300-915 Online Practice Questions and Answers
DRAG DROP
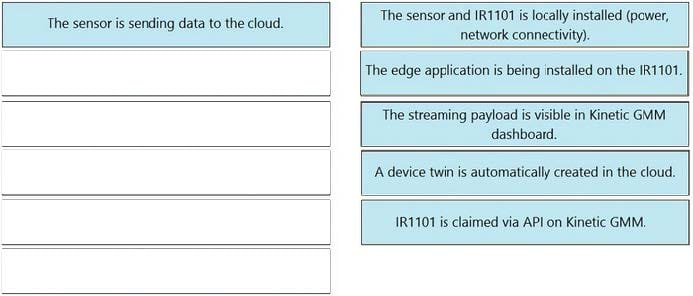
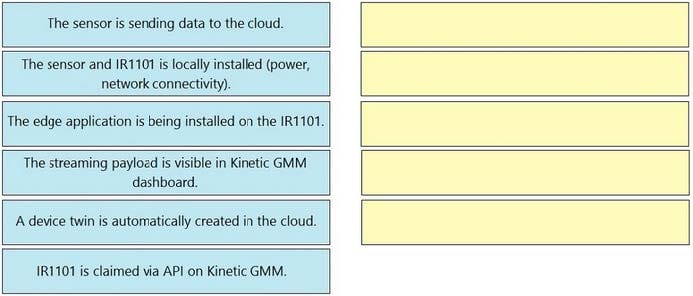
An engineering team developed a solution that gathers data via a proprietary protocol (TCP/IP based) to a IR1101 gateway, which then sends the data to the cloud. Drag and drop the action steps from the left into the correct order on the right to get this solution to operate. Not all options are used.
Select and Place:
DRAG DROP
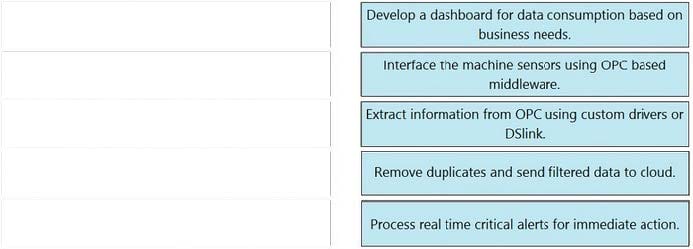
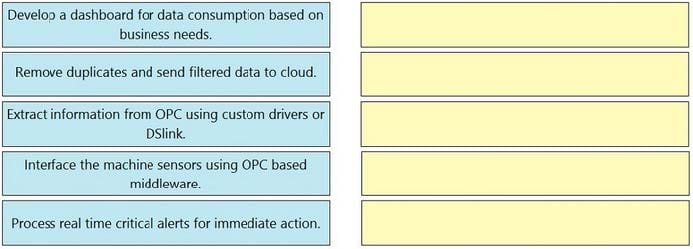
Drag and drop the tasks from the left into the correct order on the right for transporting data from sensors to the cloud, in order to extract the machine data and use the cloud-based analytics for predictive maintenance.
Select and Place:
When trying to subscribe to an MQTT broker on the internet, the MQTT client is on a private subnet and must be NATed to reach the public broker.
What is the expected outcome when this configuration is in place?
A. The client periodically reconnects to the default gateway.
B. The client connects only once using the PENDING message to the broker.
C. The client periodically reconnects to the broker over the NAT connection.
D. The client connects only once using the CONNECT massage to the broker.
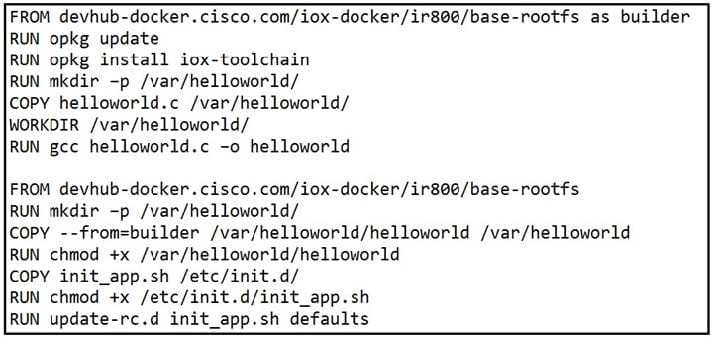
Refer to the exhibit. When a Docker image is built using this Dockerfile, which two statements are valid on Cisco IOx 1.8 and before? (Choose two.)
A. It builds an image that can be executed on all Cisco platforms.
B. It builds a Docker image that cannot be used directly on Cisco IOx.
C. It compiles a "hello world" program in C.
D. It creates two separate images.
E. It builds an IOx package that can be deployed directly.
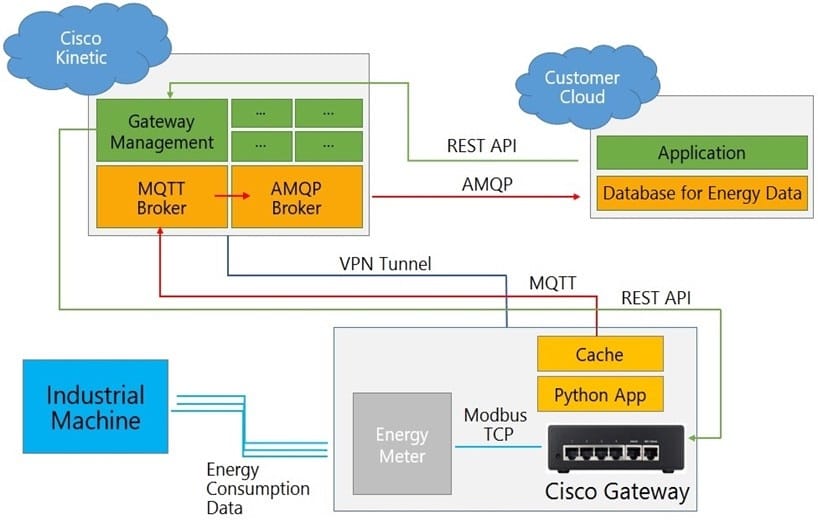
Refer to the exhibit. Which two statements about data flow are true? (Choose two.)
