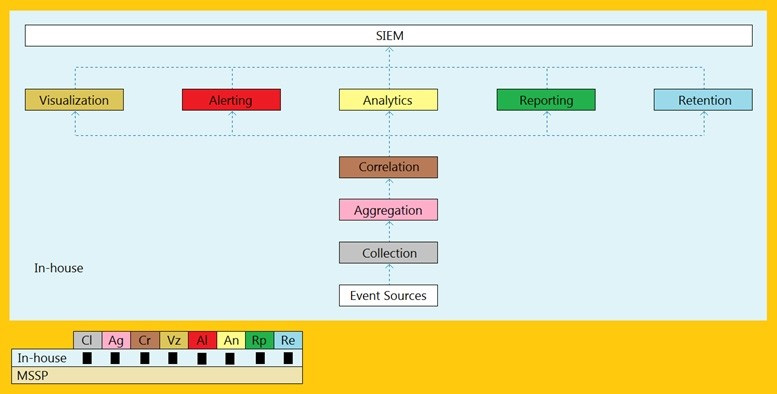
What kind of SIEM deployment architecture the organization is planning to implement?
A. Cloud, MSSP Managed
B. Self-hosted, Jointly Managed C. Self-hosted, Self-Managed
D. Self-hosted, MSSP Managed
Which of the following attack can be eradicated by filtering improper XML syntax?
A. CAPTCHA Attacks
B. SQL Injection Attacks
C. Insufficient Logging and Monitoring Attacks
D. Web Services Attacks
Which of the following attack can be eradicated by using a safe API to avoid the use of the interpreter entirely?
A. Command Injection Attacks
B. SQL Injection Attacks
C. File Injection Attacks
D. LDAP Injection Attacks
Which of the following formula represents the risk levels?
A. Level of risk = Consequence x Severity
B. Level of risk = Consequence x Impact
C. Level of risk = Consequence x Likelihood
D. Level of risk = Consequence x Asset Value
Which of the following Windows Event Id will help you monitors file sharing across the network?
A. 7045
B. 4625
C. 5140
D. 4624
Identify the type of attack, an attacker is attempting on www.example.com website.
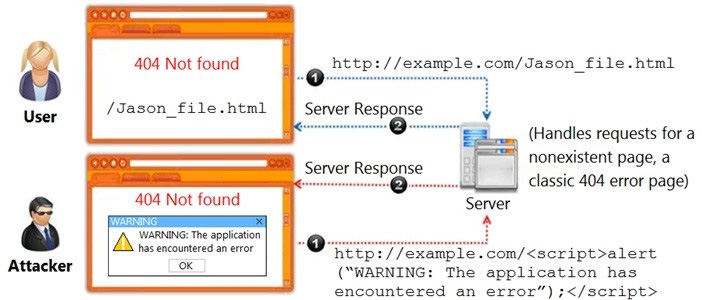
A. Cross-site Scripting Attack
B. Session Attack
C. Denial-of-Service Attack
D. SQL Injection Attack
What type of event is recorded when an application driver loads successfully in Windows?
A. Error
B. Success Audit
C. Warning
D. Information
What does the Security Log Event ID 4624 of Windows 10 indicate?
A. Service added to the endpoint
B. A share was assessed
C. An account was successfully logged on
D. New process executed
What does the HTTP status codes 1XX represents?
A. Informational message
B. Client error
C. Success
D. Redirection
Which of the following contains the performance measures, and proper project and time management details?
A. Incident Response Policy
B. Incident Response Tactics
C. Incident Response Process
D. Incident Response Procedures
Which of the following tool can be used to filter web requests associated with the SQL Injection attack?
A. Nmap
B. UrlScan
C. ZAP proxy
D. Hydra
Emmanuel is working as a SOC analyst in a company named Tobey Tech. The manager of Tobey Tech recently recruited an Incident Response Team (IRT) for his company. In the process of collaboration with the IRT, Emmanuel just escalated an incident to the IRT.
What is the first step that the IRT will do to the incident escalated by Emmanuel?
A. Incident Analysis and Validation
B. Incident Recording
C. Incident Classification
D. Incident Prioritization
Identify the HTTP status codes that represents the server error.
A. 2XX
B. 4XX
C. 1XX
D. 5XX