A. Another AMQP broker should be implemented on the customer cloud.
B. Instead of AMQP, MQTT should be used for compatibility issues in a cloud-to-cloud connection.
C. A VPN tunnel is not necessary because the MQTT payload is encrypted by default.
D. The gateway must stay constantly connected to the Kinetic cloud to avoid blank data sets, even when using caching functions.
E. The Python application could use the paho-mqtt library.
What is a major difference of MQTT in terms of design compared to AMQP?
A. MQTT requires more bandwidth.
B. MQTT has very low overhead.
C. MQTT has more advanced routing features for messages.
D. MQTT provides routing based on headers.
Which two statements about how to provision and manage data originators in a cloud environment are true? (Choose two.)
A. The provisioning of digital identities is the responsibility of the data originators.
B. Cloud providers offer services for automated device provisioning, which allows the lifecycle of the cloud-representation for data originators to be managed.
C. Cloud providers offer application programming interfaces, which allow a programmatic provisioning of data originators.
D. There is no need to provision and manage access for data originators in the cloud.
E. The access to public clouds must be configured and managed manually.
A network is being configured for an Ethernet-connected sensor. The sensor fails to send data to the configured destination. The IP address of the sensor can be pinged from a laptop on the same subnet. When a different subnet is used, the sensor cannot be reached, but other clients on the same subnet are still accessible.
What are two reasons for the connectivity problem? (Choose two.)
A. wrong DNS server on the sensor
B. wrong subnet mask on your laptop
C. wrong default gateway on the sensor
D. wrong default gateway on your laptop
E. wrong subnet mask on the sensor
Where are edge data services typically instantiated?
A. at the edge of network
B. in the cloud
C. in the data center
D. in a private cloud
Which two data sources are used with a visualization tool such as Grafana? (Choose two.)
A. Microsoft Power BI
B. Kibana
C. InfluxDB
D. Elasticsearch
E. Tableau
A customer is deploying sensors with Cisco IR829 routers in moving trucks to continuously monitor the health of engines using a cloud application.
Which data extraction and processing strategy is best suited in this environment?
A. No need to store data locally, upload in real time to the cloud for processing.
B. Generate local alerts and create reports at the edge, and upload to the cloud at the end of the day.
C. Use the store and forward mechanism to upload the information at the earliest to cloud.
D. Ensure that data is stored for a longer duration locally and upload to the cloud every week.
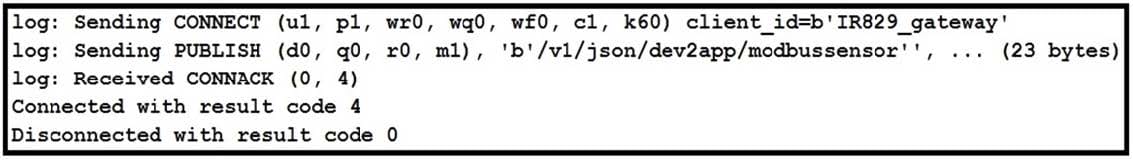
Refer to the exhibit. Based on the MQTT client output, which action should be taken so that the connection to the broker can be established?
A. Change the username/password.
B. Open port 1883 on the network firewall.
C. Change the IP address of the broker.
D. Add the certificate.
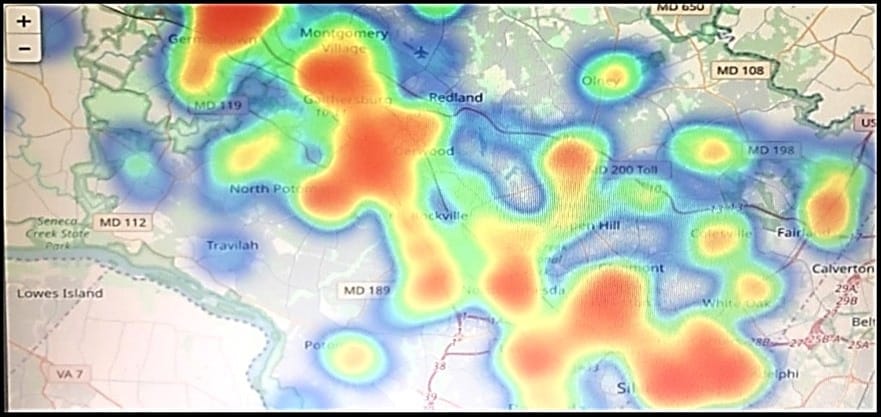
Refer to the exhibit. Which two statements are true? (Choose two.)
A. That is a heatmap projected on top of a geographic map.
B. That is a treemap projected on top of a geographic map.
C. The color red usually stands for lower values and the color blue usually stands for higher values.
D. Another suitable visualization technique for this image would be line graphs.
E. The color blue usually stands for lower values and the color red usually stands for higher values.
An IOx application is installed via Local Manager. Every time the application is started, it instantly stops.
Which troubleshooting steps should be taken?
A. There is something wrong with the application code itself.
B. Check the startup and entrypoint parameters.
C. Give the IOx application more CPU units.
D. Check local IOx settings, especially the network settings.
In a secure software development lifecycle process, what must be created as soon as the architecture is in place?
A. integration plan
B. test plan
C. functional specification document
D. threat modeling